Deobfuscating the Facebook Spam Script
The latest Facebook spam Javascript code was sent to me. Apparently there are two versions, one was obfuscated while the other wasn’t. Lucky me, I get the obfuscated one!
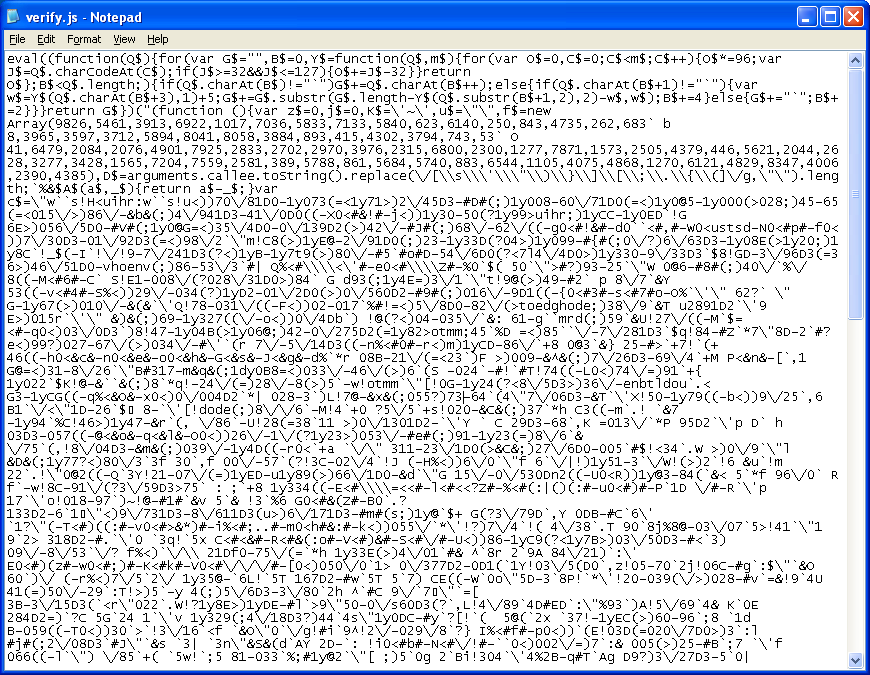
My first thought was “wow, nice obfuscation but should be easy to get around”. Ha, no such luck. The second layer is worst than the first. Do you see the fifth line from the top on the right-hand side? It’s callee!
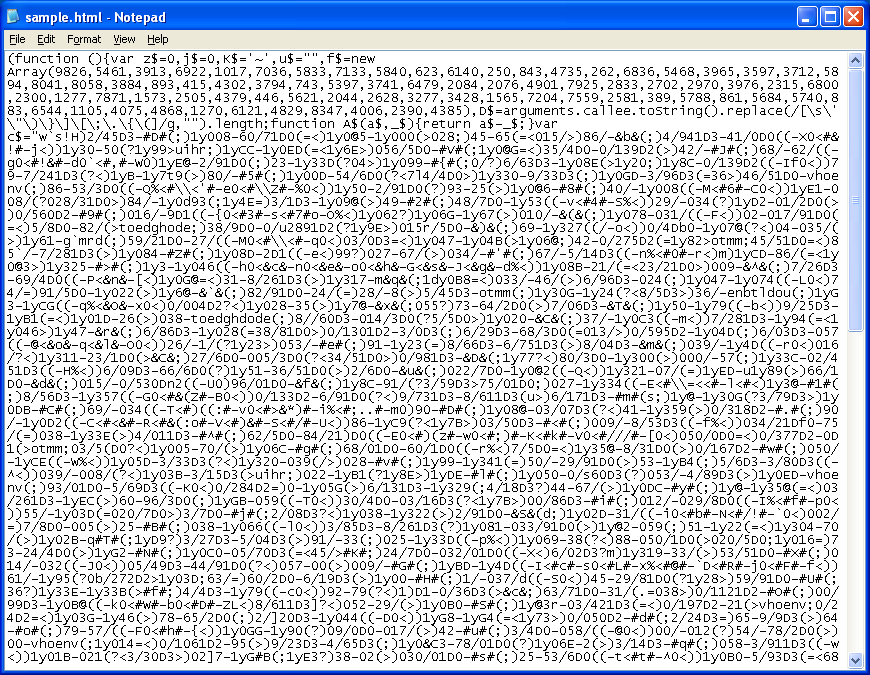
The “callee” technique is a kind of booby trap for Javascript reversers. You can read about the technique from various SANS diaries and others. The callee function reads in the calling function and in this case, the code strips away the special characters, counts the length, and then uses the value for decryption. If you add or delete any character in the function (e.g. changing “eval” to “alert”, the length changes and the decryption fails. This is a basic form of anti-reversing.
There are a couple of techniques to get around this. SANS and others provide the various techniques. One of the easiest to deploy is to add a new function outside of the original one (seen here in the red box).
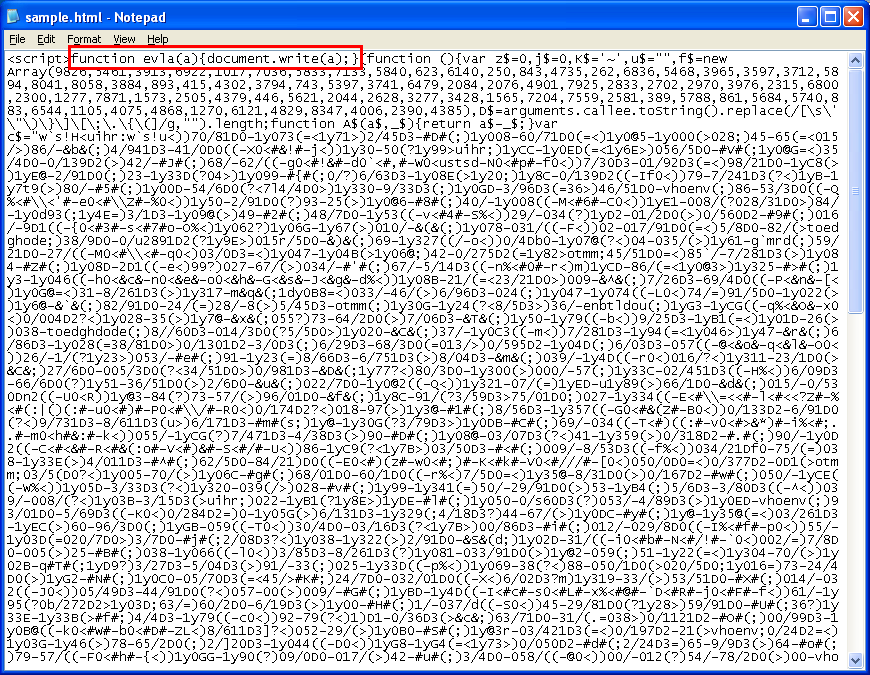
Down at the bottom of the script is an “eval” function. We change that to “evla”. By doing this, we don’t change the length.
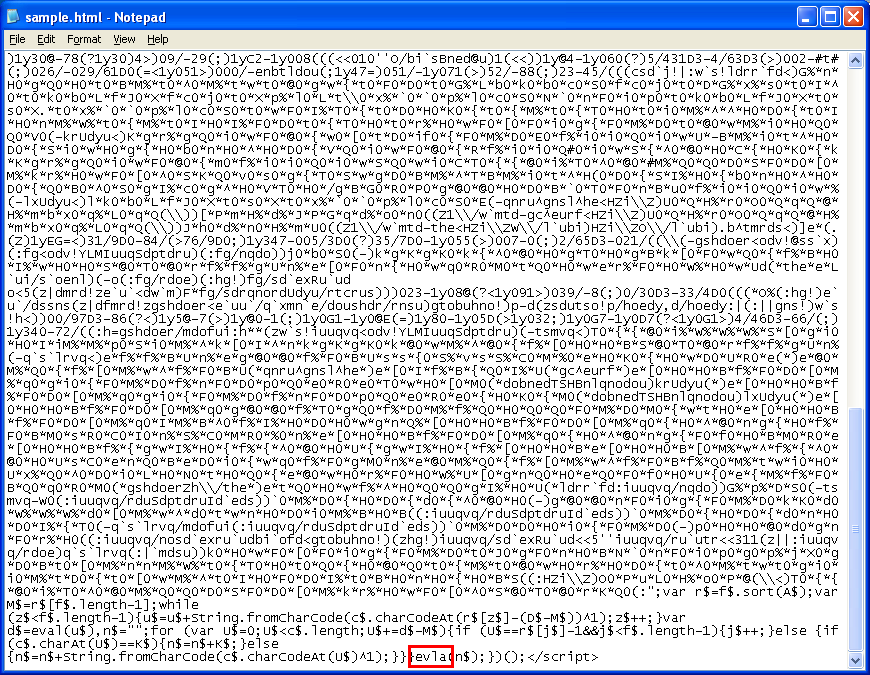
So when the code is executed, the value of n$ gets sent up to the new function we created where we get to see what’s there. Which is….another layer of obfuscated code!
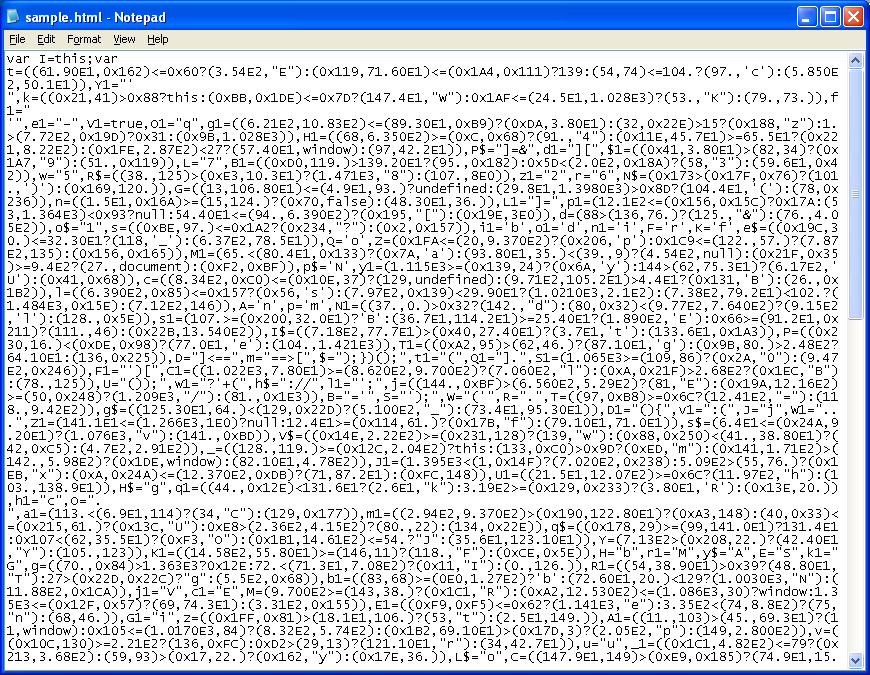
Since there’s no callee function here, we can beautify it. Here we see variables getting loaded up after some tricky conditional statements.
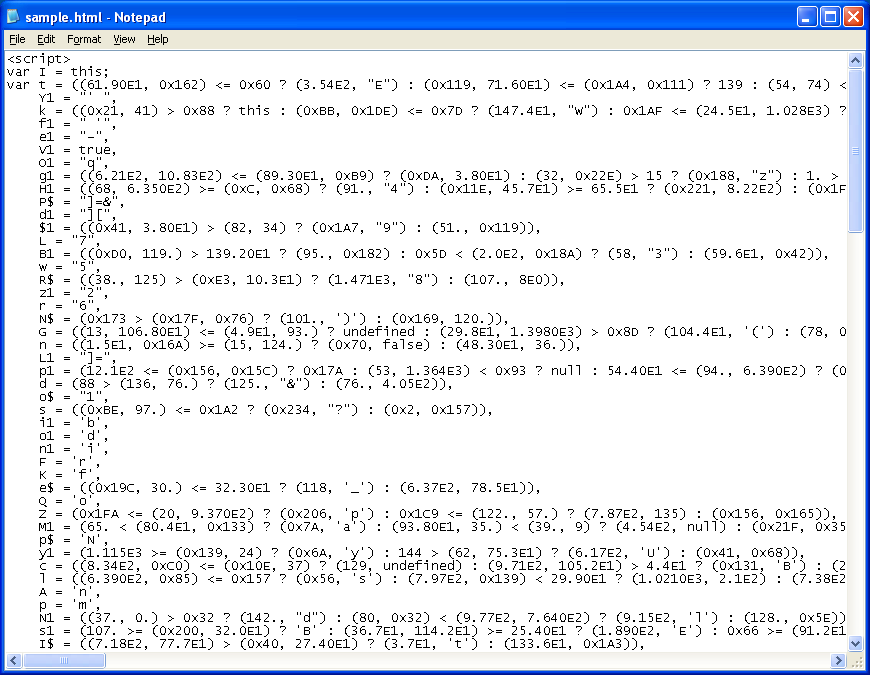
After three layers of heavy obfuscation, we are finally treated with an excerpt of the script that’s causing all the spam.
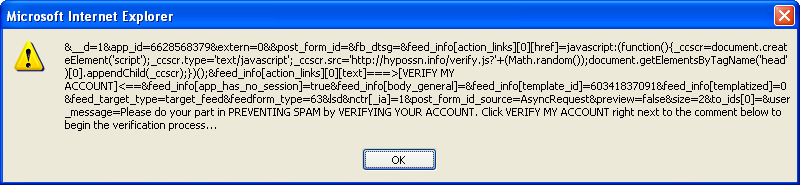
You can see the complete source of the script here: http://pastebin.com/nkBx8GbH

