Revelo v0.4 Released
I got some feedback from some folks as well as trying out some new methods to improve Revelo. This version now includes the following:
- Added ability to choose the direction of the replacement (e.g. top-down or bottom-up).
- Added ability to choose action method (e.g. textarea, document.write, or alert) and modified the other choices as a result.
- Implemented a method to redirect a variable to a particular action.

Most of the feedback and questions I've been getting recently was around "how do I deobfuscate Blackhole?" The Blackhole author(s) continually modify their obfuscation methods so I'm not sure which version are giving some of you a hard time. Other methods in Revelo work but I wanted to focus on the new "redirect variable" method.
Remember, if you are playing with live malicious scripts like Blackhole, use Revelo in a virtual machine! While Revelo won't redirect you to a malicious site (by default), it will execute exploit code which could launch Java that will redirect you.
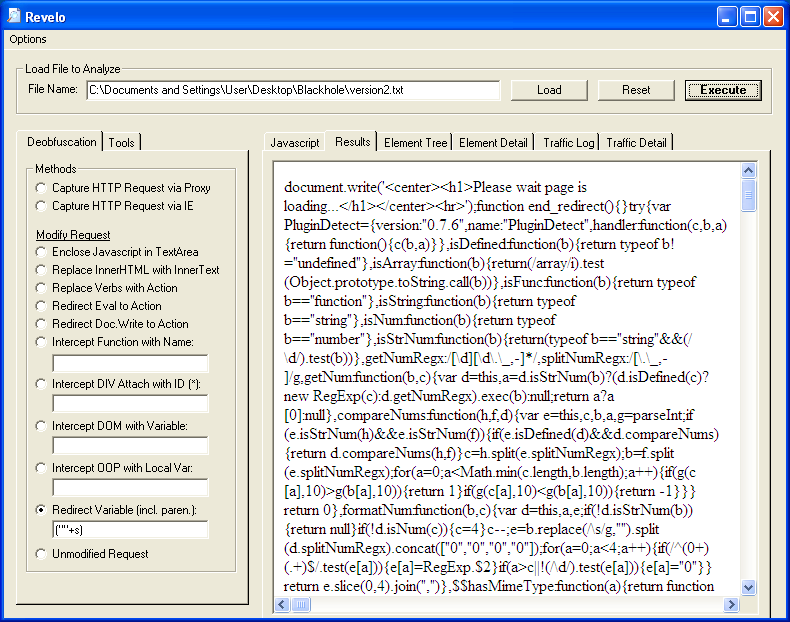
Version #1
1. Load up the obfuscated script. Up near the top, you will see "e(c);". The "e" variable holds "eval" and the "c" variable holds the exploit code. Select the "Redirect Variable" method. Enter the "c" variable as well as the parenthesis around it.
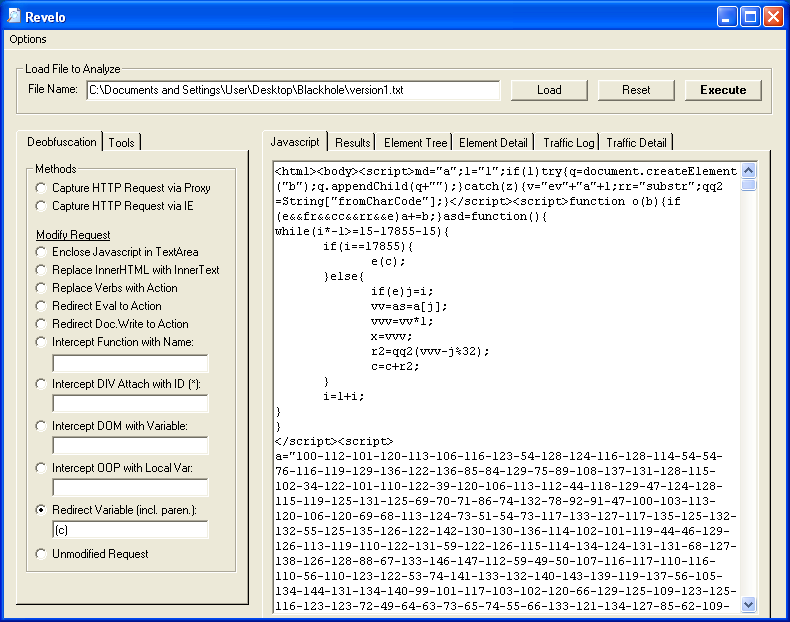
2. Click on "Execute" then go to the "Results "tab.
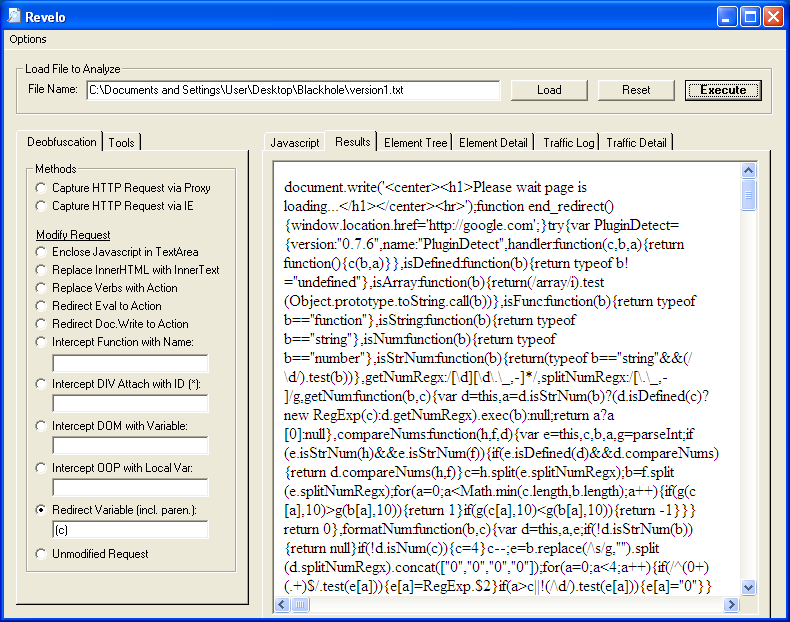
Version #2
1. Load up the obfuscation script and check out the bottom part of the script. You can see "e(""+s);" at the end. This time the "s" variable contains the exploit code. Select the "Redirect Variable" method once again but this time we want to enter (""+s).
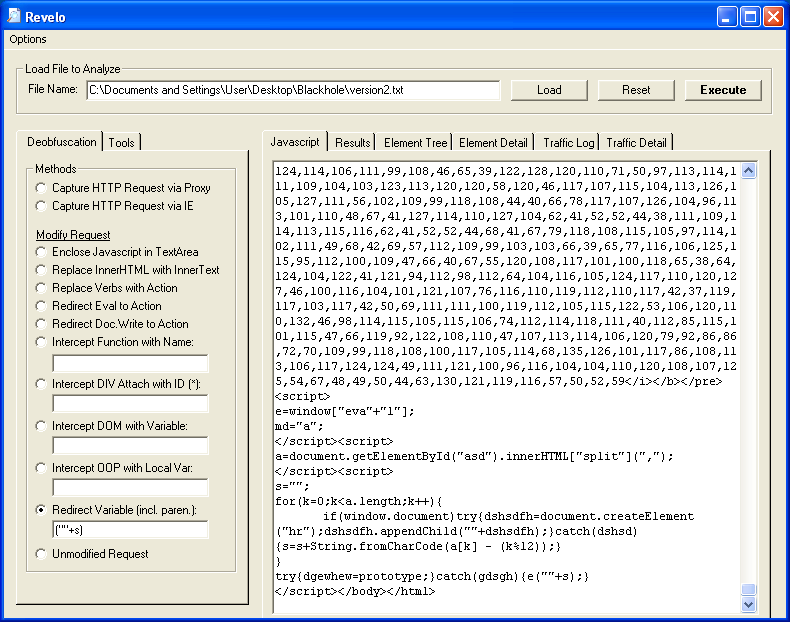
2. Click on "Execute" then go to the "Results "tab.