Clever Redirect to Impact EK
This malicious script was found on a somewhat popular website. Trying to find these things is like an Easter egg hunt. This particular one was clever in more ways than one. Here's the external script file that's hiding in plain sight on the webpage:

And the script itself was no ordinary redirect.
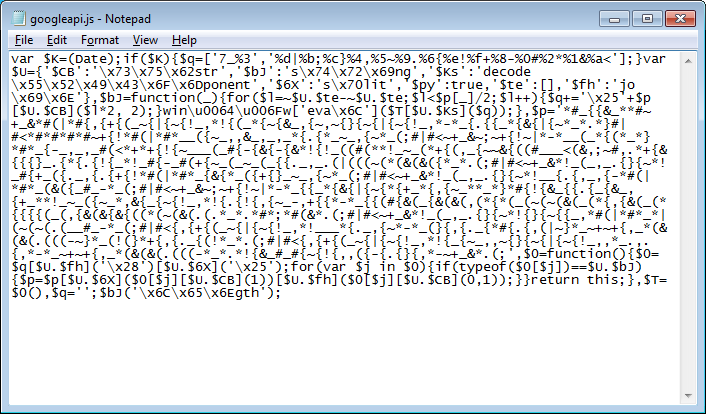
Here's a prettied-up version of the script. What the script is doing is a simple character substitution to convert those special characters into hex code. The hex code is then converted to text and eval'd. Of course it's doing it in the most obscure way.

Here's a very quick rundown of what it does. First it takes the value of the $q variable and converts it from this:
$q = ['7_%3', '%d|%b;%c}%4,%5~%9.%6{%e!%f+%8-%0#%2*%1&%a<'];To this. This is the substitution key:
$q = ['7_,3(,d|,b;,c},4,,5~,9.,6{,e!,f+,8-,0#,2*,1&,a<'];Then all it does is search/replace the value of the $p variable (the mess of symbols) by using the two characters separated by commas above. So it reads in "7" and "_" from q$ then it does a search for "_" in $p and replaces it with "7". Next it reads in "3" and "(", etc. Continue through the rest of $q.
To deobfuscate the script, simply make this modification:
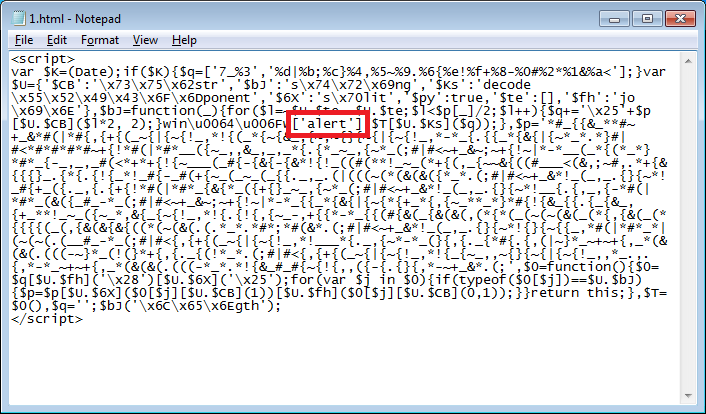
And the final result appears.

This leads to Impact Exploit Kit. You can find out more about this kit here:
http://malware.dontneedcoffee.com/2012/12/inside-impact-exploit-kit-back-on-track.htmlhttp://malwaremustdie.blogspot.jp/2013/01/lets-say-hello-to-impact-exploit-kit-w.html
