Cyber Exercise Tools
For the past two years, I've been involved with several cyber exercises and competitions from planning, training, as well as participating in them. I've written a dozen or so defensive and offensive tools for these cyber ranges. While there's better tools out there that do the same thing, I wanted to customize my own for the 64-bit environment and battle-test them to work out any bugs. Rules for some of these exercises and competitions state that any tool can be used as long as it's publicly available so that's why I'm posting some of the tools here.
Welcome Mat
This is a program for the blue team. It will try to listen on unused ports from 1 through 1024 where possible. The idea is to make it hard for the red team to figure out which services your server is running.
Here's what the tool looks like. You can only listen to up to 1024 ports at a time.
When the red team does an nmap scan, here's what it looks like:
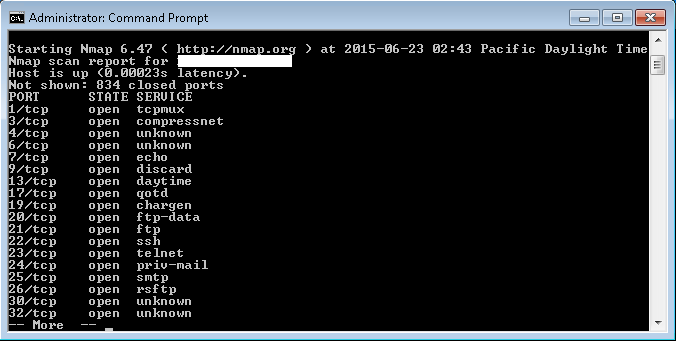
Experienced red teamers should be able to figure out which ports are truly open.
Cover Fire
During these exercises, it's hard to be slow and quiet since the blue team knows you're coming. You can do some misdirection here or launch a decoy there but it's hard to hide. This is a program for the red team. This will perform a series of random GETs and POSTs to specific webpages with a variety of user-agents. This should fill up the web server logs and make it challenging for the opposing side to figure out where your webshells are.
The program takes in a text file of hosts/IPs. The other text file it needs is the URLs to request. Sample files are included. You will need to spider your target website first and generate a list of URLs yourself.
Here's what the server logs look like when the tool is running. Can you find the webshell?
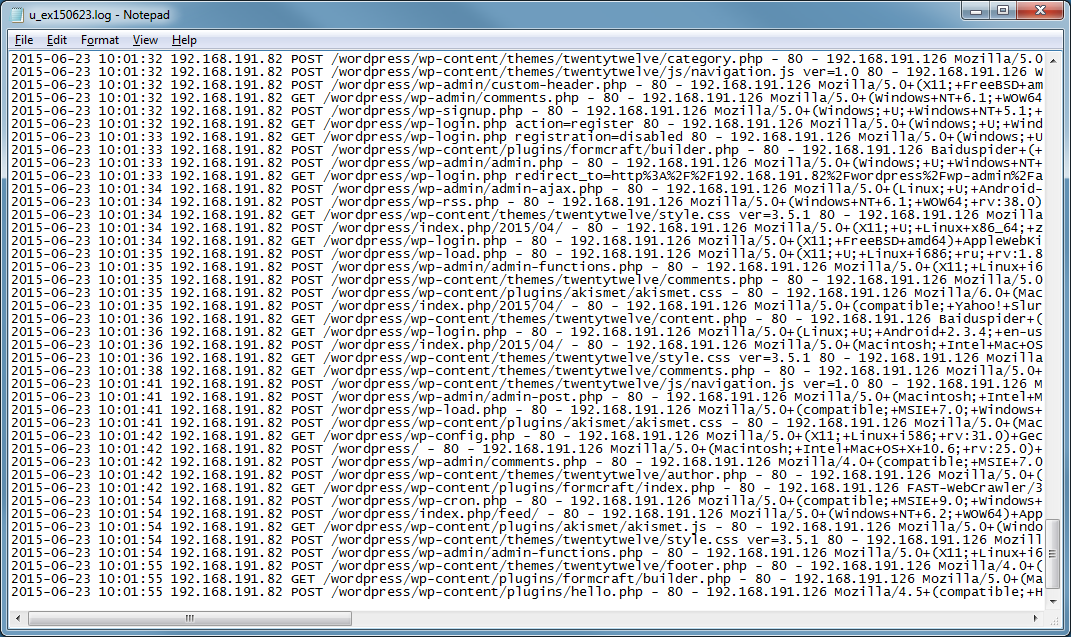
Blue team members who know their stuff should be able to find the webshell no matter if the logs contain a lot of noise.
Fake Defender Alert
This program attempts to fool the blue team member into granting it admin privileges. It uses the same privilege escalation trick implemented by Beta Bot. I added a screen-dimming feature to make it more convincing.

DeadDrop
I started off writing a portknocker program that sniffs network traffic to look for a keyword then open up a reverse or bindshell port but I found a better way to achieve the same goal. This program watches various ingress points on the server and executes commands it receives. This is done without using any listening port so monitoring netstat is useless.
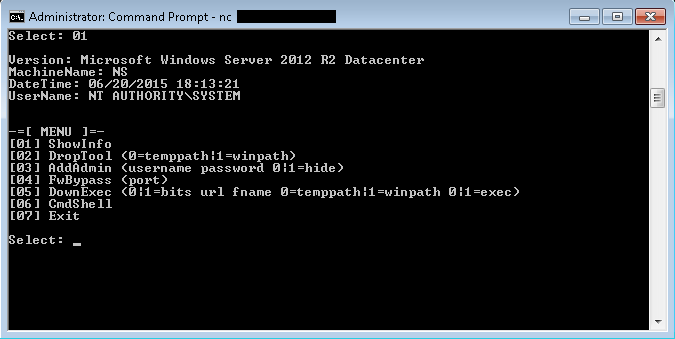
Backdoor Shell Menu
I wrote a reverse shell and during the exercises, I found myself doing the same commands over and over again. In order to be faster, I built capabilities directly into the shell program itself. Here's a screenshot of what the menu looks like. Instead of typing a series of commands manually, I just type the menu number plus some required parameters and I'm done.
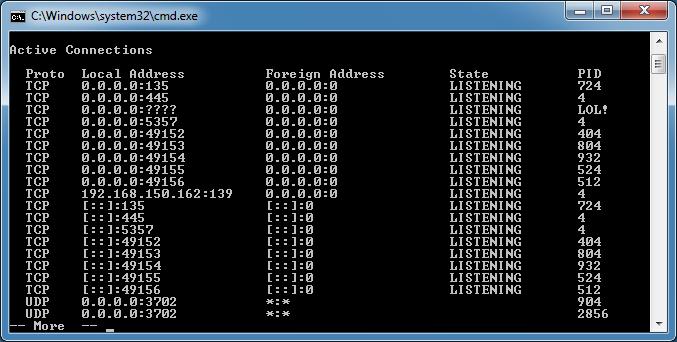
Netstat Interceptor
This program intercepts calls to netstat and can modify or remove anything related to the IP address, port, or PID of my choice. I can do the same thing to tasklist and taskkill.
Capture-The-Flag Jr.
Since I've been involved with CTFs lately, I started working on a capture the flag for kids. It's going to be pretty basic but the idea is to introduce them to various security concepts and get them familiar with security tools like a packet sniffer, hex editor, and Linux commands. It's going to be self-contained and portable so an instructor can run it in class and pass it to the kids to work on it at home.

For the time being, you can get the first two programs from the Tools page.

