Making Wacky Redirect Scripts - Part I
A couple of months ago, I created a program that would analyze Javascript code that obfuscates redirection to malicious websites. I come across a lot of these kinds of scripts so this program will make it easier and faster for me to analyze it. I’m testing it now by throwing a bunch of obfuscated code at it to see how it fares. It’s working rather well but I decided to make my own “malicious” scripts to see if I could evade it.
The challenge I posed to myself was to make the redirection scripts look harmless, try out some techniques, and come up with new methods to see if my program could properly analyze it. All of these scripts redirect the browser to Google and were built to work on Firefox.
I’m not breaking new ground here and there’s probably another dozen or so techniques that I haven’t included that people way smarter than me have figured out (please share if you are one of them). The dozen or so scripts I came up with are very simple and straightforward. I didn’t employ any serious obfuscation or countermeasures, in fact, these are brain-dead simple to analyze/reverse but they are unusual and may give my program a headache while it tries to figure it out.
1. When I analyze a malicious website, I look for obfuscated Javascript which can be visually detected rather quickly. I admit that when I see search engine analytics, AJAX frameworks, etc, I pass them by because they usually aren’t modified to be malicious. But if I can’t find the obvious malicious script then of course I double-back and scrutinize everything.
What I did here was take Google’s advertisement code which can be found on just about every website out there and modified it in such a way as to redirect the user to Yahoo.com even though it clearly shows Google’s URL. [This is the only script that redirects to Yahoo.com, the rest redirects to Google.com.]

This script dynamically replaces the HTML body with the HTML code from the Javascript. The key to this is the variable “Google_Ad_Client” which holds a bunch of numbers that when read in three at a time (decimal values) eventually converts Google’s URL to Yahoo’s URL.
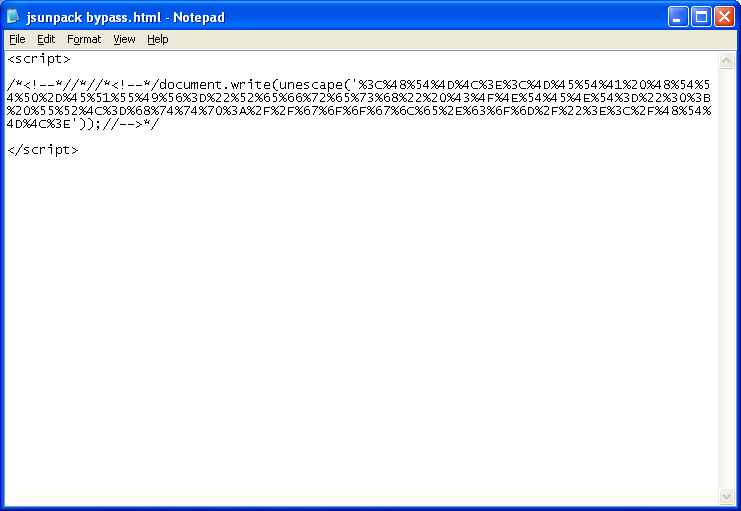
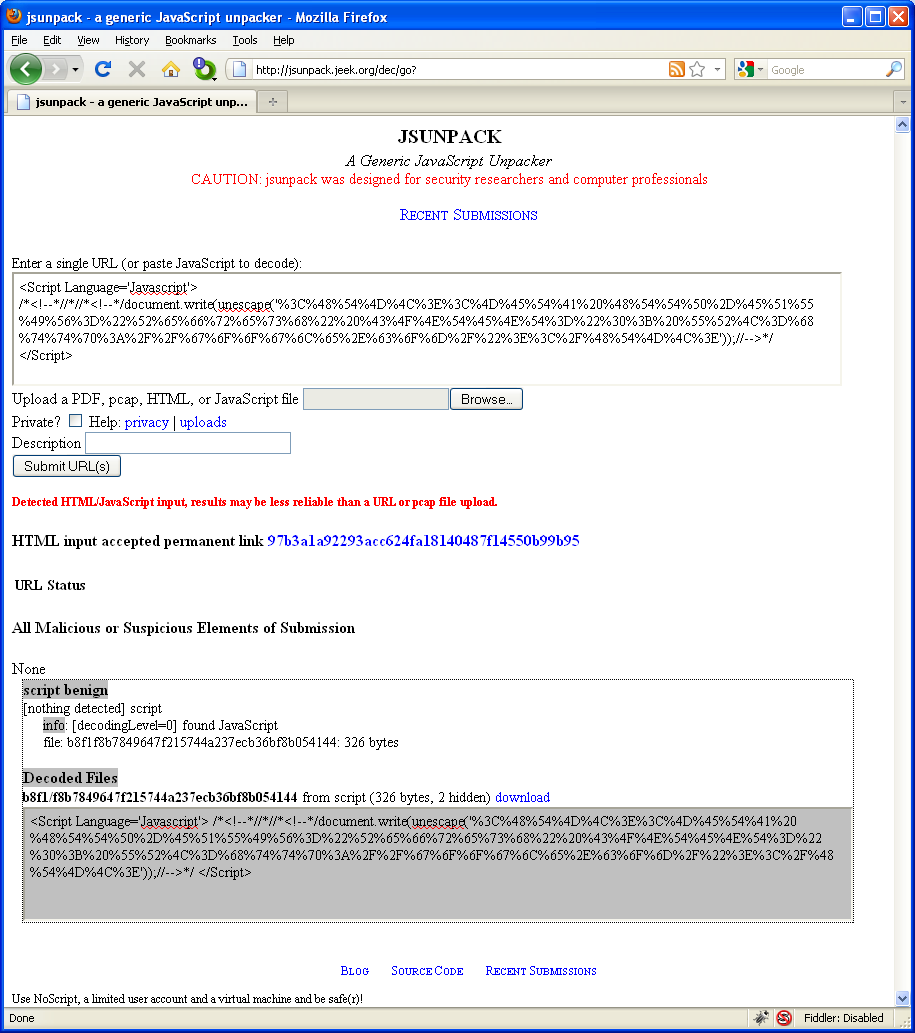
2. JSUnpack is a very good online tool that analyzes Javascript. I came up with several bypass methods some time ago and I’ll try to use the same techniques against my tool. Here’s one such method.
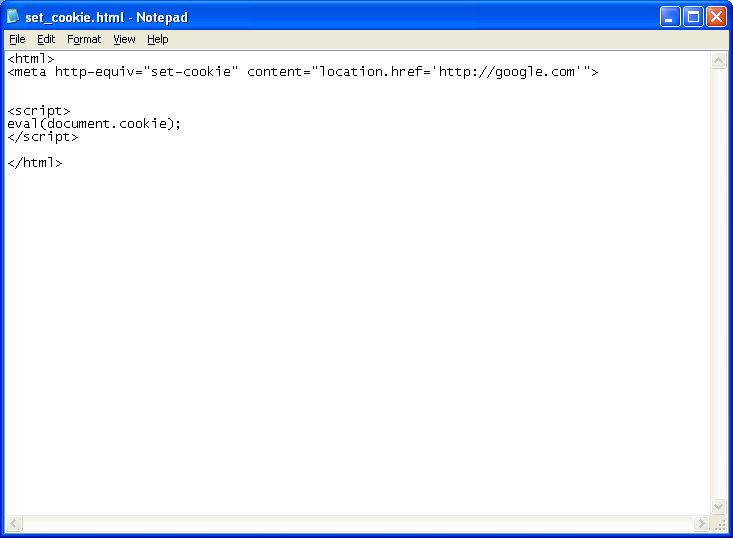
3. This technique uses HTML to set a cookie that has the redirect script as its content. An external Javascript file is then used to eval the cookie (I’ve included it in the webpage to make it easier to see).
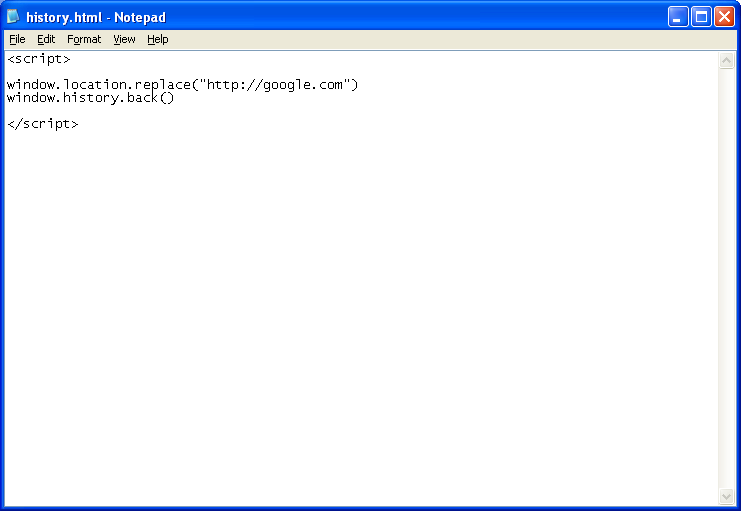
4. Just like the cookie method above, I’m sure this has been used numerous times before. Here, I replace the browser location history with a URL I want the browser to visit then call it.
5. Using Push and Unshift methods, I formed a redirect in an Array object. I basically start at the center then prepend (push) and append (unshift) characters to form the final script. I also threw in some Pops and Shifts so that the final script formation wouldn’t be that straightforward.
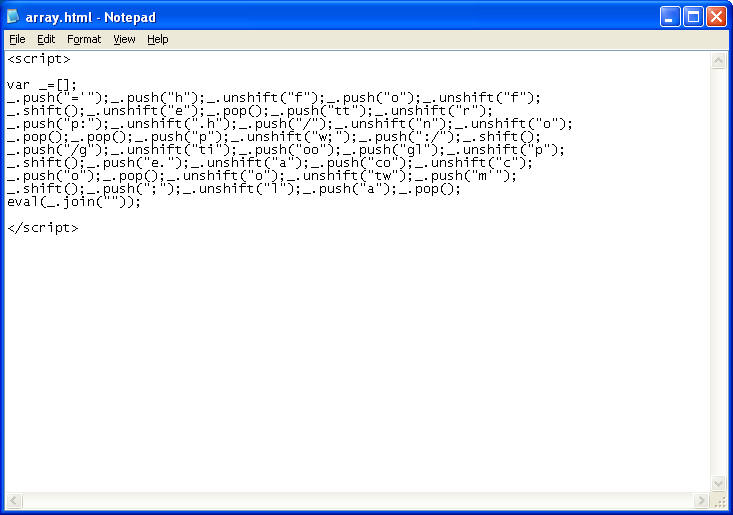
6. Okay, now I’m just getting silly. A common characteristic of obfuscated Javascript is garbled text (random characters) or a long string of numbers. As a challenge to myself, I thought I would try to make a redirect without using the word “script”, random characters, or any numbers.
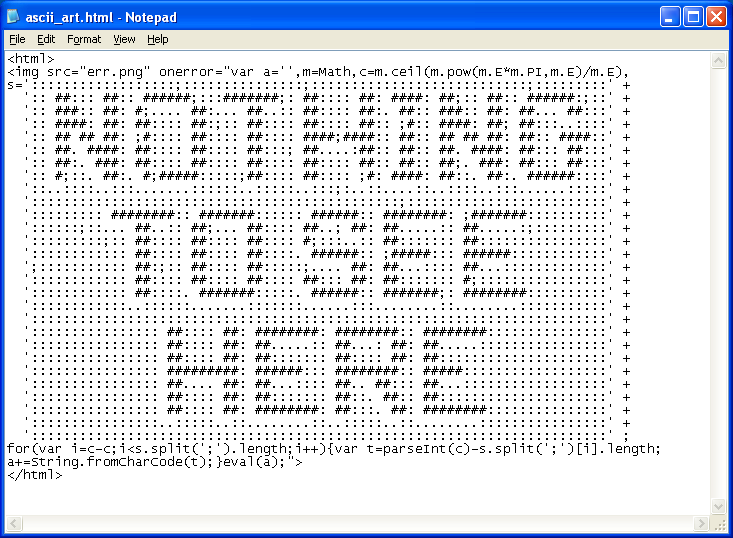
In this example, I used the onerror function to run my Javascript code that counts the characters between semi-colons (“;”) to construct code that redirects the user to Google.

