Converter v0.3 Released
Here's another update based on some recent real-world analysis I've done as well as some of your requests and feedback.
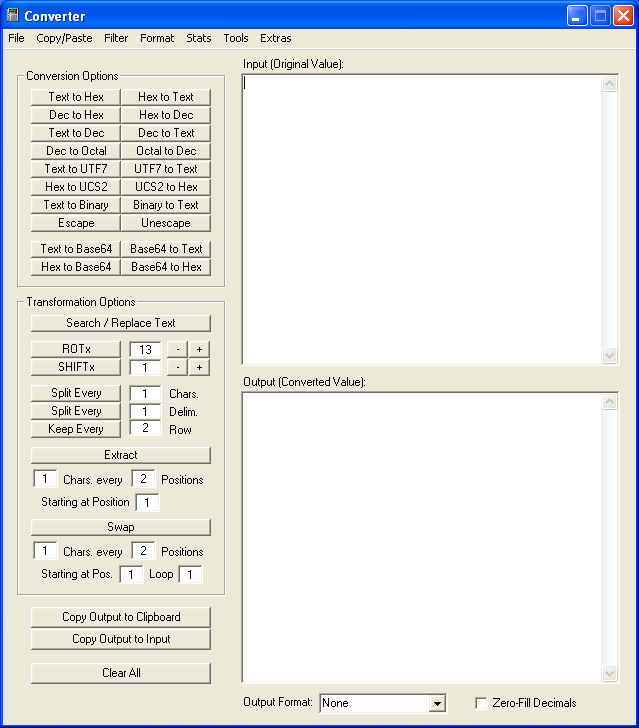
The first thing you'll notice is that I've increased the workspace as requested.
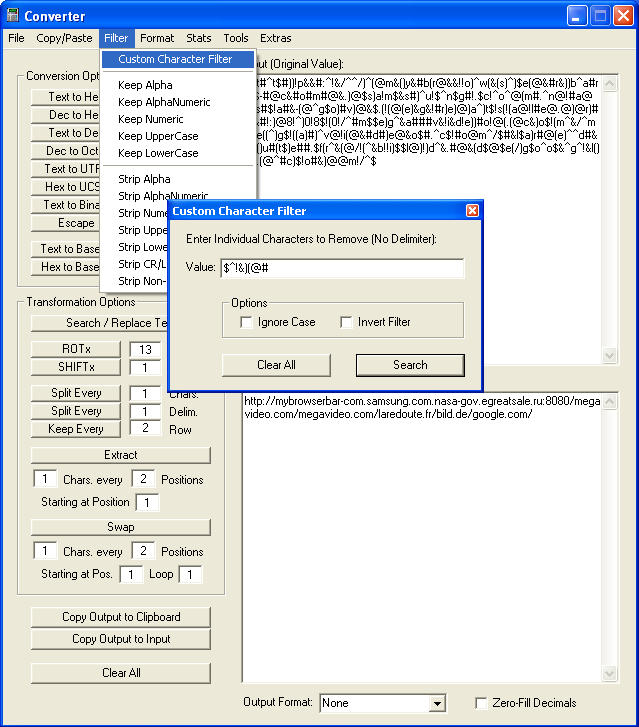
Custom Character Filter
Here's one example but you can find numerous variants via Google:
It's just a URL with garbage characters inserted between valid ones. This feature allows you to remove a string of single characters. Note: You can also use the "invert" option to keep the string of characters that match instead.
Multi-Pass Search
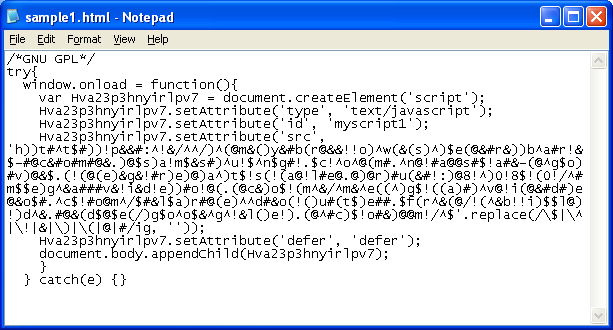
You might have seen this script on recent website compromises; it uses a convoluted method of character replacement.
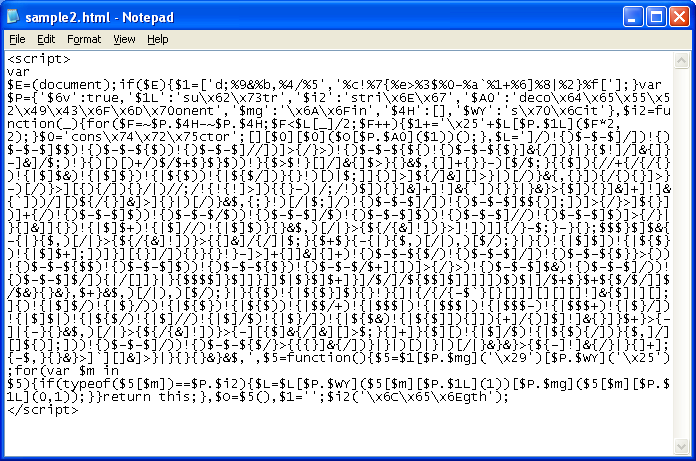
You can tackle this script in a couple of ways. One method is to manually search/replace each character but that takes time so I've added a way you can do multiple searches/replacements in one pass. Just make sure you use a unique character for your delimiter.
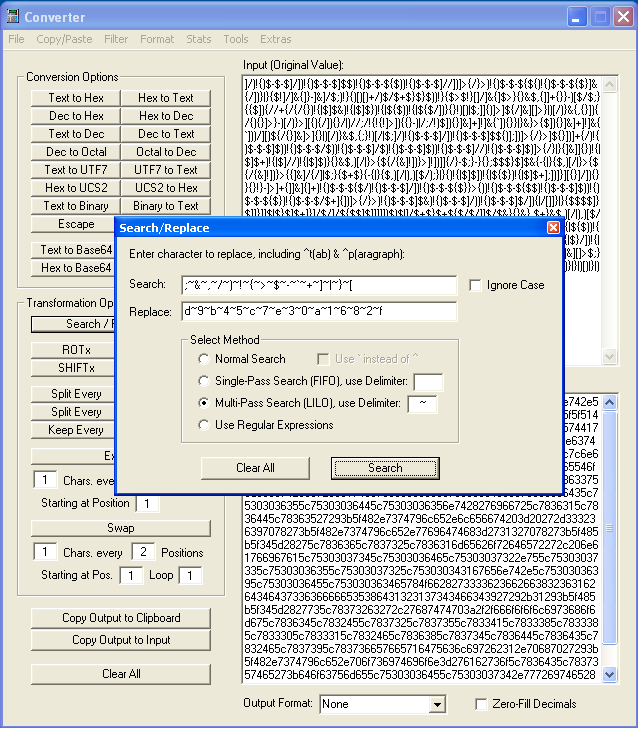
FIFO, "first in, first out", means that it will find the first match and ignore any other matches. LILO is "last in, last out" which means that the last match will be used. Here's a very simple example:
Method: Single-Pass (FIFO)String: "hello"Search: e,xReplace: x,zDelimiter: , (comma)Result: "hxllo"Method: Multi-Pass (LILO)String: "hello"Search: e,xReplace: x,zDelimiter: , (comma)Result: "hzllo"Under the File menu item...
Convert Binary File
You can read in a binary file and convert it to a hex file and vice versa. The output file will be written to the application's current path.
Convert Shellcode to EXE
If you encounter shellcode, you can convert that to an EXE file (credit to David Zimmer of Sandsprite). The file "shellcode.exe_" will be written to the application's current path.
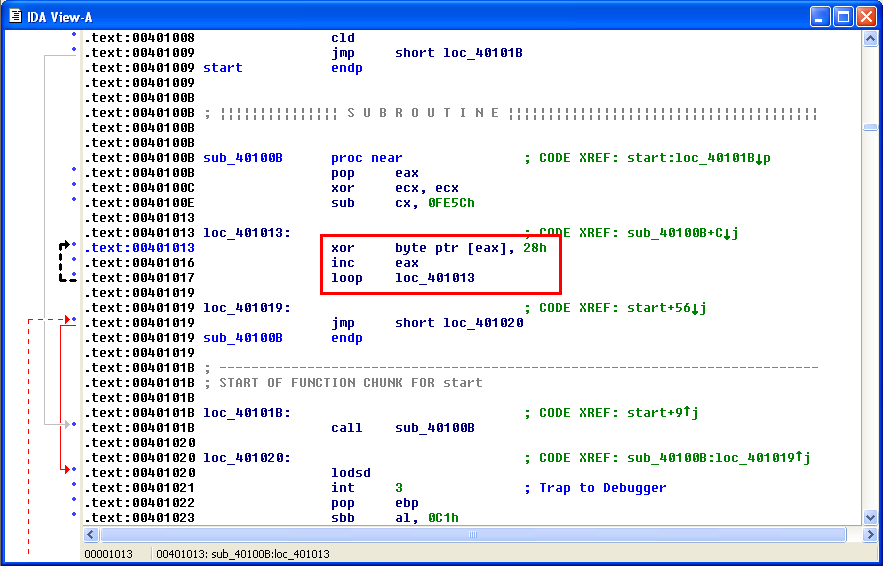
Now you can decompile/debug it using IDA or Olly. You can see the XOR decryption loop here (remember this for later).
Under the Tools menu item...
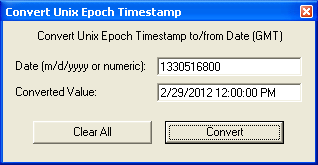
Convert Unix Epoch Timestamp
You can convert date/time to Unix Epoch and vice versa:
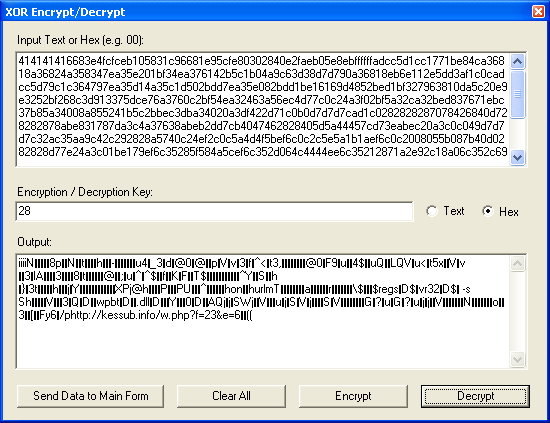
XOR Encrypt/Decrypt
You can now encrypt or decrypt content using XOR (credits to Sebatian L. and to James Johnston of TechKnow Professional Services. This program also contains cryptography software by David Ireland of DI Management Services Pty Ltd
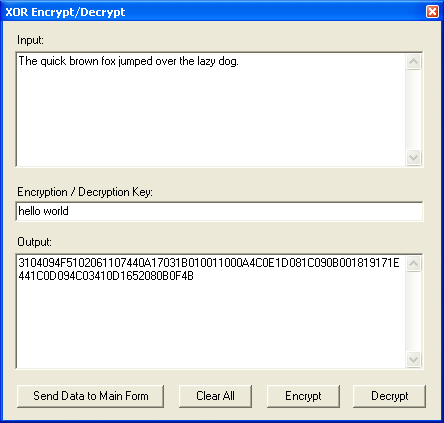
If you paste shellcode in hex, you can decrypt it if you know the key. Remember the example above? It uses the value of 0x28 to decrypt the shellcode, which is "(" in ASCII. You can use either values.