KaiXin Exploit and Tool Update
Just a quick follow-up of an in-depth article from Denis Laskov which you can read here. Denis kindly provided me with the pack and I noticed this strange text file was getting downloaded:
This sort of looks like an EXE file structure so I imported the file as hex, truncated it so I could do an XOR search for "MZ" quickly.

Now I can load up the entire file then XOR it with the key, 0xA2 but something doesn't look right.

All the 0xA2 values should actually be 0x00s. The KaiXin author(s) only encoded non-0x00 values. So I check this box and do it again.
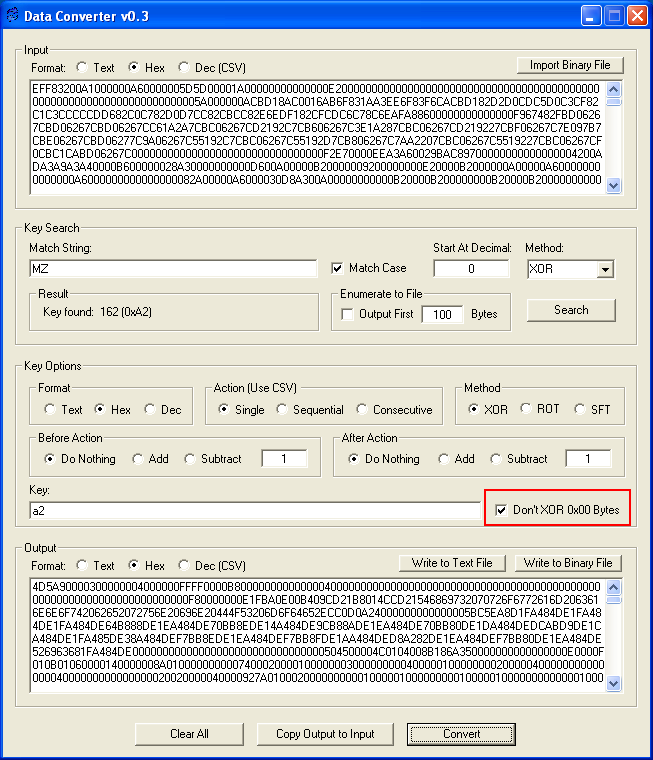
Okay, that looks better. Now let's write it out to a binary file then check it against VirusTotal. Here are the results:
MD5: a2528ea962ce621b3b0f190a1d1e904eVT: 25 / 43
