A Quick Peek at Network Injection
Like many of you, I've been looking at the various NSA document leaks to see what kind of tools and techniques are being used. I suppose these releases will give cybercriminals new ideas and we will see some of these put to nefarious use sooner than later.
This particular article was very interesting, especially the concept of network injectors. I've heard about EvilGrade (http://www.infobyte.com.ar/down/isr-evilgrade-Readme.txt) but never played with it. It seems as though QUANTUMINSERT and FinFly ISP do something similar.
I wondered how I could use this for a pentest. Getting inline with my target would be the first challenge. There are several tools I could use to route wired and wireless network traffic to my computer but maybe an easier way is to setup a proxy server then push out a proxy.pac file.
Here's a website with a link to a setup file for Revelo.
When the user downloads the program, I can see their GET request and response. At this point the program gets downloaded. Here we see excerpts from Paros.
The way QUANTUMINSERT is described to work, the download request gets silently redirected to another server where an implant gets downloaded. And according to the FinFisher documentation, there is a method called "INJECT-EXE" which "infects the downloaded EXE file in real time. The agent is installed when the target runs the EXE file."
There's not too much details so I can only infer how this is being done. Maybe they would have pre-downloaded popular programs, binded it with a backdoor, then sent the file over via a forged HTTP redirect. This would allow the user to install the real program with real certificates but have their program run too.
But how could you do this in real-time, with any download? If I can write a program that intercepts the GET request to any EXE program, bind it with a backdoor in real-time, update the Content-Length field in the response header, and send the file along...it *should* work. ;)
After some coding, I came up with "Interjector" - Interceptor and Injector (because of the nature of this program I won't be making this available, sorry). There's not much to look at I know.
With Interjector off, when I download the file, it looks like this:
However, when Interjector is running, the same download dialog box now looks like this (note the file size):
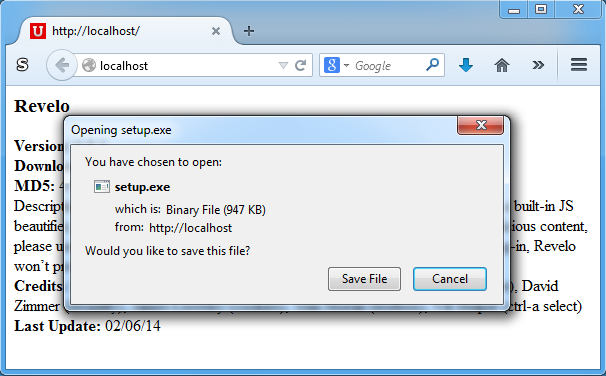
What's happening behind the scenes is that there is a specially-crafted EXE file that's been added to Interjector as a resource. When the program sees a GET request to any EXE file, it loads the resource to a variable and gets ready. When the program sees the response, it reads in the Content-Length value, adds the length of the resource to it, and puts the updated value back into the header. Finally, it injects the variable containing the resource into the download stream.
The advantage of doing it this way is that I don't need to redirect users to another server, I can intercept/inject any EXE file the user downloads, it's very stealthy, and all of this happens in real time.
Here's what it looks like when the downloaded file is executed:
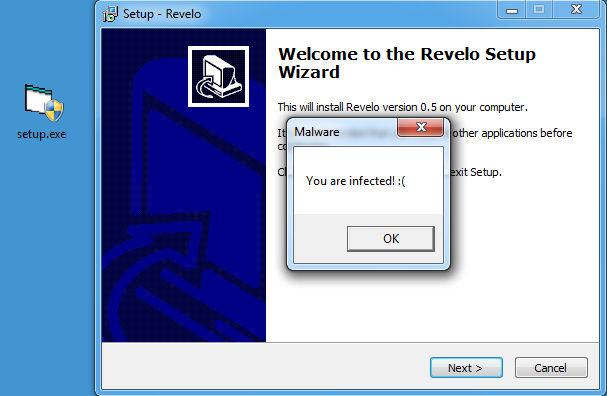
Ugh, the icon makes it look fake but I can fix that. This is going to be a challenge for those programs with unique icons. The best way is probably to use a generic icon like this and hope users don't notice.
What about the MD5/SHA hash? That's the biggest hurdle to overcome. I could change the hash on the webpage to match the final file but only for the ones I know about by doing a global search and replace. Or I can search for any hash line and remove it from the webpage.
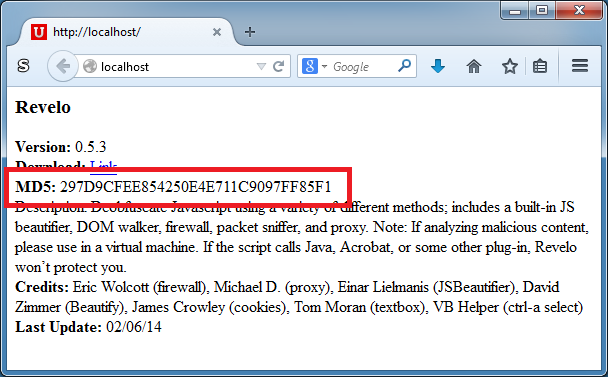
What if it's a compressed file download (e.g. ZIP)? I think I would have to rezip the file with a new EXE or rebuild the download which changes the ZIP file to an EXE. The real-time requirement makes this difficult to handle without the user taking notice.
So what's a user to do?
- Use HTTPS to download programs
- Choose to download a compressed version (e.g. ZIP) instead of a bare EXE/MSI file
- Pay attention to any anomalies and inconsistencies; when in doubt, stop
- Verify the program's hash before installing (for the paranoid, use an out-of-band device like your phone to view the hash on the webpage)

