Deobfuscating PHPJiami
I was sent a PHP script that was protected by PHPJiami which you can find here. PHPJiami is a decent PHP obfuscator that appears to be able to bypass several online deobfuscators. Here's what the script looks like:
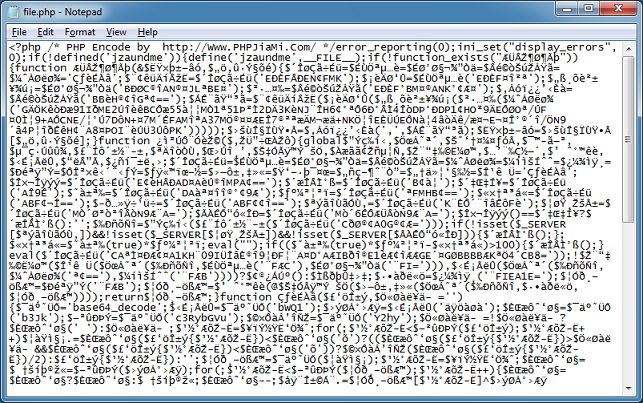
When you run it, you can see what the protected script does.
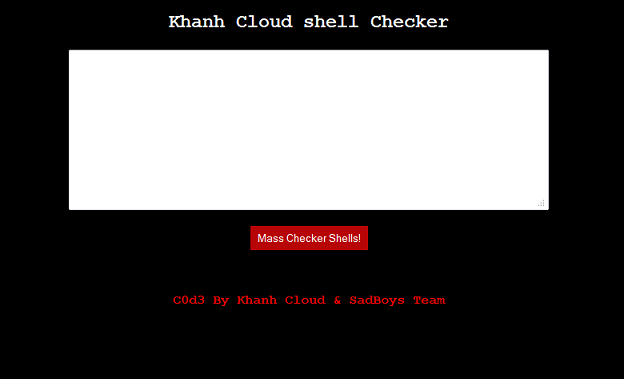
At the top there's a comments section. Let me change the uppercase "P" in "PHP" to lowercase.
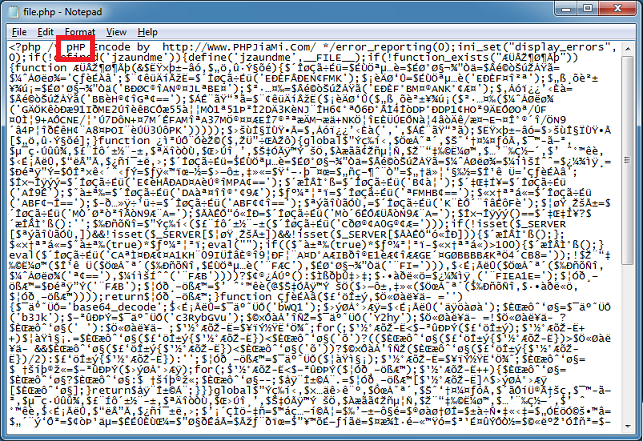
Now when I run the script, nothing happens. This means there's some kind of anti-tampering function in the script.

Let me clean up the script so we can see what it's doing. If you look at the second function, you can see what looks like variable assignments.
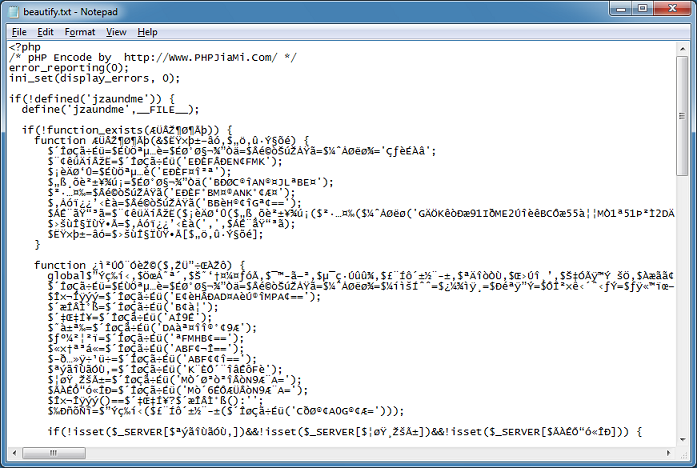
At the bottom of the script, you can see a blob of obfuscated text. This is probably where the prize is.
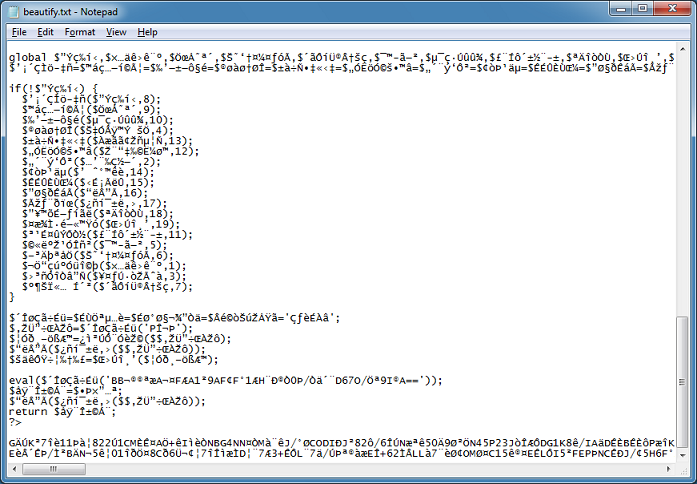
After studying this a bit, I go back up to the second function and echo out the variables to see what they contain (look at the comments). That last line is interesting as it reads a copy of itself.
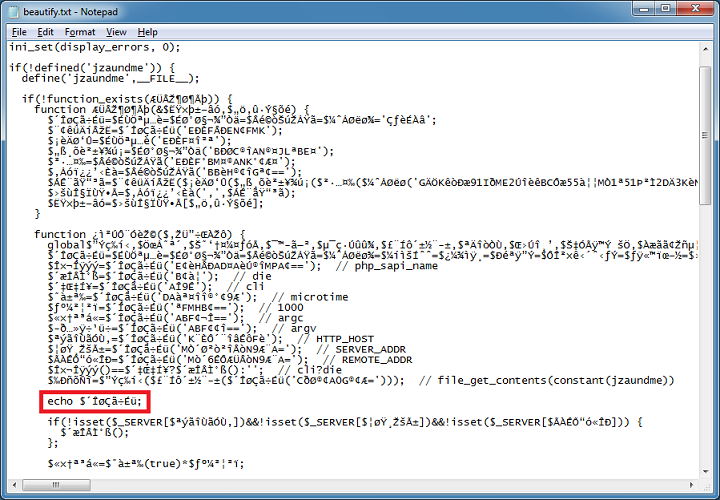
The section right below that has some interesting variables as well. It looks like it's using MD5 to ensure the script isn't modified. If all is good, the blob at the bottom gets uncompressed, rot13'd, etc.
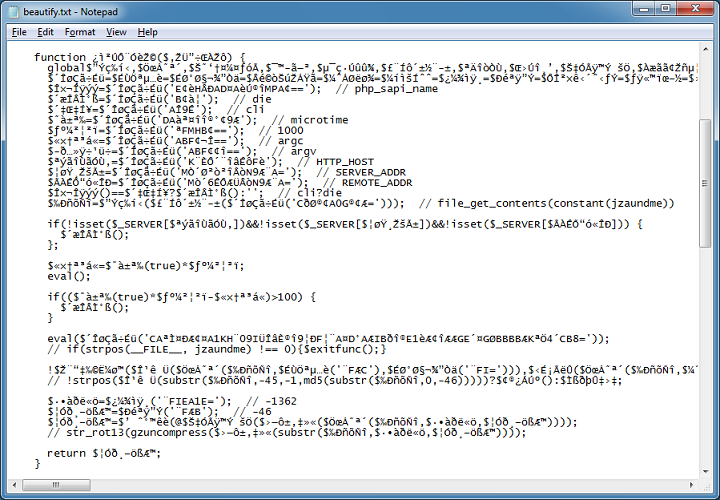
Although I have only have a brief understanding of what the script does, I think I have enough to deobfuscate the blob. Since I cannot modify this script to make it cough up the prize, I can trick it into thinking that the script hasn't changed by making it read a copy of itself (I call this the "reflection technique").
Here's the two changes made to the beautified version.
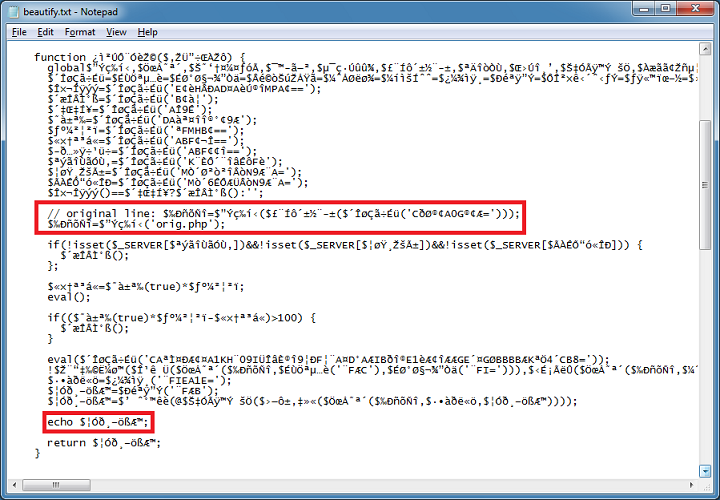
On the actual script or other PHPJiami scripts, all I do is search for strings that are at the end of the previous line which is ():''; Then put in the reference to the original script. From there, I search for "return" and put an echo there.
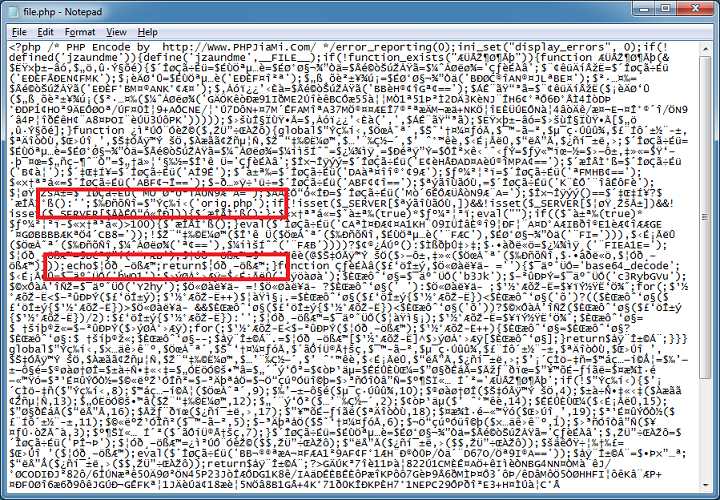
When the script is run, I get a result which looks something like this which doesn't mean too much.
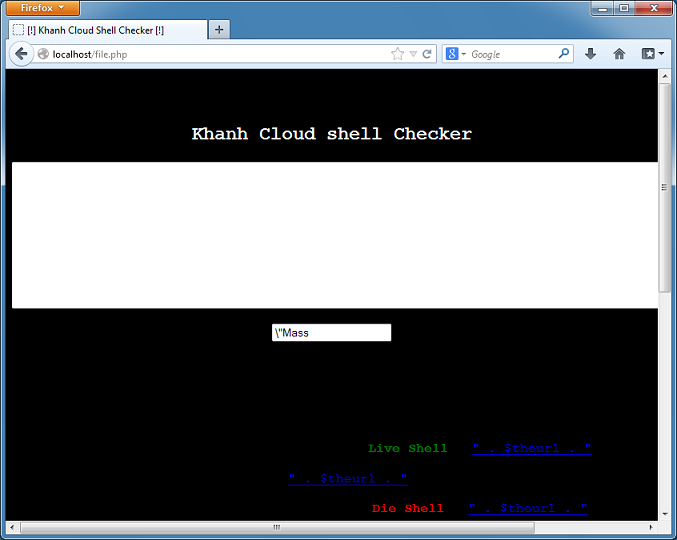
But when you view the source, you can see the original source code.
I just did a quick check to see if anyone else did a deobfuscation write-up and I came across this Chinese site.
It describes a few methods but one technique they offered caught my eye:
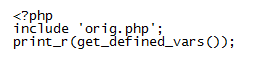
If you execute this, you get the deobfuscated script and it's so easy to do. Might even work on a bunch of other scripts too.
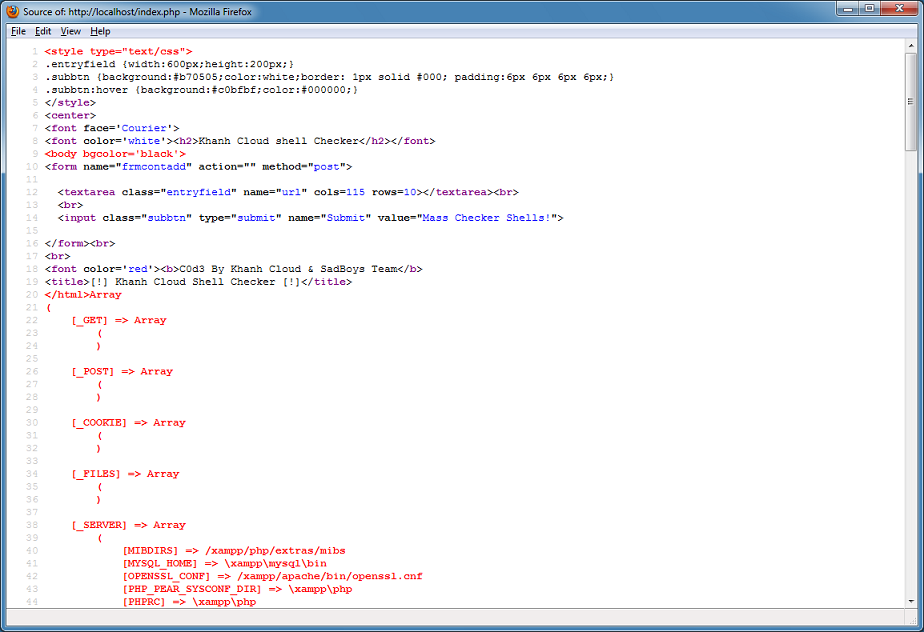
Scroll down to the very bottom and you'll see a long base64 string. If you decode this, you get the original script which is the same version I got using my, more difficult, reflection technique. Oh wellz.

Always nice to have multiple methods to use since their obfuscation method will probably be upgraded in the future.

