Excel VBA Loads DLL into Itself
A security researcher, Mahendra K R, reached out to share a sample with me recently. The researcher was trying to use the CMD Watcher tool but it didn't seem to be working.
CMD Watcher monitors the arguments passed to CMD so you can see what's being called. This can be very helpful when trying to analyze VBA macros that execute PowerShell, for example. You don't have to deobfuscate the VBA macro, you just run the tool and watch as PowerShell gets executed along with the deobfuscated script.
In this case, however, nothing gets captured by CMD Watcher so let's have a look at the macro.
Here's your typical maldoc file...

When the VBA script is executed, it starts off here at the UserForm_Initialize subroutine.
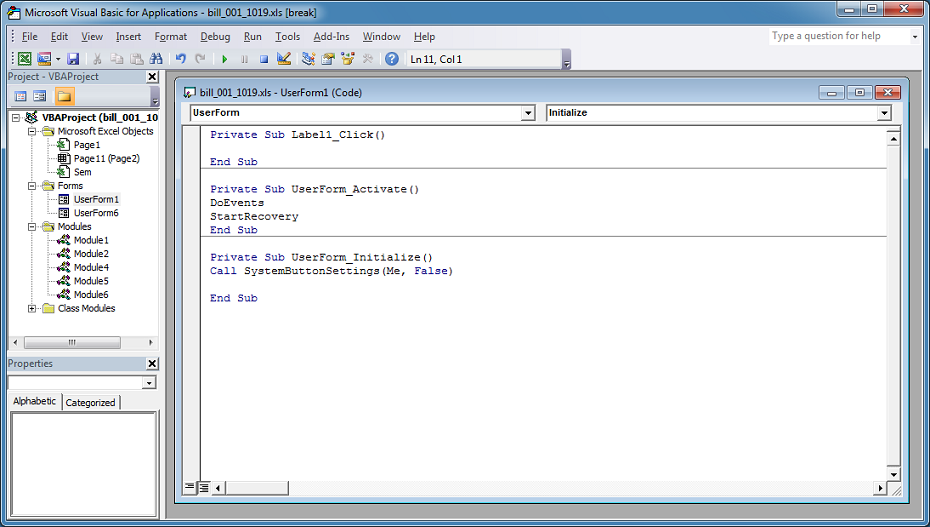
The script then builds the folder locations here.
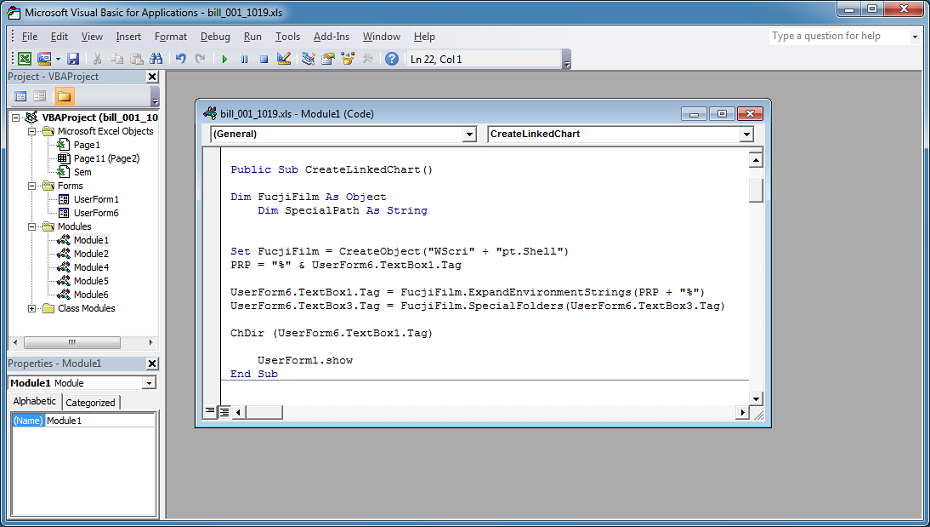
The actual names are pulled from a userform. The textbox's tag field holds the name, "Template", in this case. The other textbox is "Temp".
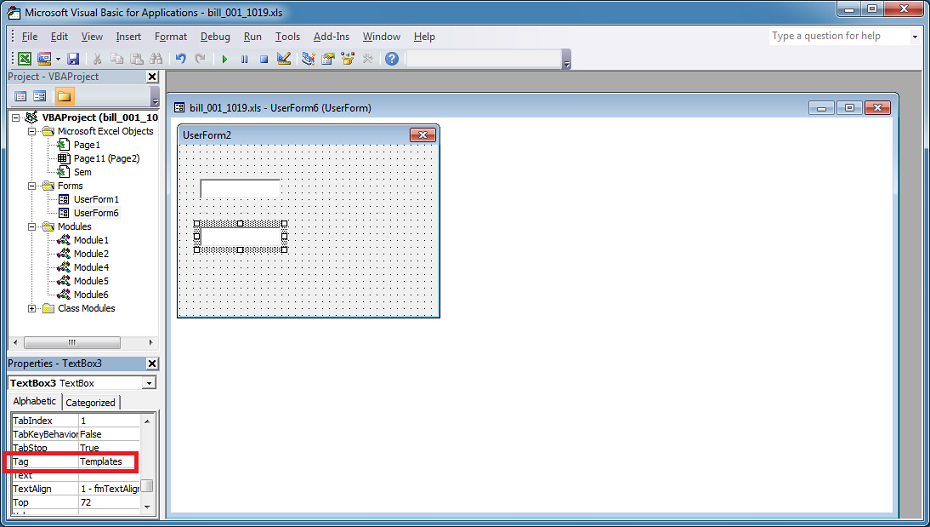
Then it saves the spreadsheet as an .xlsx file in the Temp folder.

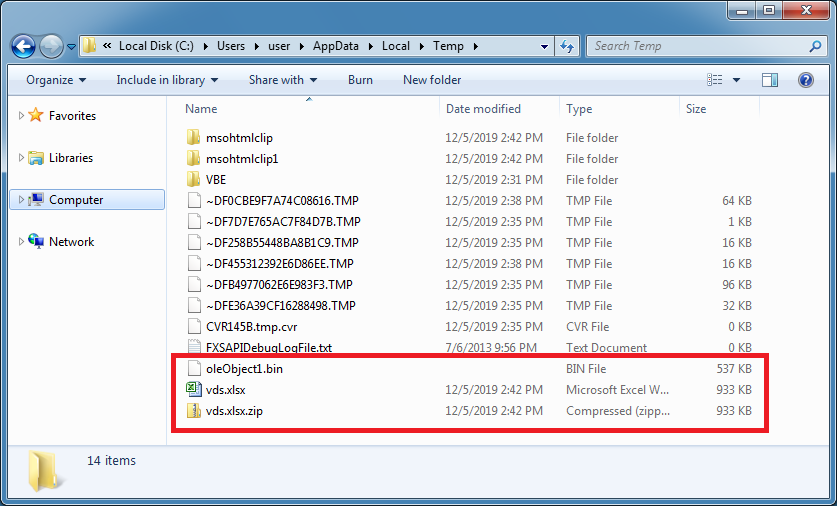
In this section, the script then makes a copy of the .xlsx file as a zip file and unzips the "oleObject1.bin" file.

In the Temp folder, you can see these files at the bottom.
The script then searches the "oleObject1.bin" file for the first three bytes of a PE file (decimal values of 77, 90, 144).
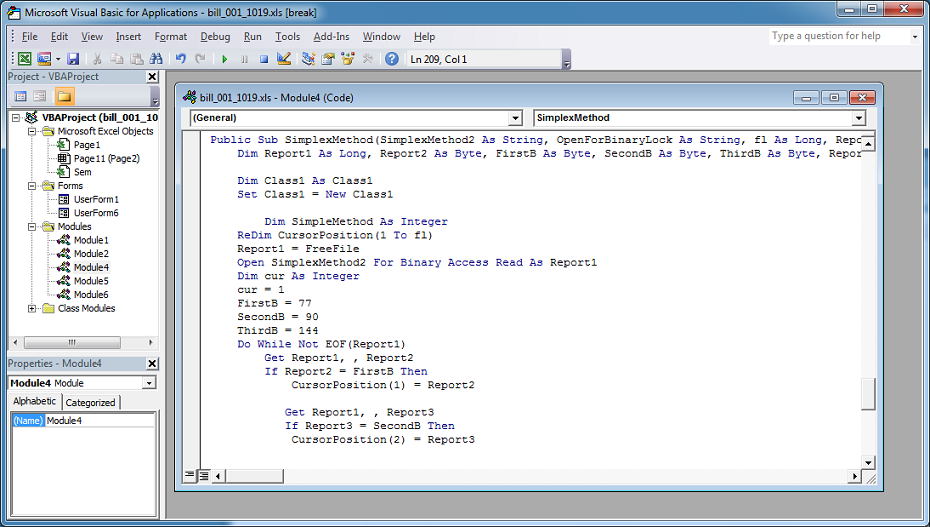
If you hexedit the bin file, you can see that there's a PE file without any obfuscation or encryption.

The PE file is extracted and written out as a DLL file in the user's AppData\Roaming\Microsoft\Windows\Templates folder.

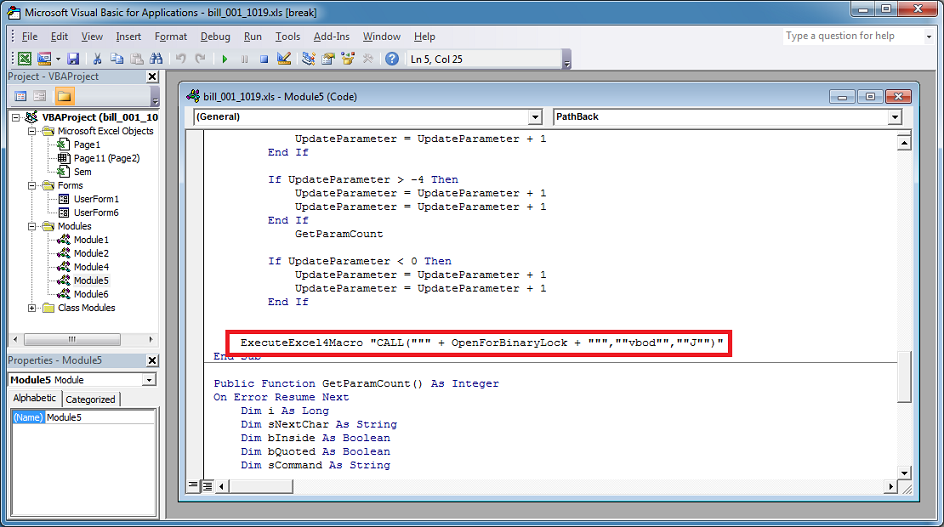
Finally, the script uses the ExecuteExcel4Macro function and executes the DLL file.
Using Process Explorer, you can see that the DLL is loaded in Excel. Note the c2 server on the left.

If the user terminates Excel then the DLL will also be terminated. The attackers must've thought of that so they created this fake progress bar. The progress bar doesn't move and since this takes focus, the user can't quit out of Excel normally. You can press Alt-F4 to close the dialog box, by the way.

I haven't seen anything like this before. It's a straightforward method of running malware without relying on any external programs like CMD, PowerShell, VBScript, etc. And that's why CMD Watcher didn't see anything.
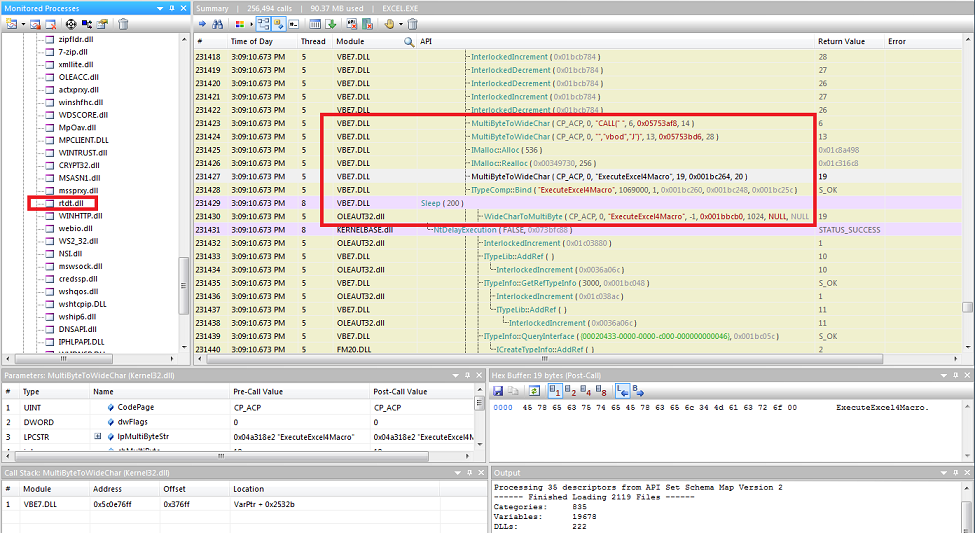
I thought about writing a kind of API monitor but other developers have already done this. I find API Monitor well equipped to handle tasks like this. Here you can see the call and the responsible modules.
File: bill_001_1019.xlsSize: 1.33MBMD5: D255FF12529B0B883609FA67B8126C7CVT: 16 / 59File: rtdt.dllSize: 284KBMD5: DECAE333229D9D2F21C495D1F1C86015VT: 33 / 69
